Backdoors are a silent menace lurking in compromised WordPress sites, granting hackers ongoing access even after security fixes have seemingly been applied. These malicious entryways often masquerade as legitimate files or hide within existing code, making them a challenge to detect.
Hackers typically exploit vulnerabilities in plugins, themes, or core files to install these covert backdoors. The urgency of identifying and removing backdoors cannot be overstated; every moment they remain in-place puts your site at risk of further damage.
This guide will equip you with the knowledge to recognise, eliminate, and prevent backdoor threats, ensuring your WordPress site’s long-term security through proactive protection.
Risks of backdoors on your WordPress site
The consequences of backdoor exploitation can be severe, far-reaching, and enduring:
- Data theft: Backdoors allow unauthorised access to sensitive user data, including personal and financial information. This breach can lead to identity theft and financial fraud, potentially exposing your business to legal consequences.
- Website defacement: Attackers can alter your site’s appearance and content, replacing your brand image with offensive or malicious material. Such damage to reputation and user trust often persists even after restoring the original content.
- Malware distribution: Your compromised site may be used to spread malicious software to visitors, including hosting phishing scams. This harms users and risks your site being flagged as a security threat, further damaging your reputation.
- SEO damage: Search engines may blacklist compromised sites, resulting in a significant loss of organic traffic and visibility. Recovery can take months, even after resolving security issues, with long-lasting impacts on your site’s credibility.
- Server overload: Attackers often exploit backdoors to misuse your server resources, leading to decreased site performance, slower load times, and potential downtime. This can result in frustrated users, harm to business operations, and additional costs for metered hosting plans.
Recent incidents underscore the persistent threat of backdoors. In 2023, a massive attack compromised over 17,000 WordPress sites, exploiting vulnerabilities to inject malicious JavaScript. In the same year, a critical backdoor was discovered in radio technology infrastructure used by emergency services and utilities across 100 countries.
These cases demonstrate that no sector is immune to backdoor threats, from individual websites to critical national infrastructure.
Where are backdoors hidden? Exploring common locations in WordPress
Backdoors in WordPress can be cunningly concealed. This section will guide you through typical hideouts favoured by attackers so you can direct your attention and resources accordingly.
Themes and plugins
Themes and plugins are prime targets for backdoor insertion, especially when outdated or poorly maintained. Hackers often exploit vulnerabilities in older plugins to gain unauthorised access, and then inject malicious code into these files.
Signs of compromise include unexpected changes in theme or plugin behaviour, new files appearing, or modifications to existing files. Integrity monitoring with regular scans will detect these alterations quickly.
In June 2024, security researchers uncovered a backdoor in five plugins running on around 36,000 websites. The malicious code was part of a supply chain attack that affected the Social Warfare, BLAZE Retail Widget, Wrapper Link Elementor, Contact Form 7 Multi-Step Addon, and Simply Show Hooks plugins.
Security plugins like Shield Security PRO offer comprehensive protection against such threats. Shield Security PRO’s automated scanning and monitoring features can identify malicious code in themes and plugins, alerting you to potential backdoors before they can be exploited. It can even verify the integrity of premium plugins through its exclusive crowd-sourcing technology, comparing your files against what they should look like based on data from other users.
wp-config.php file
The wp-config.php file contains essential configuration details for your WordPress site, like database credentials and security keys. Its importance makes it a prime target for backdoor insertion.
Signs of compromise include unexpected changes to the file size or modification date, or the presence of unfamiliar code. You need to keep an eye on this file to detect threats and unauthorised alterations early.
Shield Security PRO offers an exclusive feature designed specifically for this file, called FileLocker. It lets you “lock” the contents of the file and be alerted any time there’s a change. You can then see a diff of the contents helping you to examine the contents and decide whether the change was good, or bad.
Alternatively, to manually inspect wp-config.php:
- Download a copy of the file.
- Open it in a text editor and look for suspicious code, particularly obfuscated or encoded strings.
- Compare it with a known clean version or a recent backup.
- If you find malicious code, replace the entire file with a clean version.
Always maintain current backups before making changes so you have something to roll back to if you make a mistake with the original.
Uploads directory
The wp-content/uploads directory is a prime target for backdoor insertion. This folder, used for storing media files, and very often many other files from plugins and themes used on the site. Because it’s so busy, it’s an attractive hiding spot for malicious code.
Signs of compromise include the presence of unusual files, particularly those with extensions like .php, .js, or .exe, which shouldn’t typically be in an uploads folder. Unexpected subfolders or files with obfuscated names are also red flags.
To manually inspect the uploads directory:
- Access your site via SFTP or file manager in the control panel.
- Navigate to wp-content/uploads.
- Look for suspicious files or folders, especially those with recent modification dates.
- If found, download and analyse them before deletion to ensure they’re not legitimate.
While manual inspection is valuable, it can be time-consuming and error-prone. For more comprehensive protection, consider using Shield Security PRO. Its automated scanning features can regularly check the uploads directory, alerting you to threats as early as possible.
Database
Hackers can insert backdoors directly into the WordPress database, often targeting the wp_options table. This method is particularly insidious as it bypasses file-based security scanning.
Signs of database compromise include unexpected entries in tables, especially in wp_options, wp_posts, or wp_users. Look for suspicious option names, encoded content, or modifications to existing entries.
To manually inspect your database:
- Access your database through phpMyAdmin or a similar tool.
- Examine the wp_options table for unfamiliar entries, particularly in the option_name and option_value fields.
- Check wp_posts for unexpected content, especially in post_content fields.
- Review wp_users for unauthorised admin accounts.
Shield Security PRO uses its custom-designed Snapshot technology to enhance its activity tracking. It can detect changes made directly to your WordPress database, including new/removed DB tables.
Core WordPress Files
As their name suggests, WordPress core files are a vital component of your site, making them attractive targets for backdoor insertion. Hackers may inject malicious code into these files that compromises your entire site.
Signs of core file tampering include unexpected changes to file sizes or modification dates, or the presence of unfamiliar code within these files.
Manually verifying core file integrity is practically impossible given how many files there and the complexity of the task. Tools like Shield Security PRO offer automated core file scanning, comparing your files against the official WordPress repository to identify any discrepancies. This ensures that your core files remain tamper-free.
However, core file integrity checks are just one aspect of comprehensive malware detection. To truly safeguard your site, you need a holistic approach to scanning for malicious code across all areas of your WordPress installation we’ll explore below.
How to scan for, identify, and remove malicious code
With backdoors potentially lurking in your WordPress code, regular malware scans are critical. As we’ve already seen, you can try to manually inspect your site, or use a plugin to automatically do it for you.
Remember, finding malware doesn’t solve the problem; it only alerts you to it. Once identified, you must remove the malicious code. This can be done by manually deleting the code or, more safely, replacing the entire compromised file with a clean version from a fresh WordPress install.
We strongly urge you to consider using a WordPress security plugin to automatically monitor and scan your site regularly.
Using a plugin
Shield Security PRO offers a robust malware scanner that can detect and alert you to potential threats.
A standout feature of Shield Security PRO is its MAL{ai} technology. This advanced system has demonstrated the ability to identify 8 out of 10 previously unseen malware injections, showcasing its effectiveness against new and evolving threats.
Some other malware scanners for WordPress include NinjaScanner, Wordfence, and Sucuri‘s malware scanner.
Here’s how to access and configure the malware scanning settings in Shield Security PRO:
1. Open the Security Dashboard from the Shield Security PRO section of the plugins menu.
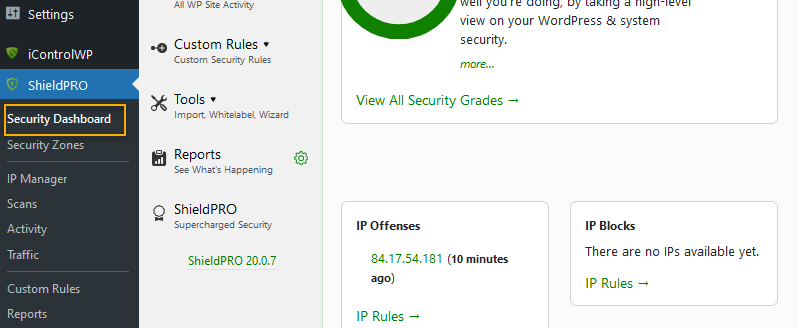
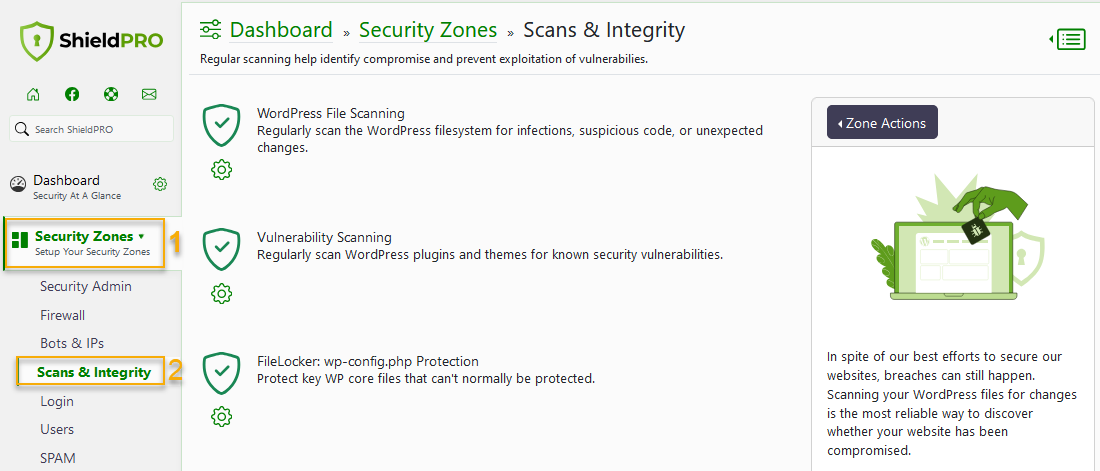
2. Using the menu on the left, go to Security Zones > Scans & Integrity.
3. Go to the WordPress File Scanning and choose which areas you want the scanner to go through.
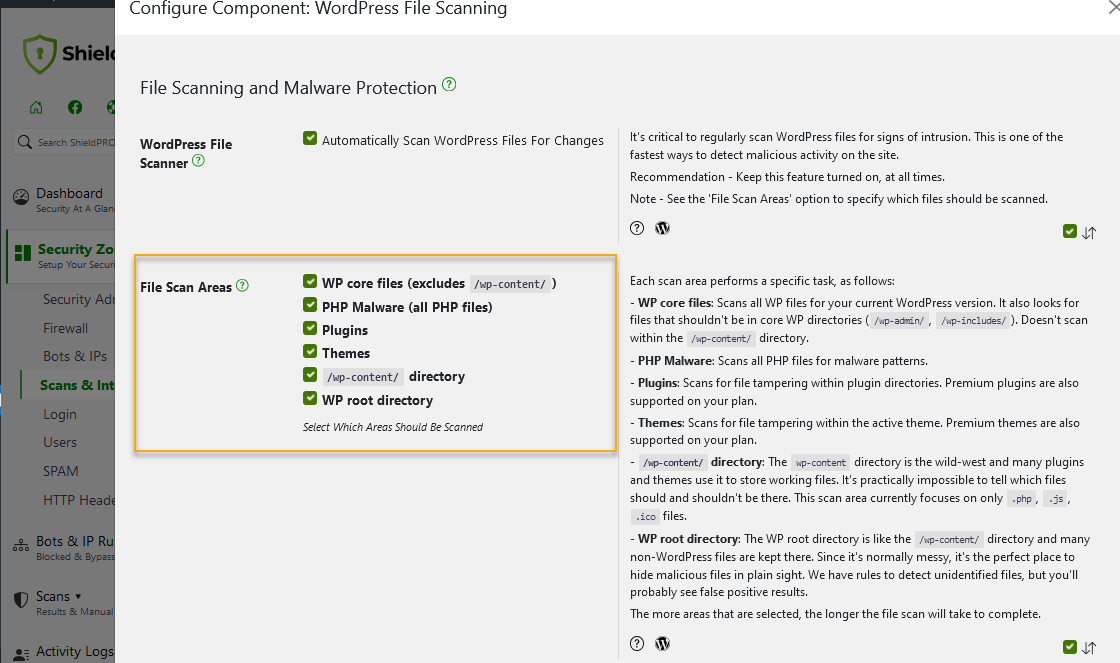
4. When you’re done, scroll to the bottom and save your settings.
5. From the menu on the left, go to Scans > Run.
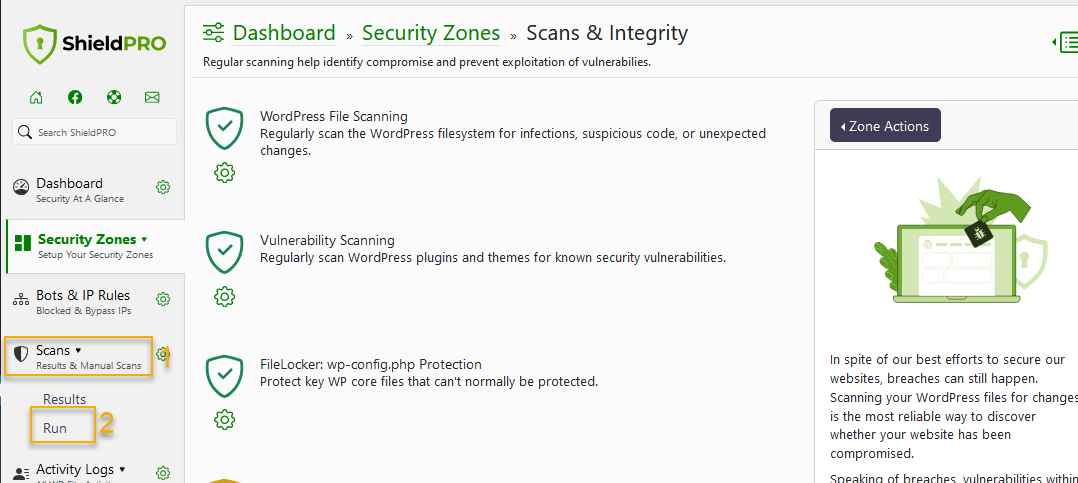
6. Click on Run Scans Now to start the process based on your pre-configured parameters.
Manual backdoor identification & removal
Manual review of WordPress files for malicious code is possible but not recommended for several reasons:
- It’s easy to overlook subtle malware insertions.
- There’s a risk of misidentifying legitimate code, potentially breaking site functionality or design.
- The process is time-consuming and mentally taxing, often leading to stress and fatigue.
If you still choose to identify and remove malware manually, you should create a comprehensive backup first. This precaution allows you to restore any legitimate changes accidentally damaged during cleanup.
Implementing security best practices to prevent future hacks
Once you’ve found a backdoor, you need to take extra steps to remove it completely from your site and prevent similar attacks in the future:
- Run regular security scans to detect any lingering or new malicious code.
- Replace all WordPress core files, plugins, and themes with fresh copies from trusted sources.
- Carefully inspect custom themes and plugins for remaining malicious code.
- Change all passwords and access credentials.
- Implement 2FA for enhanced login protection.
- Continuously monitor for unusual activity and conduct regular security scans.
Shield Security PRO is an excellent tool for achieving these goals. It offers enhanced login protections, site activity monitoring, file scanning for malware, and bad-bot blocking to prevent future backdoor injections.With Shield Security PRO, you can automate many security practices, providing robust, ongoing protection for your WordPress site. Don’t leave your site vulnerable – get started with Shield Security PRO today and fortify your digital presence!

