The balance between functionality and security is a delicate one for WordPress sites. A classic example concerns XML-RPC, a built-in protocol enabling communication with other platforms.
While XML-RPC has its uses, it’s particularly vulnerable to cyber attack. From brute force attempts on logins to DDoS attacks, the XML-RPC endpoint is open to potential exploitation. If your WordPress site doesn’t make use of XML-RPC, leaving this open to attack is not a risk worth taking.
This article will explore XML-RPC, examining the balance between its usefulness and security risk. You’ll discover whether it’s worth keeping for your own needs, and if not, how to disable XML-RPC on WordPress to help keep your site safer from malicious activity.
What is XML-RPC?
XML-RPC is a web service that connects WordPress with external services. It defines how data is exchanged and allows interaction between the WordPress platform and different services.
To break it down into its two component parts,
- ‘XML’ refers to Extensible Markup Language, the language of the data format WordPress uses to export site content.
- ‘RPC’ stands for Remote Procedure Call. This protocol enables a website to execute code remotely from a different site.
XML-RPC plays a major role in facilitating connectivity between third-party apps and the WordPress platform. It enables changes to be made to your website through the likes of mobile devices, such as uploading new content, or updating software.
Originally, XML-RPC was integrated into WordPress to allow users to manage their sites without needing to be at their desktops. Usage declined, however, when WordPress introduced the REST API (Application Programming Interface), which offers many more capabilities.
Given its history, XML-RPC has retained its default-activated status in WordPress installations since version 3.5 and will likely still be enabled on your sites.
Why might you want to disable XML-RPC?
Due to its automatic activation in new WordPress installations, some users are naturally confused as to why they might need to disable it. This is especially so for anyone using its external linking functions on a regular basis.
Despite its utility, its outdated nature can cause problems for web owners. XML-RPC has some serious cybersecurity vulnerabilities and can potentially be a gateway for brute force attacks, DDoS, and unauthorised access.
Through XML-RPC, hackers are able to attempt login exploits, testing multiple, simultaneous user and password combinations, repeatedly, undetected. They can also use DDoS attacks to overwhelm a server, slowing down the site and web services for genuine users. Unauthorised access attempts may result in a hacker gaining entry to an organisation’s network, and putting all sensitive data at risk.
Given such risks, it’s clear why many have disabled XML-RPC access. However, it’s important to be aware of the pros and cons of doing so. While disabling XML-RPC can strengthen your security posture, it may affect other connected programmes and plugins, causing unforeseen trouble elsewhere.
When should XML-RPC be kept enabled?
Depending on your website’s needs, XML-RPC can either be an asset or potential security liability. It’s critical to evaluate its usage and understand the implications of disabling XML-RPC before making any final decision.
Keeping XML-RPC on your site can be necessary to maintain various features. Jetpack is an example of a popular WordPress plugin that needs XML-RPC, and many mobile apps are the same. You’ll need to assess which of these features and apps you deem essential to your business as part of the decision-making process. In some cases, you may need to reach out to the app developers to check whether they require XML-RPC access.
Of course, it’s worth determining whether you actually have XML-RPC enabled on your site as a starting point. Given it’s activated as-standard, it’s highly likely. But if your site was designed by an outside developer, there’s a chance it was disabled during the build process.
- In your web browser, simply enter your website’s URL, followed by
/xmlrpc.php: https://yourwebsitename.com/xmlrpc.php - A response stating that the ‘XML-RPC server accepts POST requests only’ means the function is enabled.
- A 404 error page or a security plugin’s ‘Access Denied’ message means XML-RPC is disabled or blocked.
Additionally, you can monitor your site’s traffic and inspect your plugins and themes to identify XML-RPC activity. Advanced users can search through the source code of plugins and themes via a Secure File Transfer Protocol (SFTP) client, or through the WordPress Content Management System (CMS). Access your site’s control panel, visit ‘Files’ > ‘File Manager’.
Plugins and themes are typically stored in your File Manager’s /wp-content/ folder. Check the source code of both /wp-content/plugins and /wp-content/themes. Search for references to xmlrpc.php, or input the following:
add_filter('xmlrpc_enabled','__return_true');
This is a filter function used to enable, or disable, XML-RPC on a WordPress site.
Text editors with search functionality or Integrated Development Environment (IDE) software can be used to scan through your /wp-content/ files. Experienced WordPress developers can also enable debugging to identify any errors or notices related to XML-RPC functionality.
How to disable XML-RPC on WordPress
If you’ve made your assessment and decided to disable XML-RPC, there are several ways to go about the process. As a time-saving option, it’s worth contacting your hosting provider as a first point of call. They may be happy to do the job for you or guide you through it step-by-step. Failing that, you have the following three options:
1. Using code
If you’re comfortable coding, it’s a relatively simple operation. Access the .htaccess file in your WordPress site’s root directory using an SFTP or through the File Manager section of your site’s control panel. Once you’ve found it, add the following code to the bottom of the file:
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>Save the .htaccess file and upload it back to the server if you edited it offline. If using the Apache server, version 2.4 or later, input the following code instead:
<Files "xmlrpc.php">
Require all denied
</Files>These changes will block all access to the xmlrpc.php file.
2. Using code snippets
Alternatively, you can use code snippets by accessing your WordPress child theme’s functions.php file. As before, you’ll find this by using an SFTP or through your site’s control panel. Depending on your site’s theme, it may also be accessible through Appearance > Theme File Editor via the WordPress dashboard.
Once you’ve arrived, add the following code to the bottom of the page:
add_filter('xmlrpc_enabled', '__return_false');
As with the first method, remember to save changes, and upload it back to the server if working offline.
3. Using a plugin
If in any doubt, use a dedicated plugin. Even experienced coders may run into difficulty if any issues arise. A good security plugin will manage the process for you, and if the disabling process doesn’t work, it will provide activity logs to help you solve any problems.
Disabling XML-RPC on WordPress with Shield Security PRO
A premium intrusion-prevention platform, Shield Security PRO makes website security easy with its user-friendly interface and automation tools. Handily, the plugin can also help you determine whether disabling XML-RPC is the right choice for you.
Once you’ve installed the plugin, take the following steps to see if your site is actually using XML-RPC:
- From the dashboard, go to Config>Bot Blocking.
- Locate the ‘Bot Behaviours’ tab.
- Find the option ‘XML-RPC Access’ section.
- Turn this on to ‘Activity Log Only’ to monitor XML-RPC activity.
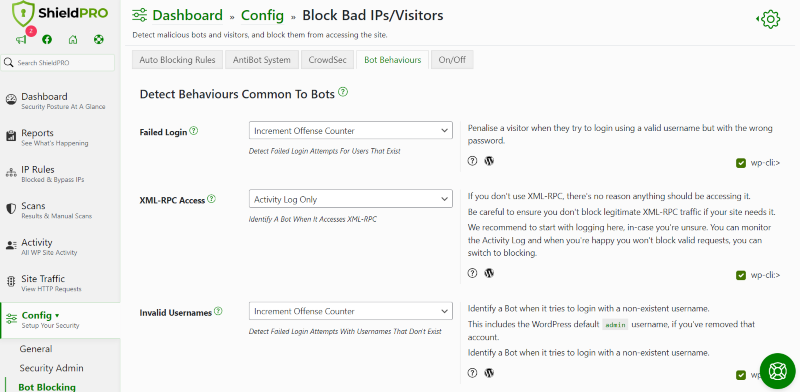
Monitor your activity logs for a few days to see if there are any legitimate requests to your XML-RPC. If you’re seeing genuine traffic there, you may want to hold off disabling it.

Otherwise, you can disable XML-RPC on WordPress by retracing the above steps:
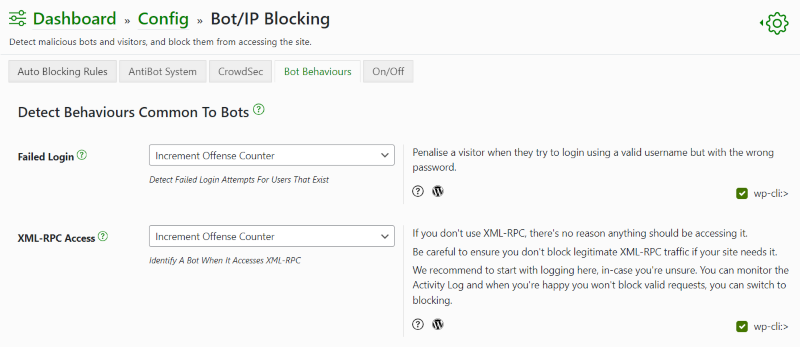
- From the dashboard, go to Config>Bot Blocking.
- Locate the ‘Bot Behaviours’ tab.
- Find the ‘XML-RPC Access’ section.
- Switch this to one of
- Increment Offence Counter
- Double-Increment Offense
- Immediate Block
Configuration errors or compatibility conflicts can arise as a result of disabling XML-RPC on WordPress. Should any problems occur, Shield Security PRO offers comprehensive support, helping you resolve issues smoothly.
Furthermore, the platform offers a complete security solution, protecting your site against everything from brute force amplification attacks to spam and malware.
You can also disable anonymous REST API requests through the platform. Only requests with verified authentication can proceed.
Verifying that XML-RPC has been disabled
After you’ve completed the above process, it’s worth verifying that XML-RPC has been disabled on your site. This is a simple process, and can be done using a free online XML-RPC service checker.
Type in the URL of your website or test site, followed by /xmlrpc.php. If the tool indicates a successful connection, XML-RPC has not been disabled properly. Naturally, if it fails to connect, XML-RPC has been disabled.
Eliminate XML-RPC security risks with Shield Security PRO
It’s clear that XML-RPC can pose significant security risks for those managing a WordPress website. But it’s best to be cautious when it comes to disabling XML-RPC, in order to avoid causing complications elsewhere. Check how many of your features use it before disabling, and if you want to disable XML-RPC, research alternatives for features that still need it.
Given the vulnerability to unauthorised access attempts, DDoS, and brute force attacks, disabling XML-RPC can be crucial for website security. Shield Security PRO provides extensive protection for similar threats, including those that are related to XML-RPC.
Disabling XML-RPC is simplified with the Shield Security PRO plugin’s user-friendly design, suited to developers and non-techies alike. Beyond XML-RPC, you’ll gain a suite of features aimed at keeping your site safe, from login protection to a malware scanner, and fully automatic Bot & IP blocking.
Make your XML-RPC assessment a top priority to keep hackers at bay. Get started on strengthening your site with Shield Security PRO today!

