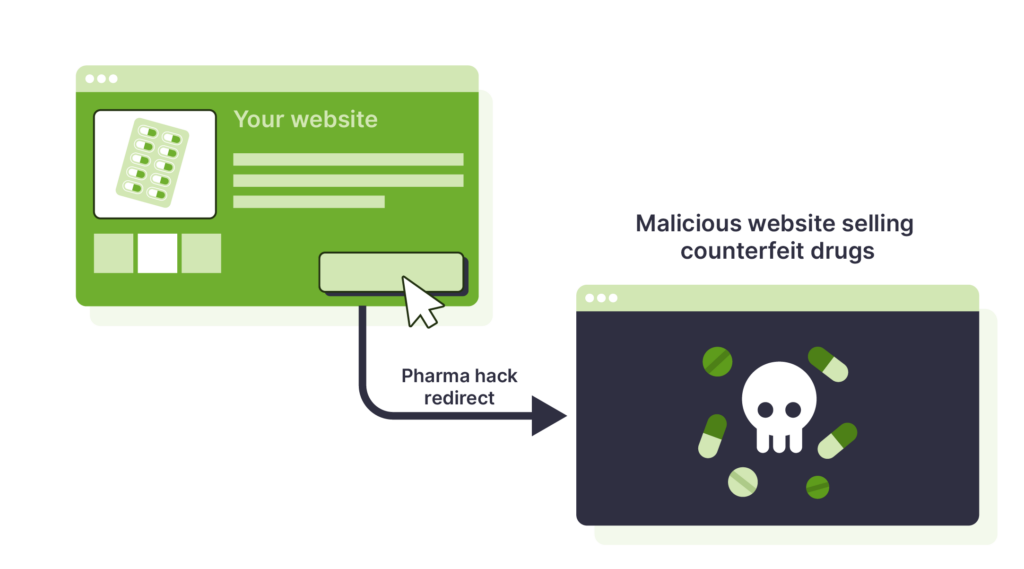
WordPress powers millions of websites, and this popularity also makes it a target for hackers. One of the most common and dangerous hacks that WordPress websites can fall victim to is the pharma hack.
Imagine a potential customer looking for your product, typing its name into Google, and finding it effortlessly. However, the search results usher them to an obscure page offering suspicious medications. This is the WordPress pharma hack.
In this article, we’ll show you how to identify, purge, and fortify your website against this hack!
Deciphering the WordPress pharma hack: Symptoms and detection
As we’ve said, the WordPress pharma hack steers unsuspecting visitors toward an illegitimate sales page selling fake medications. It cunningly exploits your highest-ranking pages, using their credibility to funnel traffic toward the scam site.
Hackers setting up this malicious code typically gain entry to your site through outdated or vulnerable themes and plugins, and the repercussions include:
- Redirects.
- Poor server performance.
- Unusual activities in server logs.
- In some cases, a complete website blackout.
If you notice a change in your website’s meta description or metadata (visible when previewing site pages on search engines), that’s a clear sign of the WordPress pharma hack. This seemingly simple alteration is an attempt to deceive search engines and, subsequently, unsuspecting users.
What’s worse is this hack can go unnoticed for a long time. If you’re not regularly checking, no one alerts you to the redirect, or you don’t stumble onto the affected page yourself, you might not realize it’s damaging your website’s reputation.
How to find out if your site is affected by the pharma hack
Detecting the pharma hack on your website is important for promptly addressing the issue and preventing further damage. Here are several steps you can take to determine if your site has been compromised:
- Monitor search engine results: Keep a close eye on search engine listings for your website. Look out for unusual titles, descriptions, or URLs associated with your site, as these could indicate unauthorized changes or malicious activities.
- Use website scanners: Employ online tools and website scanners like VirusTotal, Google Safe Browsing, or Sucuri SiteCheck to identify vulnerabilities and malware infections on your site. Regular scans can help detect suspicious scripts, malware, or blacklisting status.
- Security plugins like Shield Security PRO: Specific security plugins designed for platforms like WordPress, such as Shield Security PRO, offer features tailored to detect and protect against almost any type of hack, including the Pharma Hack. Use integrated malware scanners to promptly identify and neutralize any such the attack.
- Analyze website traffic patterns: Keep an eye on traffic patterns using web analytics tools like Google Analytics or Jetpack Stats. Sudden spikes or unusual referral sources in website traffic could signal a pharma attack.
If you suspect your site has fallen victim to the pharma hack, taking immediate action is crucial to mitigate damage and restore integrity. We’ll provide detailed instructions on how to do this later.
Understanding the impact: SEO and business ramifications
SEO performance
Beyond the obvious redirection of users to illegitimate sales pages, the hack manipulates metadata, distorting the site’s appearance on Search Engine Result Pages (SERPs). This misrepresentation not only diverts potential visitors but also devalues the site’s ranking, having a huge negative impact on SEO.
Traffic and revenue loss
When a website falls victim to the pharma hack, it sees a decline in its visitor count, which can result in a potential loss of revenue. When visitors are driven away due to false information on a website, it directly impacts the website’s ability to attract new customers and generate sales.
User experience and credibility
The hack leaves an unforgettable mark on user experience and website credibility. Unsolicited pharmaceutical advertisements linked to the hack impact the trust built with the target audience.
The consequence? Elevated bounce rates, decreased engagement, and a tarnished brand reputation.
Blacklisting threats
If Google or other search engines flag the affected WordPress site for malicious content, getting back on track can be tricky. Removal from blacklists takes time and concerted effort, compounding the negative impacts on business and online presence.
🛡️ Worried about your site’s reputation? Verify its status using Google’s Safe Browsing tool.
Step-by-step removal: Cleaning up the pharma hack mess
Discovering your site has been hacked can be very unsettling, but there’s plenty you can do to regain control. Here’s our step-by-step guide to the cleanup process.
Automated cleanup with Shield Security PRO
For a simpler, efficient solution, consider using a dedicated security plugin like Shield Security PRO. This WordPress security plugin features an AI-powered malware scanner that automatically scans through your website files, identifying malicious code with minimal user intervention. Here’s how you can use Shield Security PRO for automated cleanup:
- Install and activate Shield Security PRO: Begin by installing and activating the Shield Security PRO plugin on your WordPress website.
- Run malware scanner: Navigate to the plugin dashboard and initiate the malware scanning process. The scanner will analyse your website files, detecting any malicious code or unauthorised modifications.
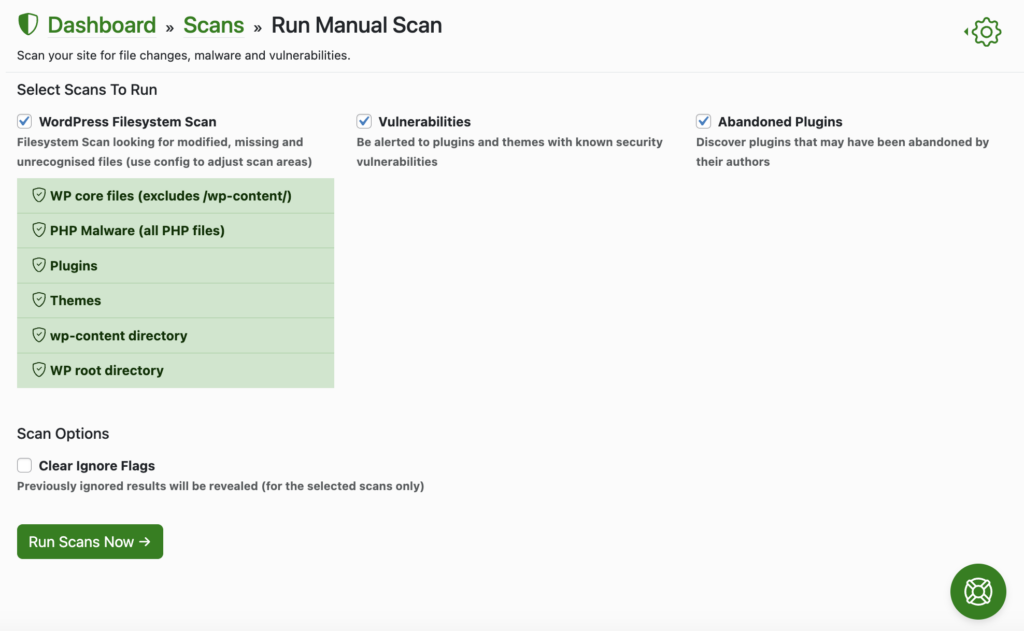
- Automatic cleanup: Upon completion of the scan, the plugin can automatically replace damaged files with clean versions wherever possible, or prompt you for manual intervention, to restore your site to its secure, clean state.
Manual cleanup
If you prefer a hands-on approach or do not have access to automated tools, you can manually remove the pharma hack mess from your website. Follow these steps carefully:
- Create a backup: Before making any changes, create a backup of your entire website to ensure that you can restore it to a previous state if needed.
- Identify compromised files: Access your website’s root directory through your hosting provider’s control panel or SFTP client. Look for files that have been compromised by the hack, such as those containing unusual code or recent modifications. Consider using a website scanner or security plugin like Shield Security PRO to assist in identifying infected files accurately.
- Focus on these files: .htaccess file, wp-config.php, theme files (especially header.php and footer.php, and compare them to the originals if you can), and the Uploads directory
- Base64 encoding: Many hacks, including the pharma hack, use Base64 encoding to obfuscate malicious code. Search your site files for base64_decode (but be aware that some legitimate plugins might use this encoding for non-malicious reasons too.
- Remove malicious code: Once you’ve identified the compromised files, open them for editing and carefully examine the content. Remove any malicious code or suspicious scripts, ensuring to delete only the infected portions while preserving the integrity of essential files.
- Clean the database: The pharma hack often injects malicious URLs into the database. Use phpMyAdmin or a similar tool to search for suspicious content. Commonly affected tables include wp_options, wp_posts, and wp_postmeta. Look for any strange URLs or long, encoded strings.
- Verify website functionality: After cleaning the compromised files, visit your website to ensure that it is functioning normally and that the malicious redirect caused by the hack has been eliminated. Test various functionalities and pages to confirm that no residual issues persist.
- Further investigation: If the redirect or malicious behaviour persists, conduct a more thorough investigation to identify any remaining infected files or hidden malware. Consider enlisting the assistance of a professional security expert or using advanced scanning tools to detect and remove persistent threats.
❗ While you can manually do this by delving into your website file directory using your hosting provider’s control panel (like cPanel), this method is tedious and error-prone. That’s why we recommend using a designated plugin like Shield Security PRO.

Restoring from backup
If your website experiences downtime or complications during the cleanup process, revert to the previously created backup to restore your site to a stable state. This ensures that you can quickly recover from any unforeseen issues without risking data loss or prolonged downtime.
How to restore a site’s reputation after a hack
Recovering from a website hack involves more than just cleaning up the malicious code, it also requires rebuilding trust and credibility with your audience and search engines. Here’s how you can do this:
Be transparent
Be transparent with your audience about the security incident and the steps you’ve taken to address it. Publish a blog post or update on your website explaining the situation, reassuring visitors that the issue has been resolved, and outlining the measures you’ve implemented to enhance security moving forward. Transparency fosters trust and demonstrates your commitment to protecting users’ data and ensuring their safety.
Update security measures
Take proactive steps to strengthen your website’s security and prevent future attacks. This may include implementing robust security plugins, updating software and plugins regularly, enforcing strong password policies, and conducting regular security audits and scans. By prioritising security, you demonstrate your dedication to safeguarding your website and users’ information.
Monitor for suspicious activity
Remain vigilant for any signs of suspicious activity or unauthorised access on your website. Utilise website monitoring tools and security plugins to detect and respond to potential threats promptly. Monitor server logs, traffic patterns, and user activity to identify any anomalies that may indicate a security breach. Prompt detection and mitigation of security incidents are essential for maintaining the integrity of your website and preventing further damage.
Re-establish trust
Rebuild trust with your website visitors by providing a positive user experience and delivering valuable content. Ensure that your website is user-friendly, responsive, and free from intrusive advertisements or pop-ups. Engage with your audience through social media, email newsletters, and other channels to reinforce your commitment to their satisfaction and security.
Engage with search engines
Notify search engines, such as Google, Bing, and Yahoo, about the security incident and the steps you’ve taken to address it. Submit a reconsideration request through Google Search Console to request a review of your website’s security status and reevaluation of any penalties or warnings imposed as a result of the hack. Implement recommended security measures and follow best practices outlined by search engine guidelines to improve your website’s search visibility and credibility.
Monitor and respond to feedback
Monitor feedback from users, customers, and stakeholders regarding their experience with your website and its security measures. Address any concerns or inquiries promptly and transparently, demonstrating your commitment to resolving issues and maintaining a secure online environment. Actively solicit feedback through surveys, contact forms, and customer support channels to gain insights into areas for improvement and identify potential security vulnerabilities.
Preventive measures: Safeguarding your site against future attacks
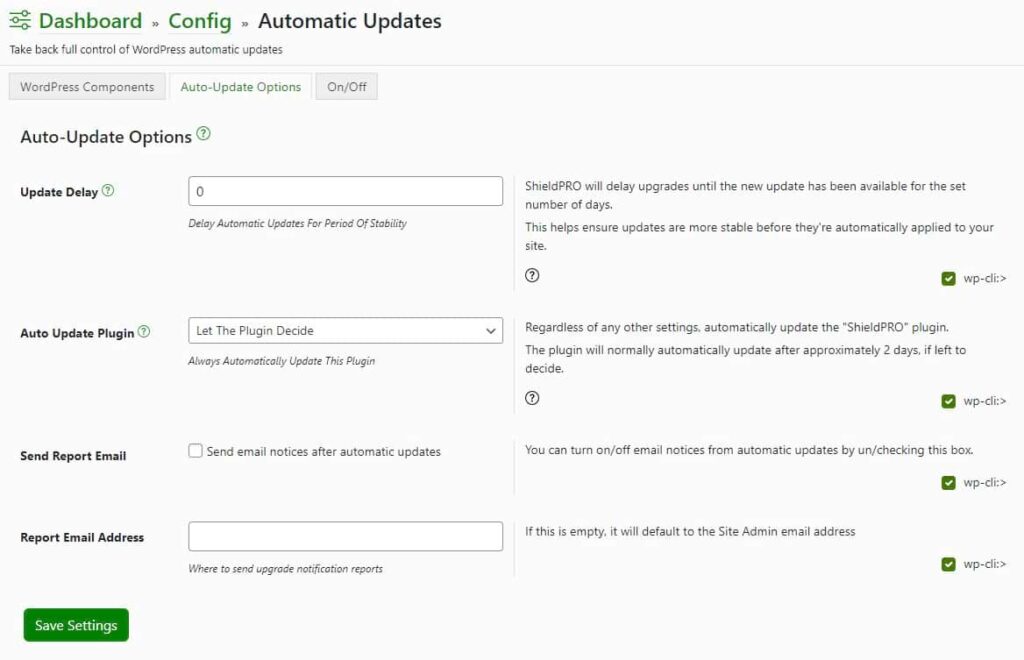
- Always keep your site updated: Regularly updating your WordPress core, themes, and plugins is important. These updates patch vulnerabilities that hackers might exploit. Shield Security PRO can help to automate the process for you.
🧐 Did you know? With Shield Security PRO, you can customise your automations to suit your unique needs. For example, you can set it to delay automatic updates by a day or so to avoid dealing with any yet-undetected bugs in brand-new updates.
- Choose every element of your site wisely: The foundation of a secure site lies in the selection of reliable themes and plugins. Avoid ‘nulled’ or cracked versions of premium themes/plugins, as they can house potential threats.
- Think about user roles: Use well-defined user roles, restricting admin access to only those who truly need it. Along with this, embrace the Principle of Least Privilege – ensuring each user only has the security privileges they need – to minimise the pathways for potential exploits.
- Use strong passwords: Set password strength minimums to ensure your users secure their accounts with strong passwords. Use additional layers of security, like two-factor authentication, to further secure your site from unauthorised access.

🔒 Enhanced security: Take advantage of Shield Security PRO’s passkey support for WordPress login!
- Train your team: Educate your team on secure practices, from never sharing login credentials to identifying phishing scams. Stress the importance of logging off shared computers to thwart potential breaches.
- Fortify your site with a WAF: Use a Web Application Firewall to fight against common threats. This measure adds an additional layer of protection to thwart potential infiltrations.
- Regularly audit and monitor: A robust security strategy includes regular security audits and monitoring. Stay vigilant, identifying and mitigating potential risks before they evolve into full-blown threats.
Maximising protection with Shield Security PRO’s advanced features
The Shield Security PRO plugin is a comprehensive cybersecurity solution, and it can handle many security measures on your behalf. Let’s take a closer look at some of its best features:
Automated bot protection
Shield Security PRO’s Automated Bot Protection effectively blocks malicious bots before they can do any damage. By deploying sophisticated algorithms, it identifies and neutralises potential threats, protecting your website against automated attacks.
Simplified security control
For those who might shy away from the complexities of cybersecurity, Shield Security PRO streamlines security control, making it accessible to non-experts, too. With automated security measures in place, users can focus on their business without the distractions.
Automatic scans
Shield Security PRO automatically scans your WordPress core and its themes and plugins. This approach ensures that your site remains resilient against attacks that target known vulnerabilities. The AI-powered scanner, MAL{ai}, can even detect never-before-seen threats, successfully catching 8 out of 10 threats it had never seen before, during testing.
Two-factor authentication (2FA)
Shield Security PRO’s two-factor authentication (2FA) feature gives you an extra layer of protection for critical user accounts against brute force attacks, and account theft. By requiring a secondary verification step, only legitimate, authorised users may gain access.
Choose Shield Security PRO for comprehensive WordPress security
When it comes to the pharma hack, opting for Shield Security PRO to fully safeguard your site is the best option available to you. With powerful malware detection and cleanup, this plugin restores your site to its original state and keeps it there.
Let Shield Security PRO give you peace of mind with features including automated bot protection, regular scans, and two-factor authentication.
Download Shield Security PRO and start protecting your WordPress site today!

