WordPress powers millions of websites, making it a prime target for hackers. Protecting your WordPress website is crucial, whether you’re running a small blog or a booming eCommerce business.
In this article, we’ll cover basic security best practices for your WordPress site so you can shield your website from hackers, malware, and other potential threats.
Protecting your website from bad bots
Two types of visitors go to your site: humans and bots. Bots account for nearly half of all internet traffic. While this statistic might be alarming, it’s worth noting that not all bots are harmful.
Good bots, like search engine crawlers, AI crawlers, uptime monitoring bots, and translation bots, perform useful tasks for your website and visitors. Bad bots perform harmful actions, including content scraping, leaving spam comments, and brute force attacks.
By blocking bad bots and allowing the good ones, WordPress site owners can shield their websites from many cyber threats. Let’s explore ways to keep the bad bots at bay.
Block bad bots with Shield Security PRO
Shield Security PRO identifies and blocks bad bots while letting the good ones pass. Its AntiBot Detection Engine (ADE) distinguishes between humans, good bots, and bad bots by assigning a score for every WordPress visitor. If a user shows too many bad-bot-like behaviours, Shield Security PRO blocks them from accessing your site.
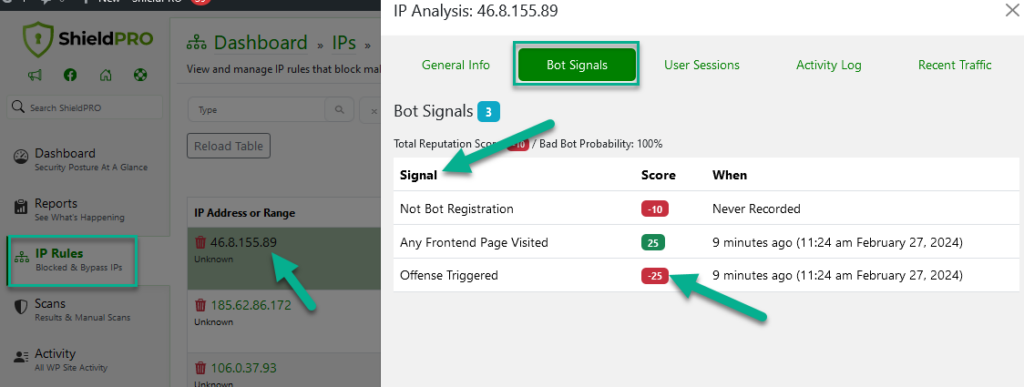
Unlike CAPTCHAs, which disrupt the user experience, the ADE runs in the background, ensuring uninterrupted browsing while protecting your website against malicious bots and fake web crawlers. With Shield Security PRO’s Automated Black List System, you can use automatic IP-blocking technology to block bad bots after a specific number of offences.
Bad bots drain your site’s resources and affect its performance. Shield Security PRO keeps them out, lightening the server load and boosting your website’s performance.

Set up honeypots on forms
Honeypots are invisible form fields that trap harmful bots. Benefits include extra spam protection, identifying bot attacks, and cleaner user experience without CAPTCHAs.
And the best part? Many form-building tools like Elementor include honeypots. The exact steps for setup will vary depending on the plugin you’re using.
Stump bots with simple maths
Bots struggle with maths problems. You can outsmart bots that can’t solve them by adding simple maths challenges to your forms. Once you do, all incoming messages are then screened for the answer.
This method thwarts bots and is a user-friendly alternative to complex bot checks like CAPTCHA and reCAPTCHA. For users who find these puzzles frustrating or confusing, solving single-digit numbers is often smoother. However, remember to keep your problem simple to reduce user frustration as you don’t want to simply swap out 1 frustrating anti-bot mechanism for another.
To protect your WordPress site, implement maths challenges in comment sections, user registration forms, and login pages.
Improving login protection
Your login page is the primary gateway to administrative site access. You can ensure only legitimate users gain access by enforcing strong password policies, applying two-factor authentication (2FA), and enabling passkeys.
Login pages are vulnerable to attacks, so it’s crucial to take login protections seriously across your organisation. Here’s what you can do:
Strengthen password requirements
Weak, reused passwords pose a serious risk to WordPress security. They’re easier for attackers to crack, leaving you vulnerable to data breaches, account takeovers, and identity theft. The consequences are severe for organisations, as weak passwords can compromise entire systems or networks, allowing attackers to infiltrate internal resources.
Enforcing strong password policies is a great way to shore up your site defences. The best practice is to use a combination of uppercase and lowercase letters, numbers, and special characters. And remember, the longer the password, the better. A 12-character password takes 62 trillion times longer to crack than a six-character password.
Shield Security PRO allows you to set a required password strength and blocks compromised/pwned passwords, among other password policy features.
Add 2FA or passkeys
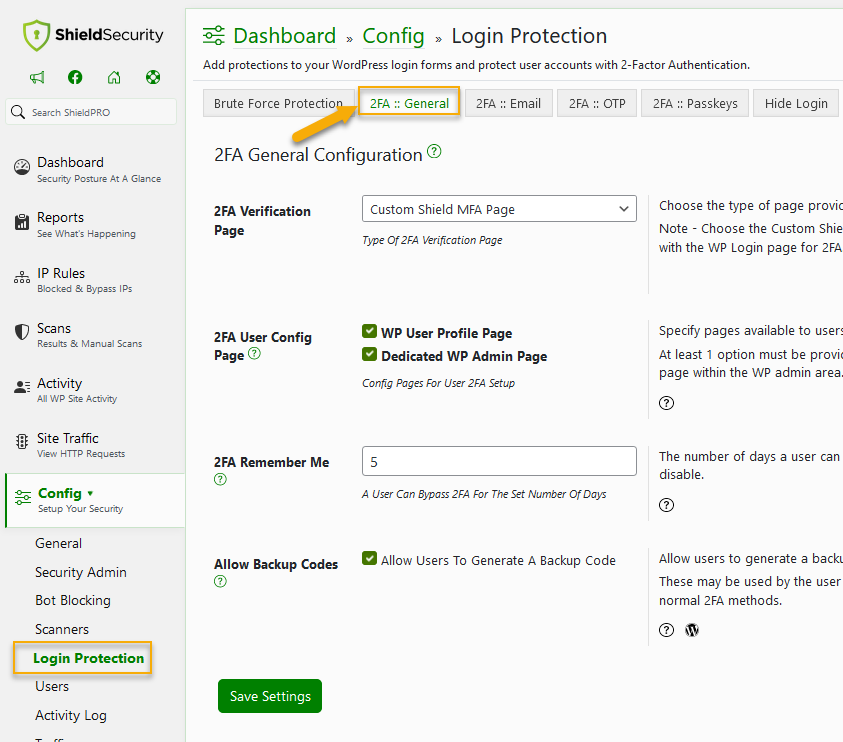
2FA & Passkeys add further user verification after entering your username and password. Enabling 2FA for your WordPress website can protect you from many threats, such as brute force login attacks and account takeover. Even if a hacker guesses the password, they would need access to your phone, email, or authenticator app to get the 2FA login code.
Implementing 2FA on your WordPress website is easy with plugins like Shield Security PRO. It allows email-based 2FA and use with security devices such as Passkeys and Yubikey. The Shield Security PRO dashboard goes a long way to simplifying 2FA deployment.
Teach login credential security
To secure your WordPress website, ensure all users understand the importance of maintaining proper login credentials. Educating users on best practices fortifies your site’s defences, reduces the risk of cyberattacks, and fosters a security-aware culture.
To protect your WordPress website, start by creating strong passwords with letters, numbers, and symbols. Encouraging the use of password managers can help a great deal. Educate users about the benefits of 2FA and its security against phishing and social engineering attacks.
User education may seem time-consuming, but Shield Security PRO can support administrators by blocking compromised passwords and enforcing password strength minimums.
Tracking website activity
Observing user interactions and system operations can help identify security threats and set a benchmark for normal website behaviour. Let’s explore why activity tracking is essential and how it contributes to a safer WordPress environment.
Use an activity-tracking tool
Activity tracking tools monitor website traffic and user behaviour. Administrators detect and respond quickly to unusual behaviour, and potentially prevent security breaches.
Shield Security PRO offers robust activity tracking with real-time alerts and a detailed log viewer. This allows administrators to stay informed about suspicious activity and take immediate action to mitigate risks.
Because it’s integrated directly into WordPress, it offers detailed logging of your accompanying security measures and it’s completely WordPress-aware and seamlessly capture events.
Learn to identify your normal
Understanding your website’s normal activities and performance metrics helps you quickly identify anomalies that might indicate security threats or technical issues.
Use analytics tools to track user behaviour and monitor seasonal traffic variations. Set benchmarks for login frequency, visitor traffic, and admin activities. Regularly review these metrics to identify unusual or suspicious activity.
Investigate abnormalities
When activity tracking tools detect something unusual, it’s important to take early steps to assess whether the abnormality is a security threat, a false alarm, or a harmless irregularity. Having clear investigative steps and implementing routine checks is needed for swift responses to potential threats.
Shield Security PRO provides insights through its Activity Log and Alerts system, helping you to remain vigilant and keep your sites safe against security risks.
Reviewing site access
Below are key steps for conducting a site audit:
Run a site-access audit
Adhering to the principle of least privilege (PoLP) can protect against internal security breaches. PoLP minimises the risk of unauthorised activity by assigning users only the necessary permissions.
When conducting an audit, review user roles to limit access to what is absolutely necessary. Remove outdated accounts and adjust permissions based on current responsibilities. Double-check administrative access and access logs for suspicious activity.
Running a site-access audit can be intimidating, but security plugins like Shield Security PRO simplify the process by automating the review of user access by automatically suspending idle accounts, for example.
Check your hosts’ security measures
Securing your WordPress website starts with choosing a reliable web host with essential security features. As you explore hosting packages, ensure they include:
- DDos protection: Distributed Denial of Service (DDos) protection guards the site against overwhelming traffic attacks to ensure your site remains online.
- Server isolation: Server isolation ensures that each website operates independently. It prevents a security breach on one site from contaminating other hosted websites.
- Secure Sockets Layer (SSL) certificates: SSL certificates safeguard sensitive information, such as login credentials, payment details, and personal data, by encrypting data exchanged between your site and its visitors.
- On-demand customer support: Access to responsive and knowledgeable customer support is important for addressing security concerns or technical issues.
- Automated backups and malware scanning: Automated backups create regular snapshots of your website’s data, enabling restoration to a previous state in case of data loss. Malware scanning tools automatically detect and remove malicious code, preventing security breaches.
- Firewall and intrusion detection systems: Firewalls monitor and filter traffic to your website, blocking malicious requests and unauthorised access attempts. Intrusion detection systems (IDS) monitor for suspicious activity or security breaches, providing extra protection.
Confirm that your web host provides some of these essential security features. Evaluate your current hosting provider against these standards. If there are gaps, consider switching to a provider that offers more.
When choosing a hosting provider, prioritise those that value ‘security by design’. Ask potential providers about their security approach and specific measures in place to protect your site.
Shield Security PRO complements web hosts by providing additional security measures, such as real-time threat defence.

Update plugins, themes, and core
One of the biggest causes of WordPress hacks is outdated software, so it’s essential to set some time aside every week to keep all your plugins, themes, and WordPress core up-to-date. Regularly updating your software is a win-win: You benefit from new features and protect your site against known vulnerabilities.
Concerns about update-related bugs are valid, as they can compromise site functionality or cause temporary issues. Shield Security PRO offers an Auto-Updates Delay feature that forces any automatic upgrade to be delayed for a set number of days. This allows time for bugs to be discovered and patched before your site updates.
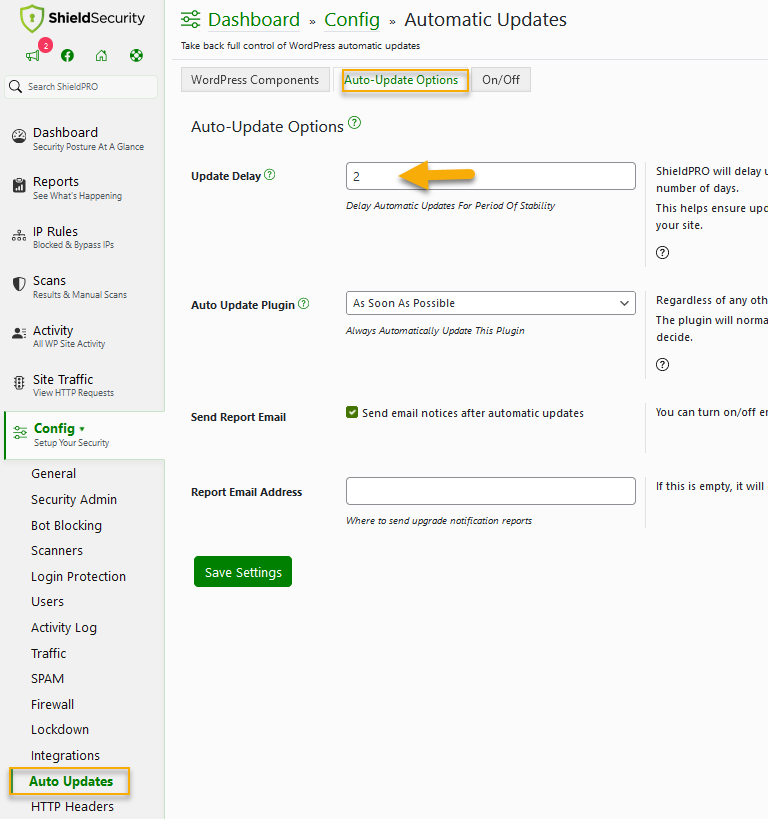
Shield Security PRO’s Vulnerability Scanner checks for known security vulnerabilities and upgrades affected plugins when patches are available. When the scanner finds a vulnerable plugin, it highlights it on the WordPress admin page and sends a daily email notification.
Upgrade your WordPress security with ShieldPRO today.
Ensuring the safety of your WordPress site requires a commitment to essential security practices. Regularly updating your digital assets and setting up 2FA and strong passwords are vital for maintaining the integrity of your site.
If your security checklist is endless, the good news is that security plugins like Shield Security PRO can lighten the load by simplifying your site security processes. With its automated features and advanced bot-blocking technology, Shield Security PRO ensures your website and its visitors remain secure.Level up your WordPress security with Shield Security PRO today!


