User activity tracking in WordPress is an essential security measure for website administrators. It serves as a deterrent to malicious behaviour, and a means of identifying and resolving security incidents.
Cybercriminals use various tactics in their attempts to hack into websites. Unauthorised access allows a hacker to change user permissions, access sensitive data, add harmful backlinks, or delete content.
Activity tracking can detect signs of suspicious behaviour by empowering site owners to understand regular user patterns and spot anomalies as they occur. Tracking also maintains an activity log for compliance or legal purposes, and helps admins understand how users are interacting with their site – useful for improving the customer experience.
However, managing complex user logs, staying alert to breaches, and handling bad-bot traffic present significant challenges for all site owners. Here we’ll detail the best solutions for implementing user activity tracking. We’ll also take an in-depth look at identifying suspicious activity and the best steps to follow should a security breach occur.
Best plugins for user activity tracking in WordPress
Few WordPress users have the programming know-how to build their own user activity monitoring tool, making a plugin the best solution. Fortunately, some hosting providers include tracking tools, and there are many plugins expressly designed for the purpose. Here’s the pick of the bunch!
Shield Security PRO

Shield Security PRO is a leader in user activity tracking for WordPress. The platform features real-time monitoring, automated security responses, and advanced reporting. Members gain a comprehensive toolkit for WordPress security, from activity monitoring, traffic logging, and bad bot protection to spam filtering and two-factor authentication.
Using its exclusive Snapshot Technology, Shield Security PRO can track changes to WordPress components, made either via the WordPress site directly, or external changes such as direct database manipulation. ‘Snapshotting’ is a logging mechanism not typically found in other security plugins.

Using a comprehensive security plugin like Shield Security PRO brings huge value to any website. It provides a window into WordPress activity that goes far beyond simple page viewing statistics.
Jetpack
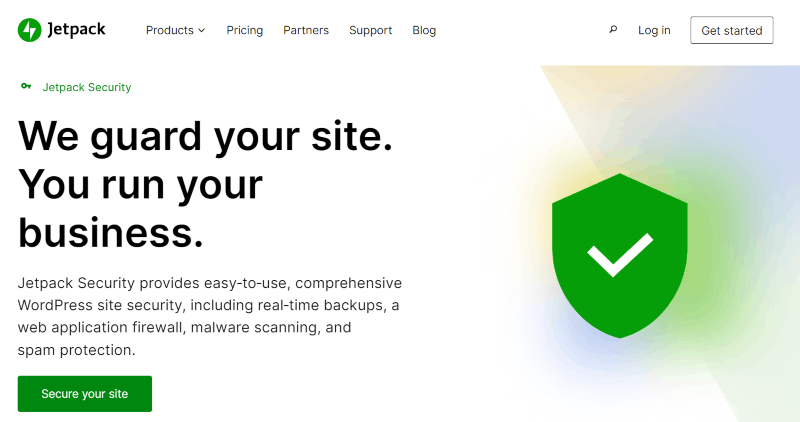
Jetpack’s activity log helps administrators manage and monitor changes on their WordPress sites. It records various core WordPress activities, including user logins, post publications, and plugin installations. This log provides detailed information for each event, such as timestamps and user actions, assisting in troubleshooting and site management.
Access to the activity log is tiered based on the user’s subscription plan. Users on the free plan can view the 20 most recent events. Paid plans offer extended access and filtering options to tailor the log view according to specific needs and time ranges.
Jetpack also includes a firewall, spam protection, and malware scanning. You can explore additional features on Jetpack’s activity log feature page.
Activity Log
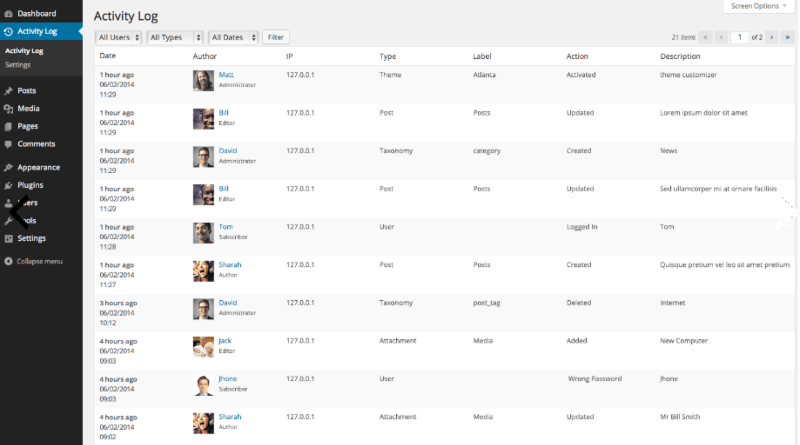
The Activity Log plugin is a free solution for monitoring user activities within the WordPress dashboard. It’s easy to use and has minimal impact on site performance as the data gathered is stored on a separate database.
Additionally, the plugin provides the tools needed to help site owners manage GDPR compliance, including the export/erasure of data. For a record of every action taking place in the WordPress admin area, it’s an excellent free resource, although limited in scope.
What to look for when tracking user activity
Suspicious activity comes in multiple forms, often indicating security threats such as unauthorised access, data breaches, or automated attacks. Here are some key signs of activity to monitor:
Unusual access patterns
- Abnormal login times: Logins at odd hours that don’t align with normal user activity patterns may suggest unauthorised access.
- Geographical irregularities: Logins from geographical locations that are inconsistent with a user’s typical location can mean an account has been compromised.
- Multiple failed login attempts: Repeated failed attempts can be a sign of brute force attacks, with hackers using bots in an attempt to guess passwords. It could also be a signal that users are struggling with some element of the login process and it might help to assess this and reach out to users to see where the trouble may lie.
Anomalies in user behaviour
- High volume of activity: An unusually high rate of requests or actions in a short period can indicate automated scripts or bots.
- Unusual navigation patterns: Rapid and illogical website navigation may suggest the use of automated tools. Shield Security PRO monitors such patterns when looking out for bad bot signals, particularly when the visitor triggers 404 errors.
- Sequential or repetitive actions: Genuine human users are unlikely to perform the same action over and over again, suggesting automated bot behaviour.
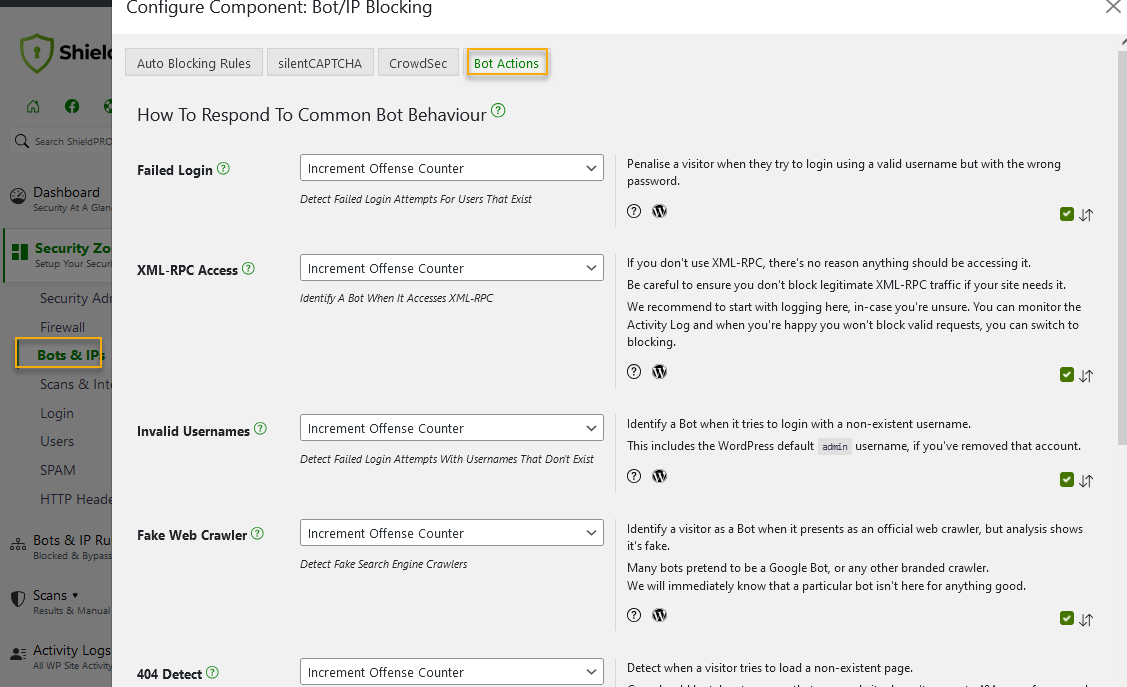
Account and data manipulation
- Unexpected changes in user profiles: Random changes to user profile information like passwords or contact details can suggest account takeovers.
- Unusual data download or upload patterns: Significant data uploads or downloads that deviate from normal behaviour patterns are another sign that an account has been compromised.
Uncommon request types
- Suspicious request formats: HTTP requests that contain unusual patterns or structures might be probing a site for vulnerabilities.
- Use of uncommon user agents: Requests made from rare or mismatched user agents might indicate attempts to disguise a malicious source.
Signs of automation
- Simultaneous logins: Accounts accessed simultaneously from different locations may indicate that login details have been compromised and are being used by multiple individuals.
- Script-like interactions: Rapid, precise, and repetitive interactions suggest the presence of a script or a bot, rather than a human user.
File and system access anomalies
- Access to sensitive files: Unauthorised attempts to access sensitive files or directories can be a bid to steal data.
- Modification of system files: Unauthorised changes to system files or configurations can indicate malware, or a hacker attempting to escalate their access levels.

How to troubleshoot when you spot red flags
When site owners detect suspicious behaviour in their user activity log viewer, immediate action needs to be taken to stop potential threats. Here are the recommended troubleshooting steps:
1. Verify the activity
- Confirm any suspicious entries: Double-check your log entries to confirm whether they are suspicious, or potentially the result of unusual – but legitimate – user behaviour.
- Contact the user: If possible, contact the user associated with any abnormal behaviour. Even very odd occasions may have a logical explanation, removing the need for further investigation.
2. Analyse the logs
- Identify patterns: Look for patterns that indicate threats, such as repeated failed login attempts, unusual access times, or logins from unexpected locations.
- Use log analysis tools: Use tools designed for analysing logs to sift through large volumes of data and highlight anomalies. Shield Security PRO’s management tools monitor activity, traffic, user sessions, and IP addresses, covering all possibilities.
3. Contain the threat
- Isolate affected systems: If a threat has been identified, prevent it from spreading by isolating that system from the wider network.
- Change passwords: Immediately change passwords for any accounts that show unusual activity.
- Implement access controls: Restrict access rights for suspicious accounts until the situation has been clarified, or the security threat resolved.
4. Increase monitoring
- Escalate your surveillance: Temporarily increase monitoring of the affected systems to catch further suspicious activities.
- Set up alerts: Configure alerts for further activities such as new login attempts, changes to user permissions, or access to sensitive data.
5. Investigate further
- Use forensic tools: Employ forensic tools like NetworkMiner to analyse the depth of the intrusion and understand how the breach occurred.
- Review connected systems: Check other systems connected to the affected systems to ensure they have not been compromised.
6. Report and respond
- Notify relevant parties: Inform everyone affected by the breach, including users, your IT team, and, if necessary, legal authorities. A swift, comprehensive, and transparent response is the best approach to containing and resolving any security issue.
- Follow your incident response plan: Your organisation should have a well-rehearsed incident response plan, including steps for containment, removal, recovery, and protection from future data breaches.
7. Prevent future incidents
- Update security measures: Based on your investigation’s findings, implement stronger security measures. These might include updating firewalls, using multi-factor authentication, upgrading security software, and regularly training employees.
- Schedule regular audits: Conduct regular audits of system logs in future, to detect early signs of suspicious activity before they escalate.
8. Documentation
- Document the incident: Keep detailed records of your incident response process, relevant decisions made, and outcomes from your investigation. This documentation can help in legal situations and may prevent future incidents.
Get started with Shield Security PRO for robust WordPress protection
For WordPress site owners seeking to tighten their website security, Shield Security PRO is a premium choice as it not only monitors all site activity but also provides proactive threat prevention across your entire site.
As previously stated, the platform’s activity log section discovers requests made from both users & visitors, but also changes made directly that have bypassed loading of the site directly. With Shield Security PRO, nothing gets missed. Detailed logs and alerts allow administrators to identify suspicious activities as they occur, affording you the opportunity to respond proactively to potential risks.
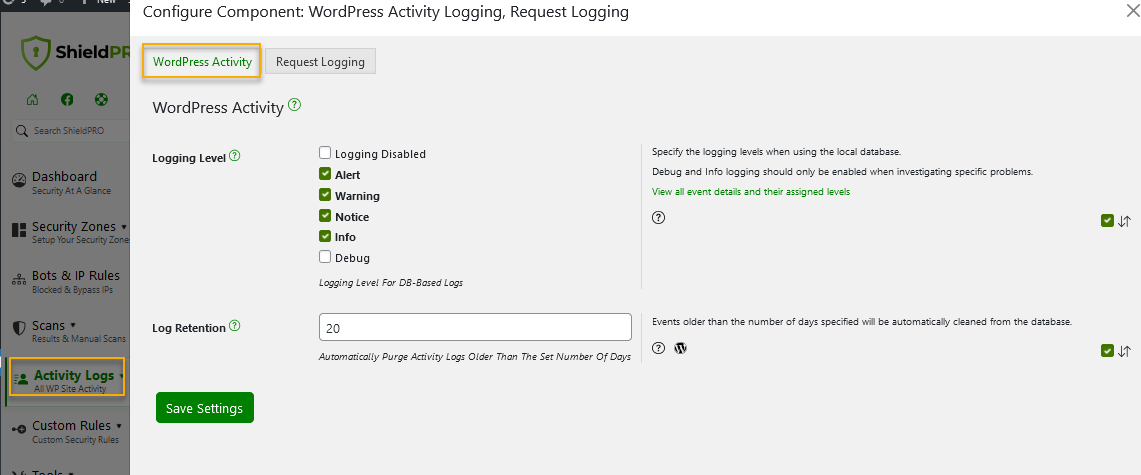
Key security features
Beyond activity tracking, Shield Security PRO is adept at blocking bad bots, a significant source of security threats. The silentCAPTCHA AntiBot system ensures that only legitimate traffic reaches your site, improving both security and performance.

DDoS protection limits suspicious traffic rates, which can drain server resources and slow down your site. A powerful malware scanner stops access attempts at the gate, and spam protection identifies unwanted comments from humans and bots. You’ll also have access to set up advanced two-factor authentication, which provides further defence against hacking attempts. And that’s not all! A comprehensive list can be found on our Complete Features page.
Instant alerts
The plugin also includes Instant Alerts, notifying site owners of all critical security events occurring on their WordPress site. These include:
- Admin account changes: If an admin account is created/deleted, has its access rights promoted/demoted, or its password/email changed, an alert is instantly sent. Snapshot technology detects changes made through the dashboard, Application Programming Interface (API), or any other means.
- Vulnerabilities: Site owners are instantly notified whenever a vulnerability is discovered. You’ll also receive notice via the plugin’s standard Alert Reporting feature.
- Plugin deactivation: If your Shield Security PRO plugin is deactivated, you’ll receive an email notification. This includes a timestamp, request path, the user responsible, and their IP address.
- FileLocker changes: The FileLocker feature secures your index.php, wp-config.php and .htaccess files against hacking and tampering. Any changes made trigger an instant alert, along with a notice through the plugin’s regular reports.
An automated security tool is a must-have investment for anyone focusing on growing revenue and expanding their brand. For a complete solution, get started with Shield Security PRO today!

