Cross-Site Scripting (XSS) attacks remain a persistent threat to WordPress sites. While modern browsers embrace the sleek sophistication of Content Security Policy (CSP), legacy browsers – yes, people still use them – cling to the deprecated X-XSS-Protection header.
For WordPress site owners juggling compatibility with both modern and older systems, configuring this header is less about elegance and more about brute pragmatism.
We’re going to cut through the noise and show you exactly how to set up X-XSS-Protection, whether through manual .htaccess edits, Shield Security PRO’s simplified tools, or a rigorous testing workflow.
TL;DR Yes, it’s deprecated. No, you can’t skip it. Legacy browsers don’t care about being cool – they just need things to work, and it’s your job to make sure they do, without compromising security.
What is XSS and what are the common XSS attacks?
XSS is a security vulnerability that allows attackers to inject malicious scripts into websites, turning them into unwitting accomplices in attacks on their own users. The script executes in the victim’s browser, stealing data, hijacking sessions, or doing whatever else the attacker wants. It’s a failure to tell untrusted input to stay in its lane.
Persistent XSS is the nuclear option. The malicious script gets stored on the server – usually in a database – waiting for victims to stumble upon it. Think of a poisoned comment section where every user who reads it gets hit by a malicious JavaScript payload. It’s insidious because it doesn’t rely on anyone clicking a sketchy link; the attack is baked into the content, ready to fire.
Non-persistent (reflected) XSS is more opportunistic – think phishing emails with a payload hidden in a URL. When a victim clicks the link, the malicious input gets “reflected” back by the server, executing in their browser. It’s quick and dirty, relying on tricking the user in the moment rather than embedding itself in the system.
DOM-based XSS is a browser-side vulnerability where the attack happens entirely within the user’s browser, specifically in the page’s structure (the DOM). It occurs when JavaScript on the site doesn’t handle user input carefully, allowing attackers to inject malicious scripts that change how the page works for the user. Unlike other forms of XSS, this doesn’t involve the server, making it sneakier and easier to miss.
How to protect against XSS attacks in WordPress
Protecting your WordPress site from XSS attacks requires understanding where your vulnerabilities lie and how to shut them down at the base level.
First, sanitise everything. If you’re accepting user input – comments, forms, custom fields – you need to use WordPress’s built-in functions to strip out anything unexpected. Use sanitize_text_field() for text, sanitize_email() for emails, or esc_url() for URLs.
Next, escape your output. Whenever you’re displaying user-provided content on your site, make sure it’s escaped to prevent execution of malicious scripts. Use functions like esc_html() for HTML, esc_url() for links, or esc_attr() for attributes depending on the context. If you’re echoing anything directly from user input, you’ve already lost.
Third, lock down permissions. WordPress has a built-in capability system for a reason. Restrict editing permissions to only those users who absolutely need them. If you let everyone and their dog have access to post HTML, you’re practically rolling out the red carpet for an attacker.
Finally, harden your site’s settings. Disable file editing through the admin panel by adding define('DISALLOW_FILE_EDIT', true); to your wp-config.php file.
Limit what can be uploaded by tweaking MIME types in functions.php:
function restrict_mime_types($mimes) {
unset($mimes['exe'], $mimes['php']);
return $mimes;
}
add_filter('upload_mimes', 'restrict_mime_types')
XSS is a direct result of laziness or ignorance. If you know how your site handles input and output, you can stop XSS before it ever becomes a threat. For those looking to future-proof their sites, implementing a Content Security Policy can add an extra layer of defence, ensuring that even if malicious scripts slip through, they’re blocked from executing.

Understanding Content Security Policy (CSP) as the preferred solution
CSP is the web’s “do not disturb” sign for malicious scripts. Unlike patchwork fixes like sanitising inputs or escaping outputs – necessary but reactive – CSP puts you in control by explicitly defining what your browser can and can’t execute.
XSS attacks thrive on unpredictability. A stray user input, an unescaped output, or a lazy file upload can give attackers the foothold they need. CSP removes that unpredictability by letting you dictate which sources of scripts, styles, and other resources are trusted. Even if malicious code sneaks onto your site, a properly configured CSP blocks it before it has a chance to run.
And implementing it is simpler than you think. Add a Content-Security-Policy header to your server configuration or use a <meta> tag in your HTML. Start with a “report-only” mode to identify violations without breaking functionality.
Add the following code to your header:
Content-Security-Policy-Report-Only: default-src 'self'; script-src 'self' https://trusted-cdn.com; report-uri /csp-report
Once you’re confident, switch to enforcement mode to lock everything down:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted-cdn.com;
If you care about your site’s integrity, stop relying solely on old-school XSS defences and start defining the rules of engagement with CSP.
How Shield Security PRO delivers complete XSS protection
Shield Security PRO fortifies your WordPress site against XSS attacks through a multi-layered approach centered on HTTP security headers. It configures them to instruct browsers to block potential reflective XSS attacks, enhancing default browser protections.
The security plugin also enables the implementation of the CSP header, which restricts the loading of resources like JavaScript and images, thereby mitigating potential threats. This allows users to set custom CSP rules within the plugin, providing granular control over which resources can be loaded or executed on your site.
Furthermore, Shield Security PRO offers control over iFrame behavior through the X-Frame-Options header, allowing users to prevent their site from being embedded into malicious iframes, which can be a vector for XSS attacks.
Configuring Shield Security PRO’s advanced security headers: Step-by-step guide
Setting up security headers in Shield Security PRO is as easy as opening the Security Dashboard, then going to Security Zones > HTTP Headers.
Here, you’ll see two options: Basic HTTP Headers and Advanced Content Security Policy (CSP) Headers. Click the gear icon next to each option to configure it.
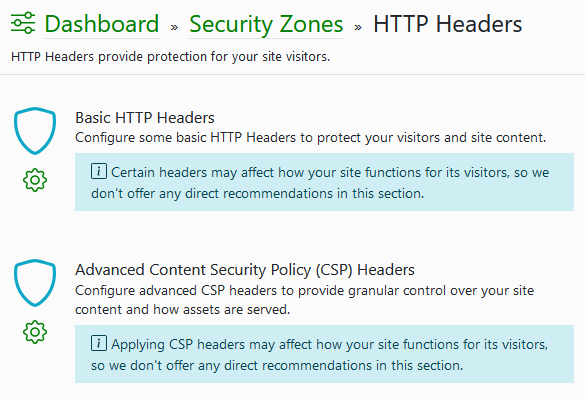
Under Basic HTTP Headers, your options are as follows:
- Block iFrames, which controls whether or not external websites can embed yours in an iFrame.
- XSS Protection, which engages built-in browser security tools.
- Prevent Mime-Sniff, which ensures browsers only process files based on their declared content type, blocking malicious files disguised as safe ones.
- Referrer Policy, which allows you to control the referral information your browser shares when links on your site are clicked.
Under Advanced Content Security Policy (CSP) Headers, you can turn on CSP and configure rules for how it operates.

Many WordPress caching plugins ignore HTTP headers, so you may need to disable caching to see the rules take effect.
Implementing CSP and modern headers with Shield Security PRO
As we’ve stated above, CSP rules give you fine-tuned control over how your site’s content and assets are served, but it’s not a plug-and-play solution.
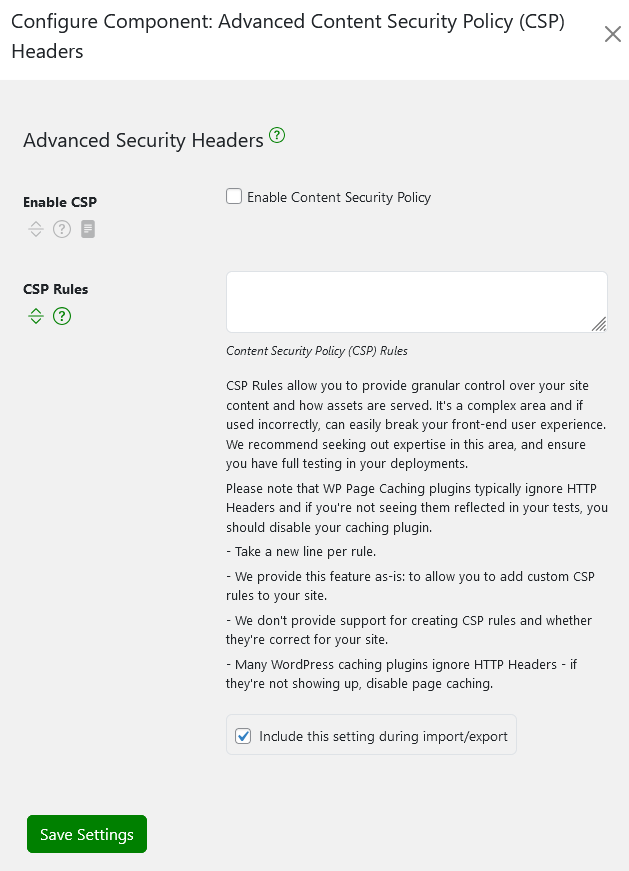
Misconfigured rules can break your frontend, so you’ll need to run rigorous tests and get expert input to avoid disruptions.
WordPress caching plugins often ignore HTTP headers, meaning your changes might not show up in tests. Try disabling your caching plugin to resolve this.
This feature is provided as-is, allowing you to add custom CSP rules to your site, but Shield Security PRO doesn’t offer support for crafting or validating these rules. If you’re implementing CSP, take the time to test thoroughly and understand the impact on your site.
Testing your WordPress XSS protection configuration
You can have the best setup in theory, but if your headers aren’t doing what you think they are, it’s all smoke and mirrors.
Start with tools like securityheaders.com, which analyse your site’s HTTP headers and show whether your X-XSS-Protection, Content Security Policy (CSP), and other defences are actually in place. It’s quick, free, and brutally honest about your site’s vulnerabilities.
To give you an idea of what to expect, this is what the security header report for YouTube.com looks like:
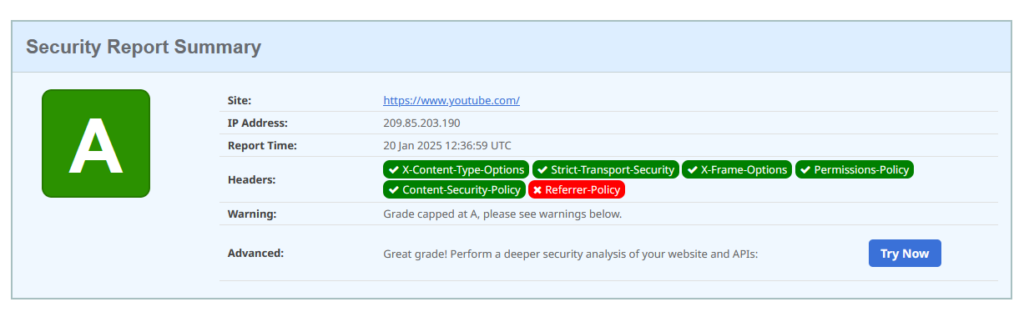
Here’s something you should be aware of: most WordPress caching plugins – yes, even the big-name ones – don’t reliably honour security headers. When they serve cached pages, your carefully configured headers often go missing. That means your XSS protection might not be working for a significant portion of your users. Test your site both with and without caching enabled to see if your headers are consistently applied.
Don’t trust assumptions or plugins to do the work. Test your configuration thoroughly and ensure your caching setup doesn’t undo everything you’ve implemented.
To verify further, use your browser’s developer tools, specifically those under the Network tab, to check for your security headers in real-time. Look for X-XSS-Protection, Content-Security-Policy, and Strict-Transport-Security. If they’re not there, you might have a problem on your hands.
Upgrade your WordPress security with Shield Security PRO
XSS is one of the most common ways attackers can exploit vulnerabilities in your WordPress site. Shield Security PRO takes this threat seriously by providing a complete suite of tools to harden your defences.
From implementing HTTP security headers like CSP and X-Frame-Options to blocking malicious scripts with XSS protection, Shield Security PRO ensures your site stays secure without compromising performance.
Security isn’t static, though. It’s an ongoing process that requires the right tools and proper configurations to work effectively. Shield Security PRO gives you control, with granular settings to manage how your site interacts with browsers and content.
Don’t wait for a breach to take action. With Shield Security PRO, you can safeguard your WordPress site from XSS attacks and other vulnerabilities, all while maintaining the flexibility and usability your visitors expect. Upgrade your site’s security today!


