Our lastest ShieldPRO 14.1 security plugin for WordPress brings a huge WordPress REST API integration along with some much-needed tweaks and enhancements.
Read on to discover everything we’ve included in your newest and favourite WordPress Securty Plugin.
#1 Full Integration With WordPress REST API
Management of WordPress websites at scale is a huge challenge for all of us.
Consider the work that’s involved with managing just 1 WordPress site and all its plugins, themes, updates, backups and, of course, security.
Now multiply that by the number of WordPress sites you run.
It’s a huge amount of work.
This is why we built iControlWP many years back and why we also integrated Shield Security into it to allow WordPress admins to manage their WordPress sites at scale, and also their WordPress security.
But not everyone wants to use iControlWP and that’s totally cool! But we still want to open up management of Shield to folk that need to scale their WordPress security.
This is where our new WordPress REST API integration comes in. It leverages the very thorough platform that the WordPress Core provides, letting us build a REST API that is powerful, secure and easy to maintain.
Many clients won’t have a need for our REST API directly, but you may use tools and services that could take advantage of if you asked them to.
#2 Hugely Improved Activity & Traffic Logs
This is a big one.
A short time ago we completely overhauled the Activity and Traffic Logging features.
This involved a major revamp of the UI and the tables that display the logs.
As you can imagine, these tables and data set can grow very large, particularly for busy websites.
Since we were loading a large dataset all at once, browsing these log tables became tedious and slow. For high traffic sites, it would unusable in some cases resulting in loading errors!
So we went back to our core implementation (again) and made the entire thing dynamic. Instead of loading all the records, we only load precisely what we need. This makes the initial loading near-instant.
The pagination will be a bit slower than what you’re used to – but this is because we’re loading just the log records you need, when you need them.
We’ve also adjusted the traffic log database table structure to help us speed all this along and provide more useful information right where you need it.
This is a major reworking and we hope you’ll love it!
#3 Run Shield As A “Must-Use” (MU) Plugin
If you’ve never heard of a must-use WordPress plugin, don’t worry, you’re not alone.
Simply put, a must-use WordPress plugin is one that is automatically enabled and always loads when WordPress loads. These special plugins can’t be (easily) disabled and execute before all other plugins.
They’re installed in a different directory (/wp-content/mu-plugins/) instead of the default (/wp-content/plugins/).
So why would you want to switch Shield to be an MU plugin?
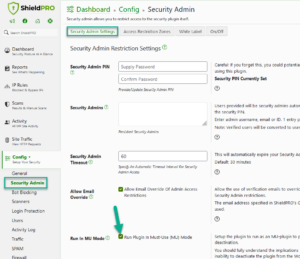
In much the same way as Shield offers the Security Admin module to protect against tampering, you could set Shield to be an MU plugin to prevent the plugin from being disabled accidentally, maliciously.
It’ll also ensure Shield executes before other plugins. While this won’t offer an advantage currently, we’ll soon adjust some Shield’s code to block malicious requests much earlier in the WordPress load.
What actually happens when you enable MU Mode?
The core of the Shield plugin will remain in the normal installation directory- /wp-content/plugins/.
Shield will then create a new file in the MU directory that loads the normal Shield plugin. When this happens you’ll see 2x Shield plugins installed on your site as shown below:
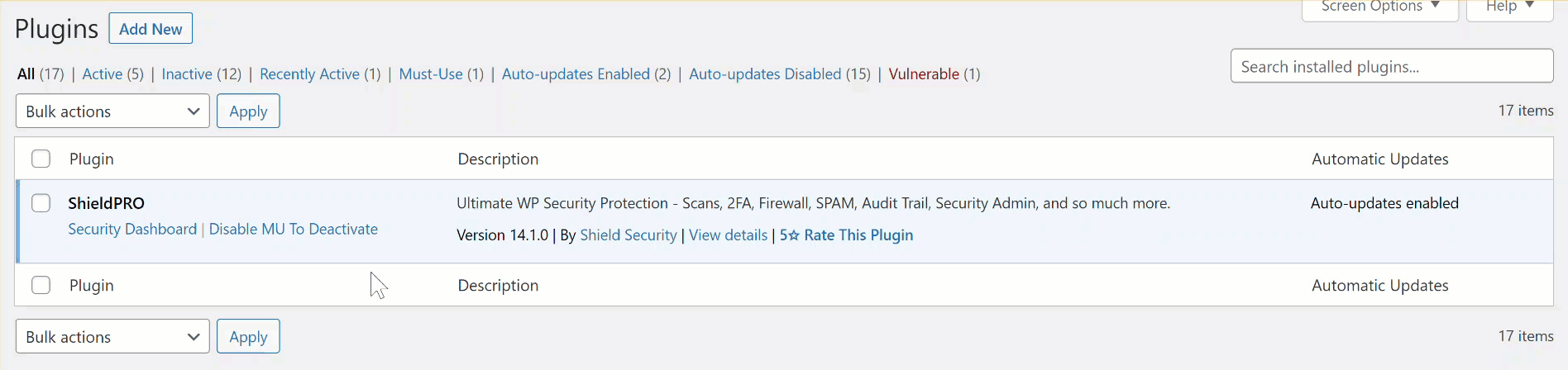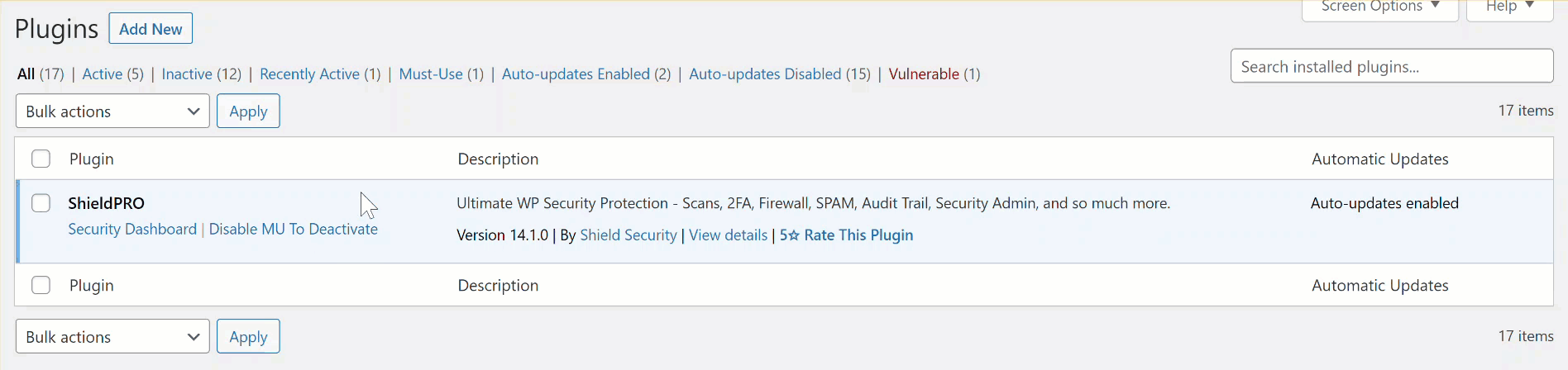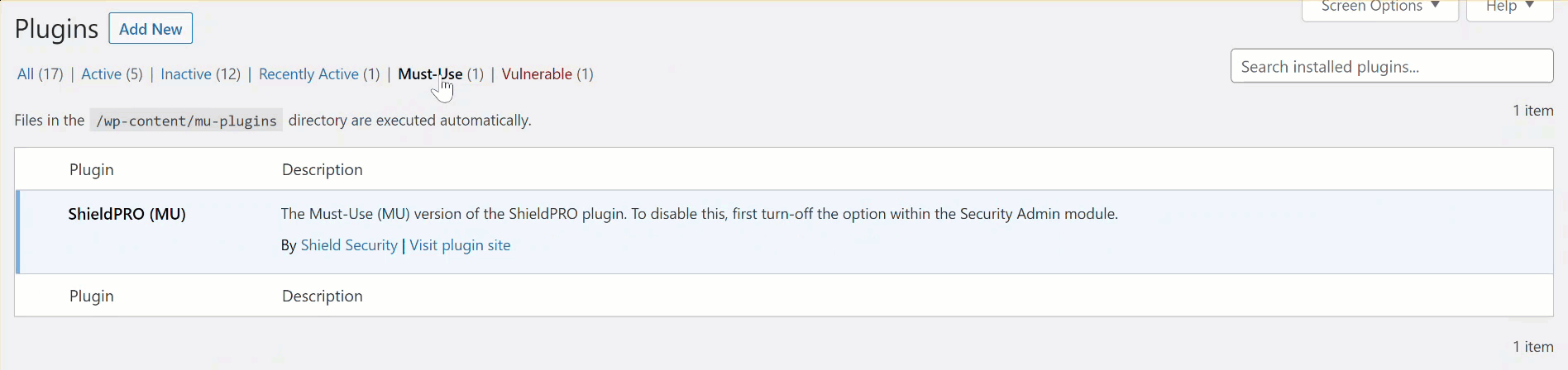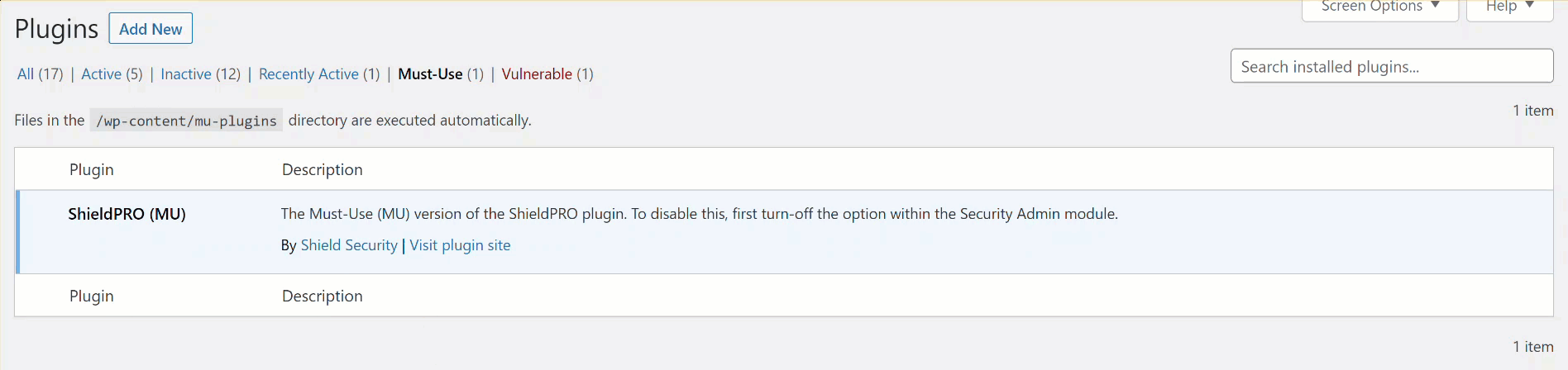
How can you disable Shield after enabling MU Mode?
Once MU mode is enabled, you can’t disable the normal Shield plugin from the WordPress dashboard. This is normal WordPress behavior.
However, you can simple revert the option within Shield’s settings to disable MU Mode, and then return the plugins screen and disable Shield like any other plugin.
The setting for MU Mode is found within the Security Admin module and doesn’t require a Security Admin PIN to be set.
#4 Better Detection Of Incorrect Application Passwords
Following a suggestion from a client and also off the back of our REST API work we’ve improved how Shield captures and logs authentication failures when Application Passwords are used.
Until now Shield wasn’t correctly spotting when these application password login attempts were failing. We’ve added some new events and logging and we’ll even increase the offense counter for an IP address when the event is triggered.
We spotted these new events being triggered almost immediately after we put them live for testing.
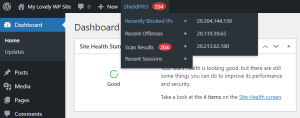
#5 More Quick Access Data In Admin Bar
Some time ago we add a top menu to the WordPress admin bar to help indicate when Shield found some scan items that warrant further investigation.
After prompting for some extra information by a client, we’ve made some new helpful additions to the menu (see image below).
Each of these additions provide helpful links to the item in question, for example:
- Recently Blocked IPs and Offenses link to the IP Analyse Tool for the specific IP in-question.
- Recent Sessions links to the Shield Sessions table and the individual session item in the menu links to the profile of the given user.
Comments, Questions & Suggestions?
We’ve packed a lot of new things into this release. We think this is our best release yet for Shield Security, but as with anything that changes, there will be questions and feedback.
Please feel free to use the comments section below to drop us a message or question if you have any. Thanks as always for your support!



Hello. I’ve been using Shield for several years, thank you for a great plugin. I especially love the 2FA options.
Lately I’ve been getting dozens of ”Bruteforce Attack” notification emails a day and it gets a bit tiresome, since there is nothing I can do about it. I was unable to find any option to turn them off. Please tell me it is possible.
Hi Tudor,
Thanks so much for such nice words about our plugin. We are glad to know that you are happy with it. 🙂
Notification emails can be very annoying indeed, which is the reason why we notify you only when that’s really necessarily. We don’t send alert notification emails for every single brute force attempts or anything like that. Instead, we have Reporting section where you can configure it on how often to receive a Summary Info Report (stats) about the most recent plugin security actions taken on your site.
Speaking about brute force attacks in general, Shield is ideally positioned to protect your site from these. It comes with many mechanisms which handles them easily with no effort on your part, and no degradation in your site performance.
One of the simple powerfully brute force protection mechanism is the “login cooldown”.
This option enforces a cooldown period after each login attempt – the default is 10 seconds. This means that after you login, you must wait 10 seconds before WordPress will even consider allowing any other request to login.
Another powerful brute force protection is our AntiBot System. This is the ideal solution to combat bad bots.
With the these 2 alone, you’re protected by brute force attacks before you’ve employed any other protection options.
Apart from that, we have various bot attack prevention options (under the Login Guard and Block Bad IPs/Visitors modules).
Plus, if you’ve turned on 2-factor authentication, then you’ll be safe.
When you are experiencing brute force attacks and unsure what Shield settings to review to improve protection, best is to use your Audit Trail and analyze bot signals through IP Analysis section. Here you’ll get the all information about that bot activities and act if necessarily.
To provide a further detailed help on how to do this, we created a support ticket for you (ID 1763). Please check your inbox for the email address you used to submit the comment on this blog post and respond when you have a chance.
Thanks,
Jelena
Hello Jelena, and thank you for your reply.
I think I have not succeeded in stating what I really wanted. I think my settings are fine, both the AntiBot settings and the login cooldown. At least they seem to be doing their job successfully.
The problem is that my site is periodically bombarded by login requests from what appears to be a distributed botnet, which just stupidly tries different (non-existing) usernames and passwords. When this happens, I start getting warning emails listing offending IPs and what usernames they tried (the email contains also a password field which is never populated). The attack sometimes lasts multiple hours and up to a whole day, and when this happens I get A LOT of these emails.
I have changed the Alert frequency setting from ”Hourly” to ”Daily” and it seems my problem is now solved, I get a lot fewer emails. But I still think the settings are not granular enough and I should be able to just disable the notification for Bruteforce Attacks, since they do not require my immediate attention or intervention, they just slightly increase my stress levels.
Anyway, thank you again for your reply. And thank you to the whole team for a great plugin.