If you’re a site owner, you probably already understand the importance of keeping your website safe and secure. But did you know that one of the most vulnerable entry points for potential threats is the login page?
You might think a straightforward username and password setup is enough. However, your login page might actually be the most tempting door for malicious hackers.
No worries, though: We’re here to walk you through six easy steps to fortifying your WordPress login page. We’ll also introduce you to the Shield Security PRO plugin that makes the process of securing your online business a breeze.
More than just a typical security plugin, Shield Security PRO offers a comprehensive suite of defense mechanisms such as two-factor authentication, solid firewalls, and advanced anti-bot protection, forming an all-encompassing safety shield for your WordPress site!
Let’s get started!
Understanding the importance of WordPress login security
The WordPress login page serves as the main gateway to the administrative dashboard of your WordPress website. Just like the front door to your house, it’s the primary point of entry, allowing authorized users to access and manage their site’s content, themes, plugins, and other settings.
Strong login security is essential for every website owner. However, out of the box, WordPress’s basic login page isn’t always enough to deter cybercriminals. If left unprotected, your login page is vulnerable to malicious actors. Worst case scenario, they can gain control, potentially leading to website defacement, data theft, or even a complete site takeover.
Via brute force attacks, hackers can use bots to try out countless username and password combos to find an opening. Phishing scams can also trick users into revealing their login details by taking them to a counterfeit website that mimics the original.
So, how can you reinforce your WordPress login page’s immunity to such threats?
A quick look at the six top WordPress login security practices
- Changing the WordPress login URL: Camouflage your login page using a new URL to make it a harder target for bots.
- Identifying and blocking untrustworthy users: Safeguard your site by flagging and removing suspicious users.
- Enforcing strong passwords: Require all existing users to have complex and unique passwords.
- Using two-factor authentication: Include an additional verification step to check users’ authenticity.
- Limiting login attempts: Halt brute force attacks in their tracks by setting a timed cap on login attempts.
- Regular account reviews: Perform routine checks for redundant or unused accounts and dispose of them.
Let’s now dive into the nuts and bolts of how to implement them step by step!
1. Changing the login URL
It’s a well-known fact that WordPress sites, by default, use the example.com/wp-login.php URL for the login page. Unfortunately, this common knowledge is a target for hackers who try to log in using bots.
Changing or hiding your login URL on your WordPress site is a type of defense mechanism known as “security through obscurity”. Bots trained to only try the /wp-login.php URL find themselves at a useless dead-end, and your site stays secure.
While there are several ways you could achieve this, one of the simplest methods is by using a plugin like Shield Security PRO.

Here’s how:
- Purchase the Shield Security PRO plugin, then download, install, and activate it on your WordPress site.
- From your WordPress admin dashboard, navigate to Shield Security PRO > Config > Login Protection.
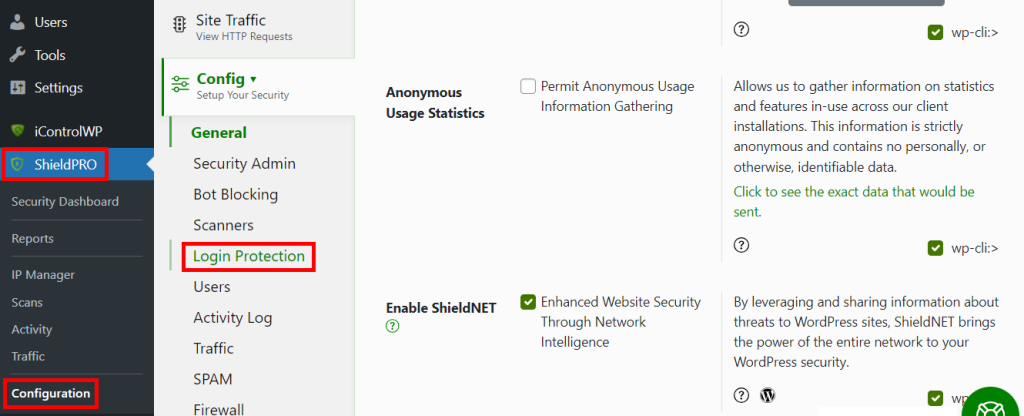
- From the Hide Login tab, create a new, unique URL for your login page.
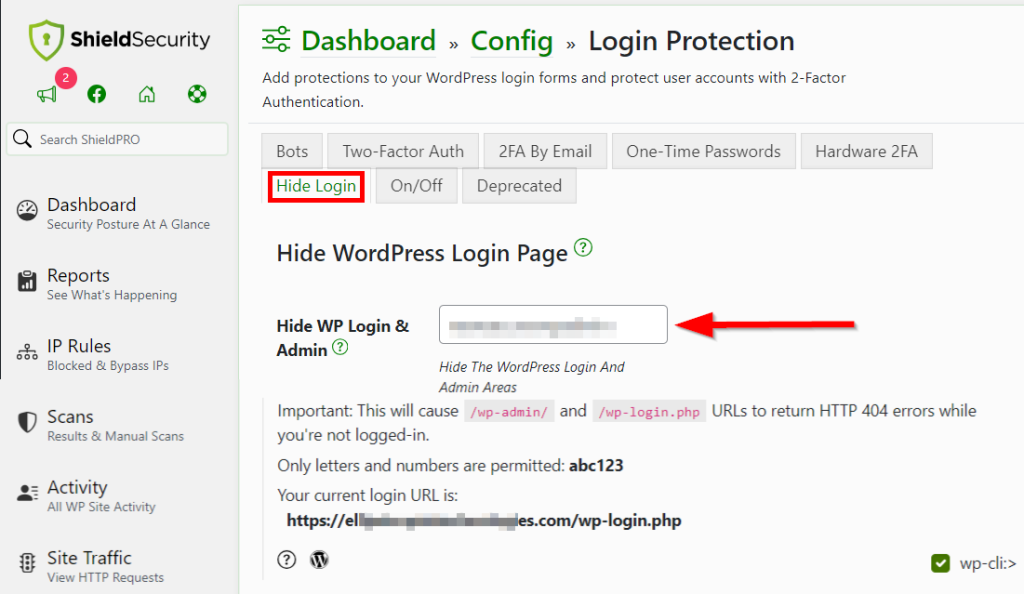
- Click Save Settings.
Note that this will have a few implications:
- Upon hiding your login URL, the /wp-admin.php version of the URL will redirect to a pseudo-404 error page unless you’re already logged in. If the default pseudo-404 page provided by Shield Security PRO is not to your liking, you can set a redirection to a custom URL from the Hide Login tab as well.
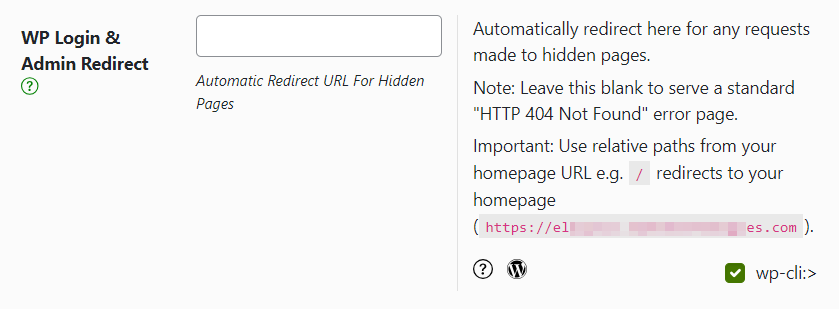
- All verified users, including you, must use the new URL to access the login page. If you misplace or forget your new URL, you’ll need to initiate a site-access recovery procedure.
- Users who have whitelisted their IP address in Shield Security PRO will not experience these changes. To activate the hidden login page settings, these users must remove the whitelist restrictions.
2. Setting login attempt cooldown times for enhanced protection
Safeguarding your site before a threat emerges is far more effective than responding to an attack. Setting up a cooldown period for login attempts is a simple yet effective measure that can substantially protect your site from brute-force attacks.
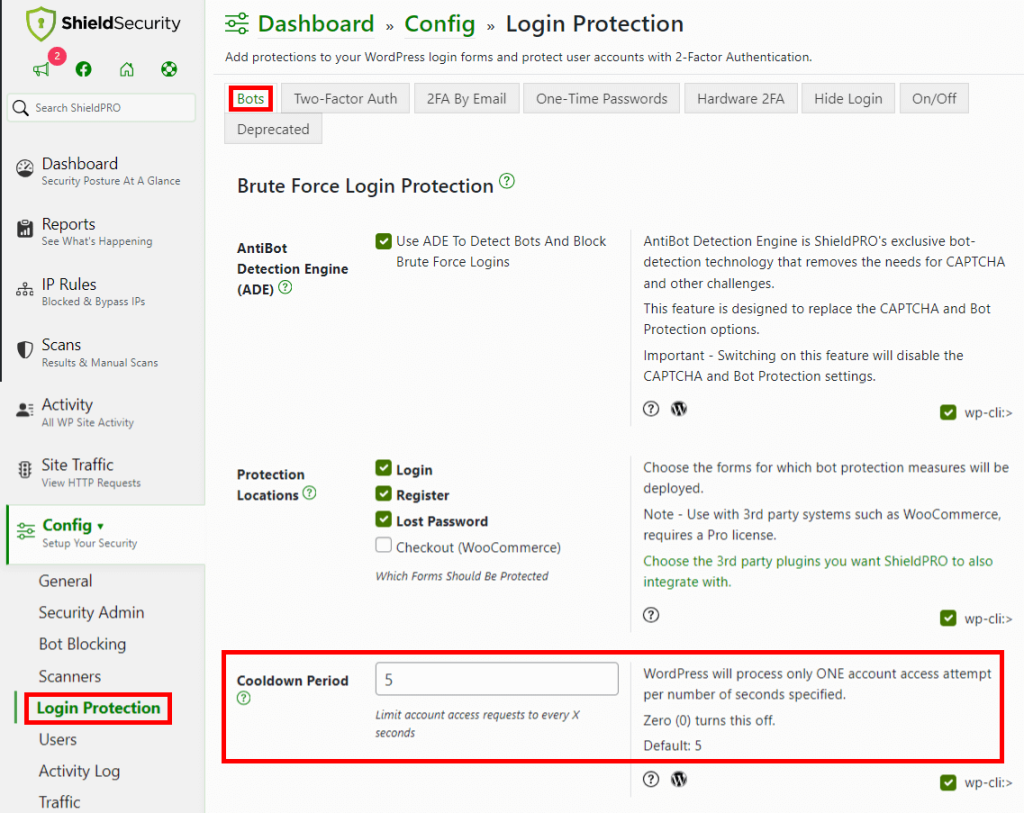
By setting up a cooldown period, you restrict your WordPress site to process only one login attempt during the designated timeframe. This approach throttles bot attempts and enhances your site’s safety.
Let’s think about a bot that’s engineered to fire off ten login attempts per second. Without a login cooldown in place on your site, the bot would be relentless, launching a million-attempt attack on your site in less than two days.
However, with a mere five-second cooldown period in place, it would take the bot nearly 60 days to make the same number of login attempts, making it a less viable threat.
When determining the length of your cooldown period, remember to consider the impact on user experience. If your site has a limited number of users logging in, a relatively longer cooldown period should work just fine.
On the other hand, if your website is highly frequented with numerous login attempts, it might be a good idea to opt for a shorter cooldown period. This mitigates the risk of login blocking due to multiple users trying to access the site at once.
Under normal circumstances, the odds of multiple legitimate users attempting a login at the exact same moment are pretty small. However, during periods of high traffic, such as sales or new product launches, you might observe a surge in simultaneous activity.
Remember, you can always adjust your cooldown time as needed to strike a balance between security efforts and user experience.
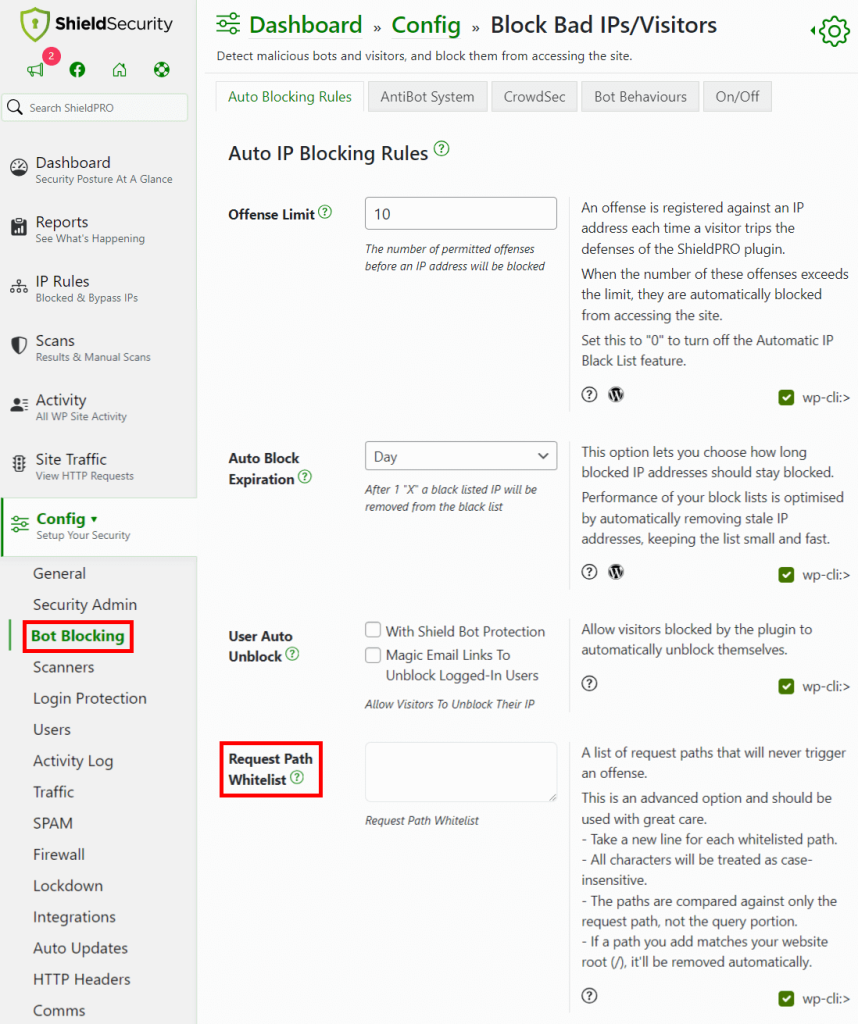
3. Identifying and blocking malicious site visitors
Bad bots are an unfortunate reality in today’s internet landscape. If one targets your website, it can bombard it with repeated login attempts and act as a persistent security menace.
Making it more challenging for bots to access your site or login page could significantly decrease their impact on your site’s performance.
Shield Security PRO is able to identify recognizable bot behavior, which provides an essential defense line. Recognizing the unique behavior patterns of these bots on your site, Shield Security PRO identifies bots and moves to block the related IP addresses, safeguarding your site entirely.
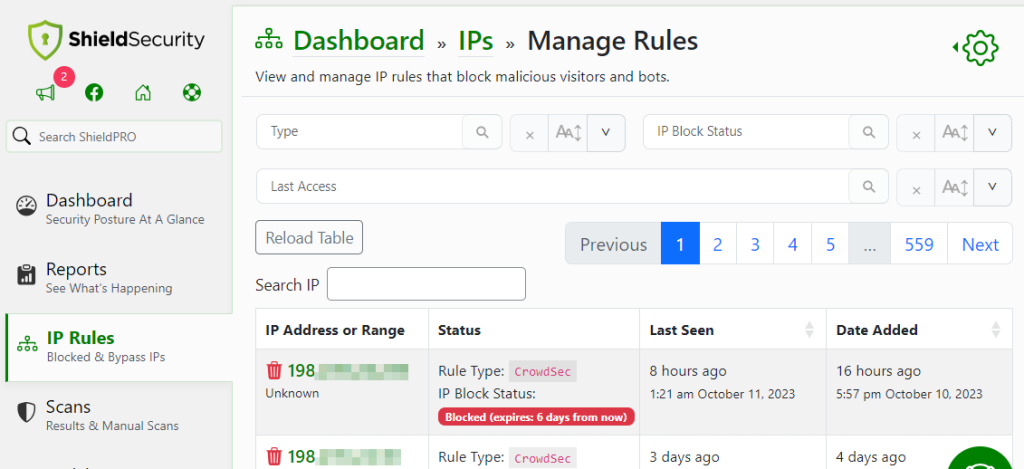
On the flip side, there may occasionally be instances where legitimate IP addresses are inadvertently flagged as bots. Shield Security PRO manages this by letting you moderate blocks and whitelist users who should have access to your site.
4. Boosting security with two-factor authentication
Two-factor authentication (2FA) is an extra layer of security that requires users to verify their identity using a secondary method, over and above their password. The secondary method is typically a unique code sent via email, text message, or retrieved from an app.
Designed specifically with WordPress site security in mind, Shield Security PRO comes equipped with a built-in 2FA system. It provides options to send the code to users’ email addresses or synchronize with Yubikey and Passkeys.
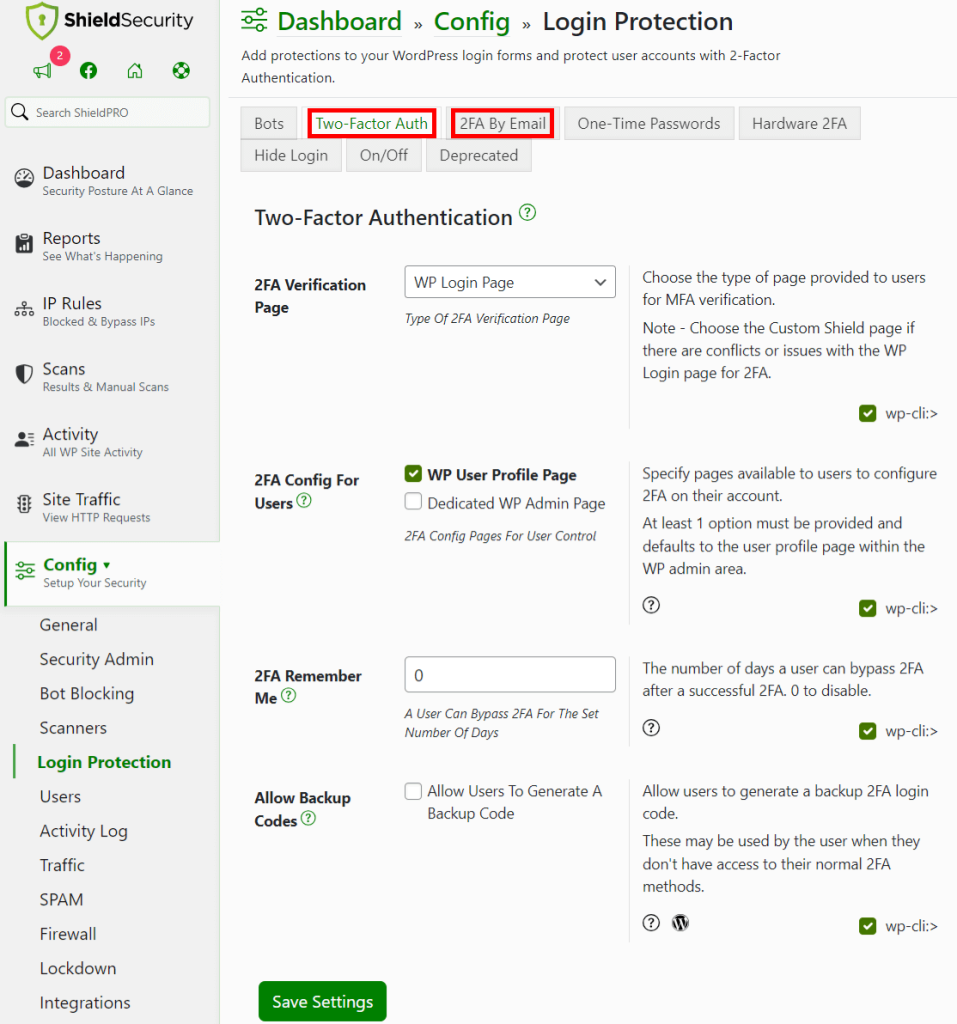
The advantages of implementing 2FA in your security practices include:
- Placing a hard stop on brute force attacks by bots, who won’t know their login attempts are falling short.
- Efficiently blocking attacks based on leaked passwords, giving you the upper hand over cybercriminals who don’t have access to the secondary identification method.
5. Enforcing strong passwords and security best practices
People tend to create passwords that are easy to remember, but these aren’t always complex enough to withstand attacks. Without guidelines, users might create passwords that lack a mix of uppercase and lowercase letters, numbers, and symbols.
This vulnerability has long troubled security experts. For ages, the most commonly used password was, notoriously, ‘password’. Since many sites have started to force users to include at least one number, there’s a new most common password in town: ‘password1’. It’s hardly an improvement to the situation.
With Shield Security PRO, you can establish a required strength level for new passwords. This metric is determined using the zxvcbn password strength calculator.

You should encourage users to select login credentials that are distinct from those used on other websites. This is important because if an attacker gains access to an account on one website, they may try the same username and password combination on other websites. By using unique credentials, users can mitigate this risk and keep safe from brute force or dictionary attacks.
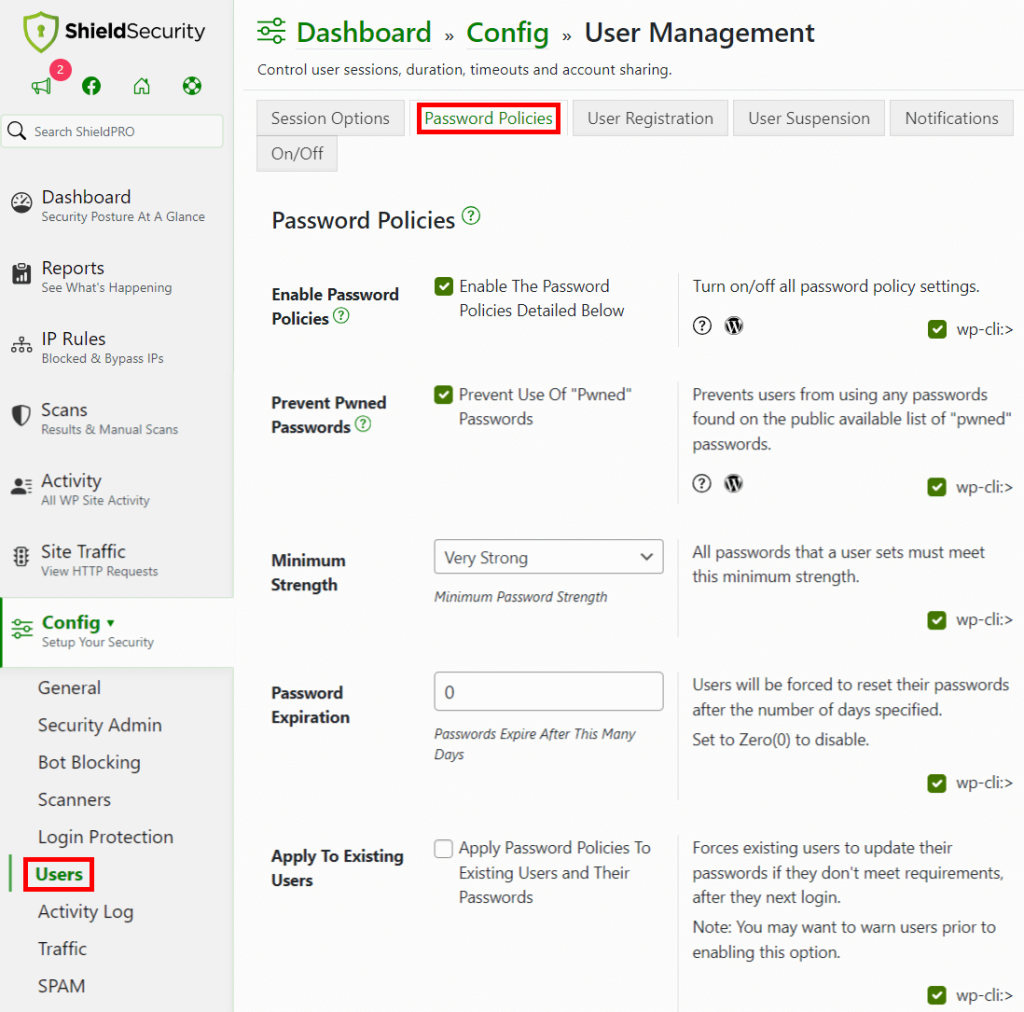
Shield Security PRO further empowers you to block “pwned” passwords, which are passwords exposed in famous data leaks, to add an extra layer of protection against potential threats.
Remember, your site is only as secure as your least secure user. That’s why you should keep the following in mind:
- Teach users how to recognize phishing attempts and counterfeit login pages.
- Warn users to never disclose their password or 2FA codes to anyone.
- Regularly provide security training to keep users aware of emerging scams, new technologies, and other tactics that those with malicious intent might use to break into your website.

6. Regular user account reviews and cleanup: a routine for safety
Regular user account reviews and cleanup are essential components of a digital security routine. You should periodically assess user accounts within your system to mitigate both internal and external threats.
For example, you should promptly remove login credentials for employees who are no longer associated with your organization. Don’t wait; do this immediately upon the termination of their employment contract. This reduces the risk of disgruntled former employees misusing their access privileges, so you can protect your data and systems.
You should also scrutinize existing user accounts for outdated permissions. For example, if you’ve granted someone temporary administrative access to address a specific issue on your platform, remember to revoke these privileges once the problem has been resolved. Failing to do so creates unnecessary vulnerabilities in your system, as the user no longer needs that level of access.
Regular user account reviews also help defend against external threats. Inactive user accounts should not stay on your site, as they present potential security risks – after all, if someone hacks that account, there’s no active legitimate user to notice the problem. Consistent permission reviews create a more secure digital environment.
Build this practice into your routine security audit process to ensure that your users are always up-to-date and in line with your organization’s needs. This proactive approach to user account management fosters a safer and more secure online ecosystem.
Next steps: Enhancing security with Shield Security PRO
The tips in this article will help you to reduce vulnerabilities and amplify your site’s login page security.
But why limit your security measures to just your login page? With Shield Security PRO, you can improve security across your entire site.
Equipped with cutting-edge features such as precise bot detection, diligent traffic rate limiting, and thorough malware and vulnerability scanners, Shield Security PRO arms your website for holistic security. These advanced tools work together to secure your WordPress site effectively and conveniently.
Don’t wait until it’s too late to fortify your WordPress website. Safeguard your WordPress login page with Shield Security PRO now and embrace a secure and reliable future for your site!



