Websites are not just platforms for content, but gateways for communication. Contact forms play a pivotal role here. They serve as bridges connecting your WordPress website to the outside world, funneling in leads, building your mailing list, and enticing visitors to return to your site.
However, while immensely beneficial, contact forms attract their fair share of woes, primarily in the form of spam. This unwanted interference is a nuisance and can significantly disrupt the efficiency of your business.
In this article, we will explore:
- Five effective methods to protect your WordPress website from the relentless waves of contact-form spam.
- Beginner-friendly and secure strategies to enhance your site’s integrity without compromising user experience.
- Different ways in which Shield Security PRO can protect your website without much effort from your side.
Understanding contact form spam in WordPress
Contact form spam is the submission of useless or malicious content through a website’s contact form by spammers (individuals or, more frequently, bots). This content often appears harmless but carries hidden agendas for nefarious activities, such as:
- Disruption: Sometimes, the intent is simply to disrupt the site’s normal operation, or to overload the website owner with useless information, either as a form of harassment or to detract from the website’s usability and effectiveness.
- Search Engine Optimization (SEO) manipulation: Spammers often include links to their own or their clients’ websites in the hope of improving search engine rankings through increased backlinks. This is based on the outdated belief that more links to a site can improve its SEO performance, though modern search engines are adept at identifying and penalizing such tactics.
- Phishing scams: By sending messages that appear legitimate, spammers can trick recipients into revealing sensitive information like passwords, credit card numbers, or other personal data. This is a more malicious form of spamming, as this sensitive data can then be used for fraud or identity theft, or be sold on the dark web.
- Malware distribution: Some contact form spam includes links to malicious websites, aiming to infect users’ devices with malware, ransomware, or viruses.
- Unethical lead generation: In less moral marketing practices, spammers collect email addresses and other contact details from replies to their spam messages, which are then used for further marketing or sold to third parties.
Sadly, regardless of size, popularity, or niche, any site with a contact form is a potential target, and the consequences can be serious.
Contact form spam’s impact on your business
Yes, spam is downright annoying. That’s the immediate reaction any site owner has when their inbox gets flooded with irrelevant spam emails through contact forms. But the problem runs deeper:
- Inbox clutter: The constant influx of spam clutters your inbox and can cause you to miss important messages from potential clients or partners. This can directly impact your business relationships and opportunities.
- Productivity drain: Dealing with spam can be a significant time sink that can disrupt your workflow and make you less productive. Time spent deleting spam is time taken away from growing your business or engaging with real customers.
- Lost leads: In the chaos of an overwhelmed inbox, leads can easily slip through the cracks. A potential customer’s inquiry might get buried under spam, leading to missed opportunities and a potential loss of revenue.

5 methods for reducing WordPress contact form spam
1. Blocking suspicious bots
Firstly, it’s important to understand that not all bots are malicious. Some, like search engine crawlers, play a beneficial role. However, spam bots are a different breed. These bots are programmed to find and fill out contact forms en masse, often with the same repetitive, spam-y message, regardless of its relevance or the website’s context.
The good news is that blocking these bots can significantly reduce and stop spam coming through your contact form. This is where security and anti-spam plugins, like Shield Security PRO, come into play.

These tools are designed to identify and block bots from accessing your site, thereby cutting off the spam at its source.
A core feature of Shield Security PRO is the AntiBot Detection Engine (ADE), which is specifically designed to differentiate between genuine human traffic and automated bot traffic. By analyzing various signals and behaviors, the ADE can effectively block bots without hindering the experience of legitimate users.
Once you install Shield Security PRO on your WordPress site:
- Navigate to the plugins dashboard from your WordPress admin panel.
- Go to Config > Bot Blocking > AntiBot System and adjust the security settings to your desired level of protection.
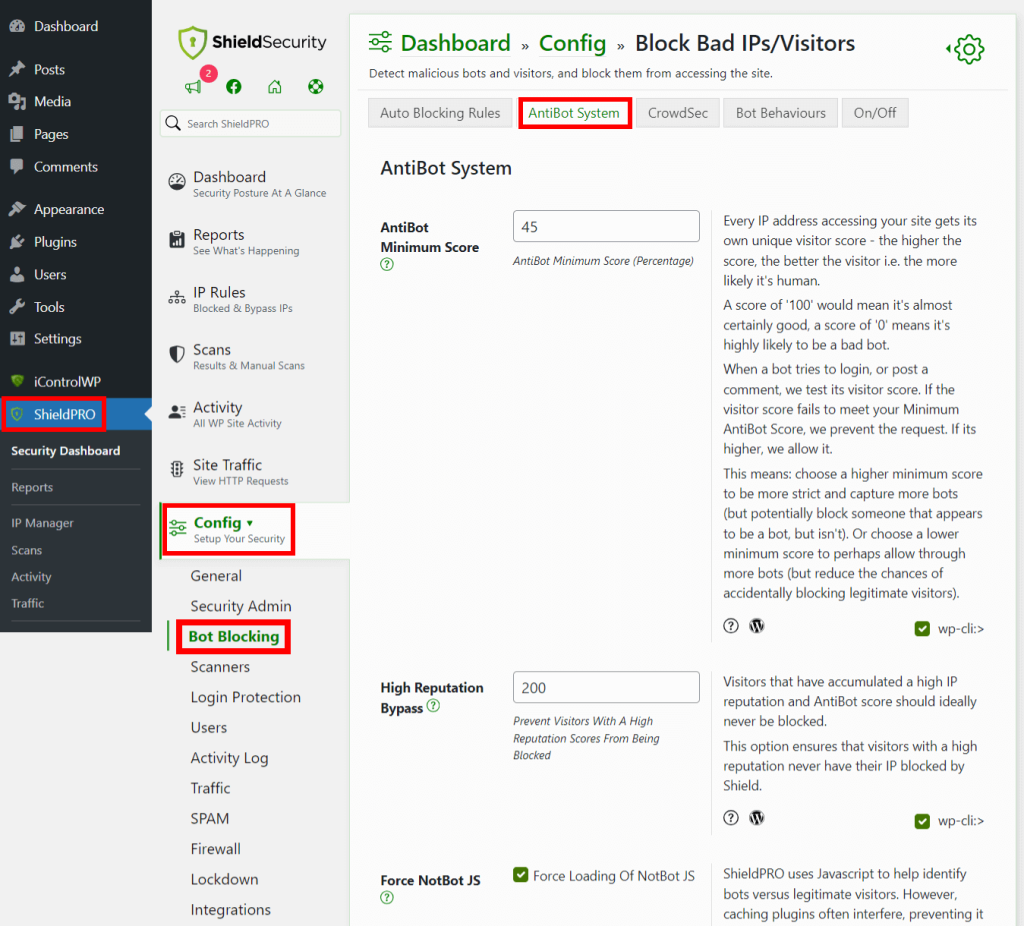
- Navigate to Config > SPAM > Bot SPAM and make sure the ADE is enabled.
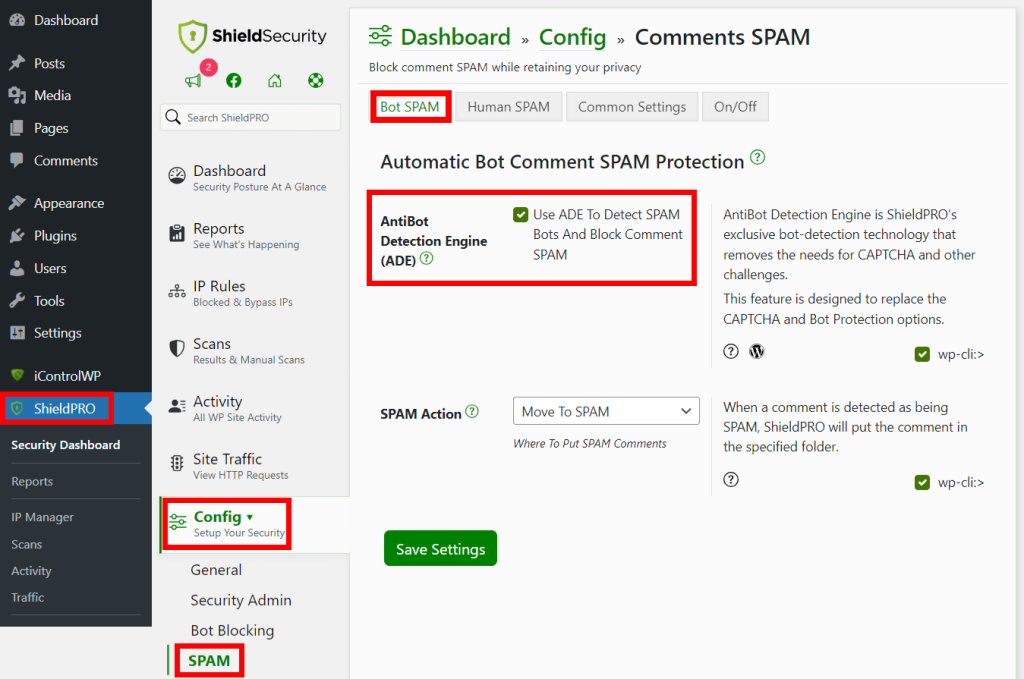
- Select the desired action to be taken when spam is detected.
And that’s it – that’s how simple Shield Security Pro makes blocking suspicious bots. Without the constant bombardment of bot traffic, your site can run more efficiently, and you can save your resources for legitimate users. You’ll also reduce your site’s exposure to a variety of other threats, such as brute force attacks or vulnerability probing.
2. Train your team to spot spam
Even with bots out of the picture, human spammers can still fill out your forms with malicious links and useless information. That’s why it’s important to train your team to be able to spot suspicious messages (whether from your contact form or any other source). Your security approach is only as strong as the weakest link in the system: If everyone on your team can spot spam a mile away, you’re much less vulnerable.
Here are a few signs of spam messages to teach your team members to watch out for:
- Message has links: Although there are certainly legitimate reasons for users to provide a link when they fill out a contact form, you should always view links with a level of suspicion. Don’t simply click links in messages; instead, double-check that the link goes where it looks like it goes. It’s easy to make a link look like it’s going to a legitimate site – say, a Facebook page – when it’s actually going to a false site, such as a spoofed Facebook login screen.
- Irrelevance or non-specificity: Often, a message will obviously have nothing to do with your business or product. This is the easiest spam to spot. However, sometimes, the messages are so vague as to apply broadly to nearly any recipient. This isn’t a clear sign of spam on its own, but if it’s paired with other red flags, you should be suspicious.
- Heavy typos or grammatical errors: Spam messages often contain lots of spelling errors, typos, and grammatical mistakes. This isn’t because spammers don’t use spell check: It’s actually done intentionally. Spammers want to avoid the people who would be likely to notice these mistakes, because they’re typically people who are more savvy and, as a result, harder to scam. Train your team to be wary of these kinds of errors, and you’ll make yourself an unattractive target.
3. Setting up a honeypot
A honeypot in cybersecurity is a decoy meant to attract attackers so their malicious activities can be identified and blocked. It is a computer system that appears to be part of a network but is actually isolated and monitored. It’s designed to look attractive to attackers, often by appearing to contain valuable or vulnerable data.
When it comes to contact form spam, the honeypot technique exploits a fundamental characteristic of bots: their tendency to fill out every field they come across.
A honeypot adds an invisible field to the form that is not visible to regular users but can be detected by bots. When a bot fills out this hidden field, it reveals itself as spam – after all, a human user wouldn’t be able to see or interact with this hidden field.
You can use the honeypot as a filter, flagging submissions that trigger it for further review, which will allow you to manually assess whether they’re genuine or spam. Alternatively, you can set your system to automatically discard any submissions flagged by the honeypot to streamline the process and keep your inbox free from bot-generated spam.
If you’re using contact form plugins like Contact Form 7, the process of integrating a honeypot into your WordPress website is straightforward. Here’s a general overview of the steps:
- Go to the contact form plugin section in your WordPress dashboard. Either create a new form or edit an existing one.
- In some plugins, you can add a honeypot by inserting the shortcode [honeypot your-honeypot-name] into your form template. Replace your-honeypot-name with a name of your choice (make it look like a regular field name, but one that you will not use elsewhere).
- Some plugins allow you to customize the honeypot field’s behavior and appearance (to keep it invisible to actual users).
- After adding the honeypot field, save your form and place it on your website.
If that seems too technical and complex, you can use a honeypot plugin instead, and it’ll take care of it for you.
4. Rate limiting
Rate limiting works on a straightforward principle: it sets a cap on the number of times a user (or an IP address) can submit a contact form within a specific period. This approach is based on the observation that while legitimate users submit forms at a normal, human pace, bots and spammers tend to do so at a much higher frequency.
To implement rate limiting, you define limits on how often submissions can be made. For example, you might decide that a single IP address can only submit a form once every minute. If another submission is attempted from the same IP within that minute, it’s automatically flagged or blocked.
Shield Security PRO makes this super easy. Just navigate to ShieldPro > Config > Traffic > Traffic Rate Limiting from your WordPress admin dashboard and configure the setting to your preference.
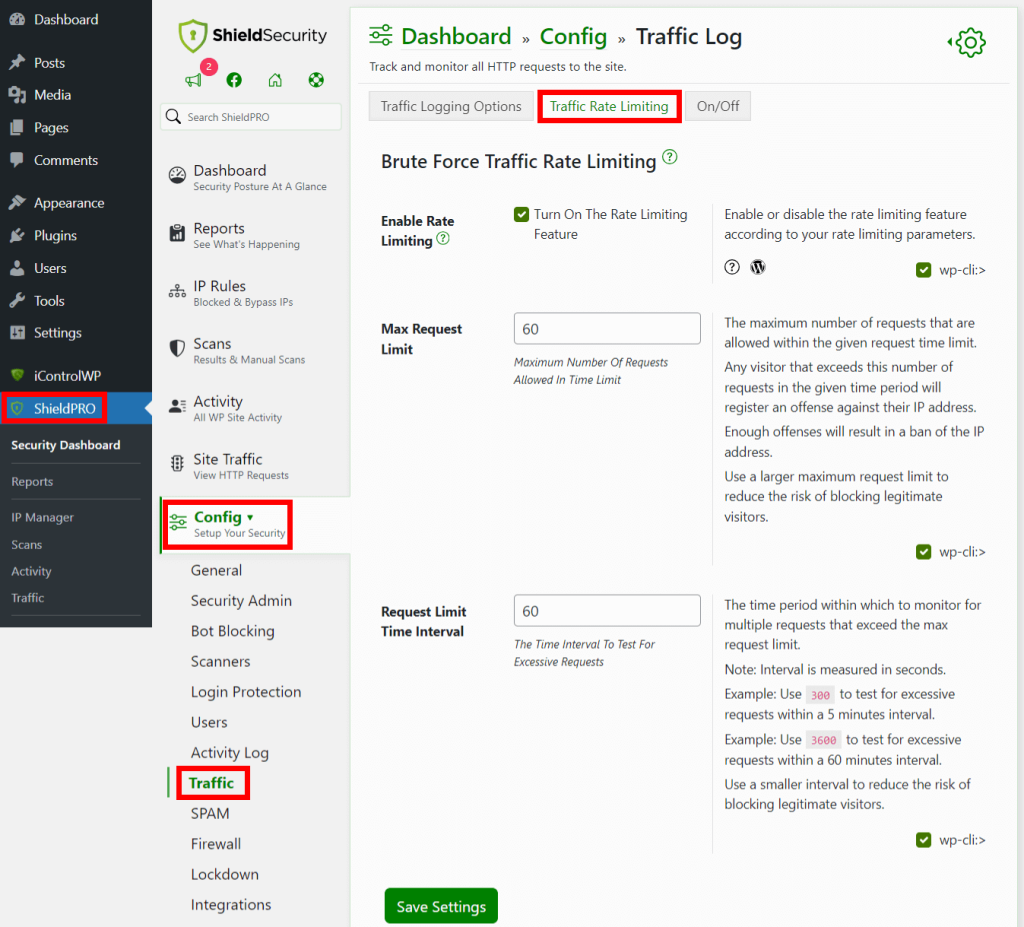
It’s important to find the right balance when setting up rate limiting. Set the limits too low, and you risk frustrating genuine users; set them too high, and you may not effectively deter spammers. The key is to monitor and adjust as necessary to ensure your rate limiting effectively provides spam protection while keeping your site user-friendly.
5. Using a Google reCAPTCHA or CloudFlare Turnstile
reCAPTCHA, developed by Google, is a widely recognized system used to verify whether a user is human. It presents challenges that are easy for humans but difficult for bots, such as identifying objects in images or simply clicking a checkbox to confirm they’re not a bot.
CloudFlare Turnstile is another solution that serves a similar purpose but with a different approach. It’s designed to be less intrusive, providing a smoother user experience while still effectively filtering out bots. Unlike traditional CAPTCHAs, Turnstile operates mostly in the background, assessing user behavior and other signals to verify if the user is human.
Incorporating either reCAPTCHA or CloudFlare Turnstile into your WordPress site’s contact forms is a smart move to significantly reduce spam while maintaining a positive user experience. Here’s why:
- Enhanced security: Both reCAPTCHA and CloudFlare Turnstile add an additional layer of security, effectively blocking a significant portion of automated spam.
- Flexibility: You can choose the tool that best fits your site’s needs and your users’ preferences, whether it’s the more interactive reCAPTCHA or the seamless experience of Turnstile.
- Ease of implementation: Integrating these technologies into WordPress contact forms is generally straightforward, with various plugins and tools available to facilitate the process.
That said, it’s worth noting that if you have Shield Security PRO, the ADE can detect bots without disrupting the user experience at all. Many users get annoyed at needing to prove their humanness, but with the right plugin, they don’t have to prove a thing.
Boost your website’s performance and safety with ShieldPRO
As we’ve explored throughout this article, protecting your WordPress site from contact form spam is both a necessary and multifaceted task. The journey towards a spam-free website is about enhancing security and creating a better experience for you and your users.
With the tools and strategies discussed in this guide, you’re well-equipped to protect your site, enhance its performance, and provide peace of mind for yourself and your visitors.
Shield Security PRO stands as a robust ally in your cybersecurity efforts. Offering features like an integrated vulnerability scanner and advanced spam detection tools, Shield Security PRO is designed to fortify your WordPress site against an array of digital threats easily, including contact form spam.
Make Shield Security PRO part of your WordPress website defense arsenal today and secure the peace of mind that comes with a well-protected online presence!


