- Part 1: Why we built the Shield
- Part 2: WordPress Super Admin Protection
- Part 3: WordPress Firewall Feature
- Part 4: WordPress Login and Brute Force Hacking Protection
- Part 5: The WordPress Comment SPAM Killer
- Part 6: WordPress Automatic Updates Management
The Firewall Security Zone is just one part of the whole Shield security system.
In this part of the series we’ll detail what exactly the firewall is, what it does, how it works, and how you should configure it.
What is the WordPress Firewall and how does it work?
The firewall component of the plugin is an Application Level Firewall.
This means it only acts, and can only act, at the WordPress level. It does not, and cannot ever, affect lower levels on the server. It can never block incoming connections from IP addresses and/or to ports on the server. No WordPress plugin can do this.
No WordPress plugin can do this, no matter what they tell you.
We don’t write to the core .htaccess files on principle, so we don’t affect how Apache handles web requests. Instead, we examine the data in these requests and then allow or block WordPress from loading depending on the rules you have chosen.
The plugin analyses the information contained within the GET and POST data sent to your site. This is explained in more detail here.
When it detects something that it doesn’t like – it’ll kill that web request and prevent WordPress from loading any further.
In this way, it prevents WordPress from receiving/using malicious data that’s been sent to it to for the purpose of causing trouble.
Understanding the Firewall Security Zone options
The firewall component of the plugin has a number of options associated with it. Below is an outline of these to help better understand each section:
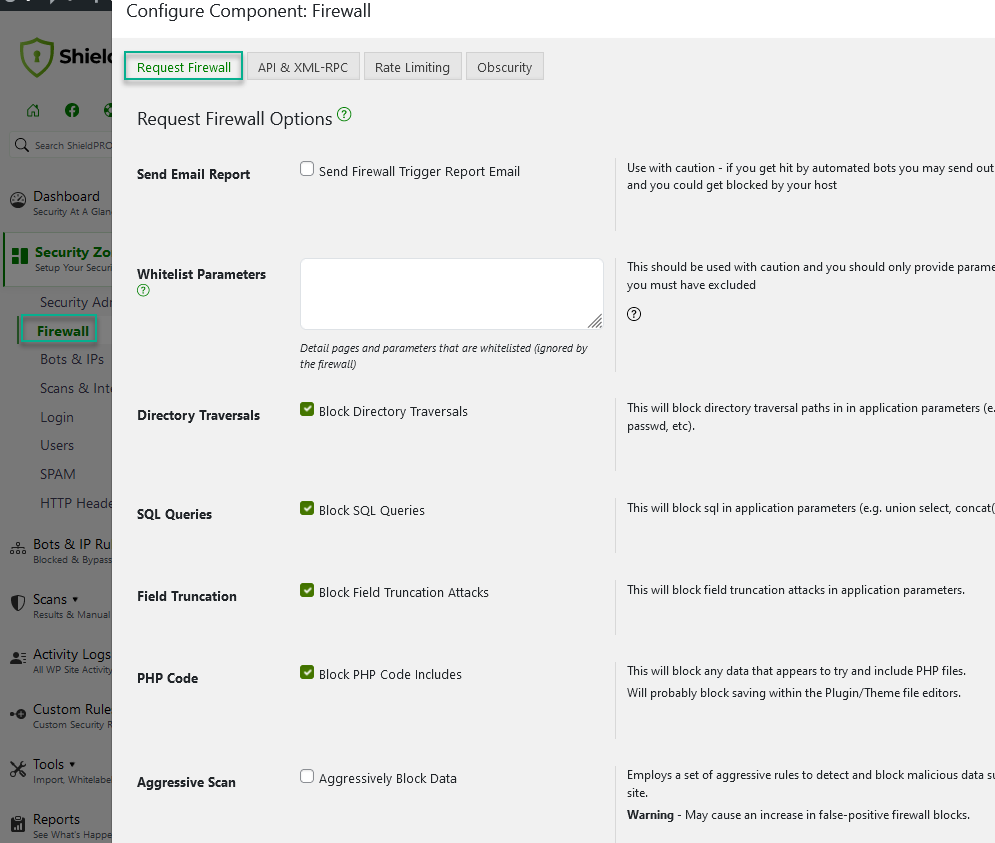
Request Firewall Blocking Options
There are 5 firewall options that determine what data is checked on each page request. Depending on certain incompatibilities with other plugins, you may need to disable certain options to ensure maximum compatibility.
Here are just a few of them:
Directory Traversals: Default – On. There is typically no need for file paths that indicates attempts to move between directories on the filesystem. Be careful, as this might interfere with sites that publish content containing code snippets – it might be an idea to use the “ignore administrators” option mentioned above.
SQL Queries: Default – Off. This will block sql in application parameters (e.g. union select, concat(, /**/, ..), etc).
Field Truncation: Default – On. Much like file system traversals, you typically shouldn’t have SQL queries in data submitted to your site. This option will try to look for keywords and patterns associated with SQL queries.
PHP Code: Default – Off. Again, just like SQL, WordPress terms etc., you typically shouldn’t have PHP code in data submitted to your site. If you use the plugins/themes editor, this might trip the Firewall checks.
Aggresive Scan: Default – Off. Employs a set of aggressive rules to detect and block malicious data submitted to your site. May cause an increase in false-positive firewall blocks.
Send Email Report Option
This option specifies how the plugin will respond when the firewall detects malicious data.
When enabled, it will send the administrator an email notifying them of a firewall block incident.
We recommend to keep this turned off. There is just no need to bother with these notices. It’s useful however when you are debugging the firewall when you suspect interference with/from other plugins.
Firewall White Listing Option
It’s possible to specify certain factors that completely by-pass all Firewall checking.
This option should be used sparingly and with caution since you never want to white list anyone, even yourself, unless you really must.
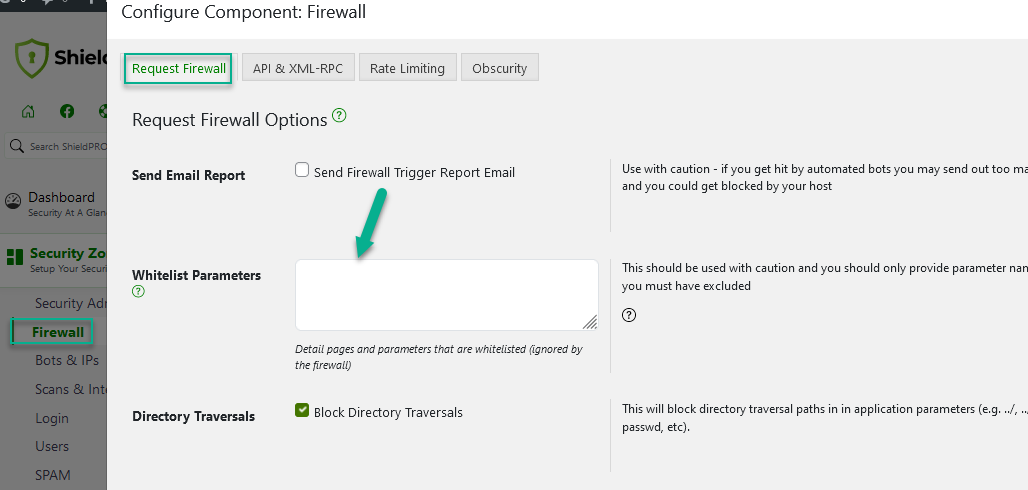
Whitelist Parameters: This is an advanced setting where you can by-pass the firewall for a given page such as ‘hello.php’, or by-pass the firewall for a given parameter sent to that page. This is useful where certain pages/plugins submit data that you always want to leave untouched by the firewall.
In general, there is no need to white list anything unless there is a compatibility issue to deal with.
API & XML-RPC Options
The WordPress API & XML-RPC options purpose is to lockdown certain core WordPress system features.
Recommendation: This depends on your usage and needs for certain WordPress functions and features.
Brute Force Traffic Rate Limiting Options
The Traffic Rate Limiting feature helps you to put a stop to bots and visitors that abuse your website and your hosting resources.
You can restrict the number of requests a single visitor can make against your site, within a certain period of time.
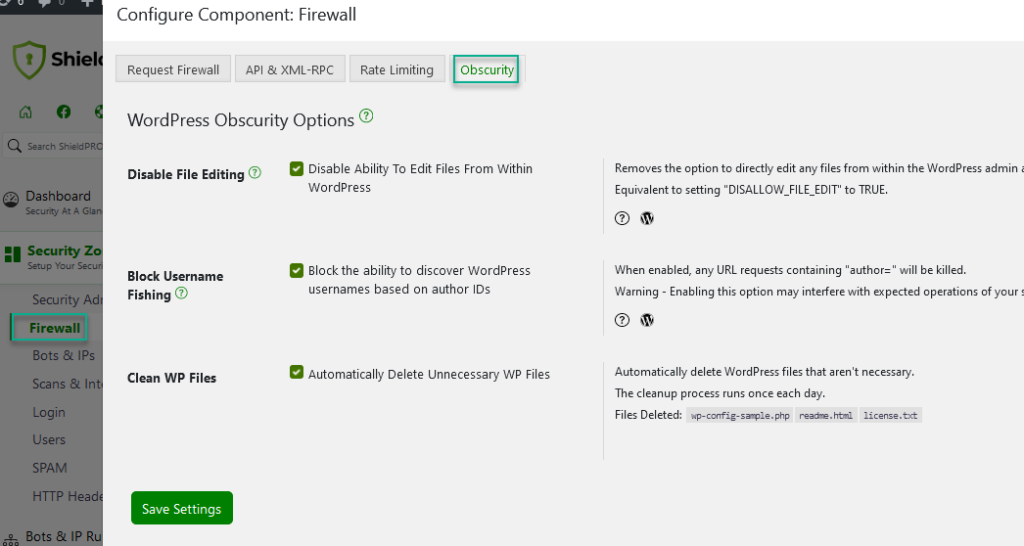
WordPress Obscurity Options
The WordPress Obscurity options obscure certain WordPress settings from public view.
Here you can
- Disable File Editing
- Block Username Fishing
- Clean WP Files
WordPress Firewall Security Zone Summary
As you can see, Shield’s Firewall component is full-featured and easily customized to fit as many site configurations as possible.
Firewall checking begins right after all site plugins are loaded and before WordPress really begins to kick-off. Of course, adding all this checking to every page request adds extra processing, but we’ve written the firewall component (just like the rest) to be as efficient as possible and to only scan where there is data to process.
If you have any questions about the firewall, or wish to request some features, please drop us a message in the comments section below, or contact us in our support centre.



I have used Jetpack to secure my website. Is my website still need a Firewall plugin such as iControlWP? I’m sorry if you find any mistakes in my English.
JetPack is not a security plugin… there is a lot of functionality supplied within Shield that is not provided in JetPack – they are 2 totally different plugins.
Thanks!
Any idea why navigating to this page: http://askwpgirl.com/how-do-i-set-up-rss-feeds-on-my-wordpress-website/ from a google search got me blacklisted?
will be better if ishield will have a 404 error blocking system as wordfence and ithemes – so if someone hit many 404 error in a short time to be blocked
Hi George,
Shield does have this option – you’ll find it under the IP Manager module. It is a Pro-only feature so you’ll need to upgrade to access it. But at $12/year, it’s not a lot… and you get all the other Pro extras too 🙂
Thanks,
Paul.