Phishing is a form of cyber attack where malicious actors trick individuals into revealing sensitive information, such as passwords or financial details, by pretending to be a trustworthy entity. For WordPress sites, phishing poses a significant threat, potentially leading to data breaches, loss of customer trust, and severe financial damage.
Phishing scams targeting WordPress sites generally fall into two categories:
- Hosted scams: These involve malicious software or spam comments on your website, tricking your users into divulging sensitive information.
- Direct attacks: These scams are aimed at you or your business, with the intent of gaining access to your site.
We’re going to give you easy ways to find, delete, and stop them, using Shield Security PRO. If you follow these rules, you can keep your WordPress site safe and make sure your users can continue to trust and rely on you.
Identifying, removing, and preventing hidden phishing content on your WordPress site
Phishing scams can be insidious, often hiding within the code of your WordPress site. We want to help you learn how to find, delete, and stop phishing content to make sure your users stay safe.
Identifying hidden phishing content
The first step in combating hidden phishing content is to identify it. Start by running a full sites scan. While numerous plugins are available for this purpose, we recommend using Shield Security PRO, powered by MAL{ai}, to perform a full-site file scan. It uses machine learning to help it detect up to 80% of never-before-seen malware.
MAL{ai} scans all files on your WordPress site, flagging any suspicious ones for your review. This approach ensures that potential threats are identified quickly, so you can take corrective action before significant damage is done.
Removing malware
Once malware has been identified, it’s important to remove it quickly. Shield Security PRO offers an automatic repair tool that replaces infected files with clean versions from a blank WordPress installation. However, please be cautious. Automatic repair can undo legitimate changes if the malware has infiltrated intricate parts of your site’s code, such as theme files or function definitions.
Dealing with malware on a site can be a little complicated, and while Shield Security PRO can help identify the malicious code, if you have any doubts, seek help from a professional developer.
If the malware created pages on your site to host phishing attacks, be sure to thoroughly review your website to remove any unauthorised pages or content. Phishing pages are designed to deceive visitors into divulging sensitive information. Conduct a comprehensive review of your site to spot these malicious pages and delete them as soon as possible.
Shield Security PRO’s Snapshot technology will highlight changes in posts or pages in its regular security reports, so you can use these to help you spot nefarious changes.
It’s crucial to also check your server logs and database for any signs of unauthorised access or changes made by the malware. By taking these steps, you can mitigate the damage caused by the phishing attempts and prevent further compromises to your site’s security and reputation.
As mentioned earlier, manual cleanup of complex malware infections may be necessary. If you’re not confident in this, consider hiring a professional to make sure the job is done thoroughly.
Managing spam comments
Phishing scams can also manifest in spam comments on your site. Regularly review incoming comments to spot any suspicious activity. To reduce the risk of phishing attempts and spam comments:
- Limit comments: Only allow comments on posts where it is truly necessary.
- Monitor and approve: Set comments to require approval before they appear on your site.
- Use Shield Security PRO: The plugin can block both bot-based and human spam comments helping to reduce the likelihood that malicious (phishing) links are published to your site’s comments.
Preventing malware injections
Preventing phishing content from infiltrating your site is as important as identifying and removing it. Here are some other things you can do to protect your site:
Bad-bot blocking
Many malware injections occur through automated processes such as brute force attacks or vulnerability probing. Shield Security PRO’s silentCAPTCHA bad-bot blocking feature is essential in preventing these programs from running on your site, thereby reducing the risk of malware injections.
Two-Factor Authentication (2FA) and passkeys
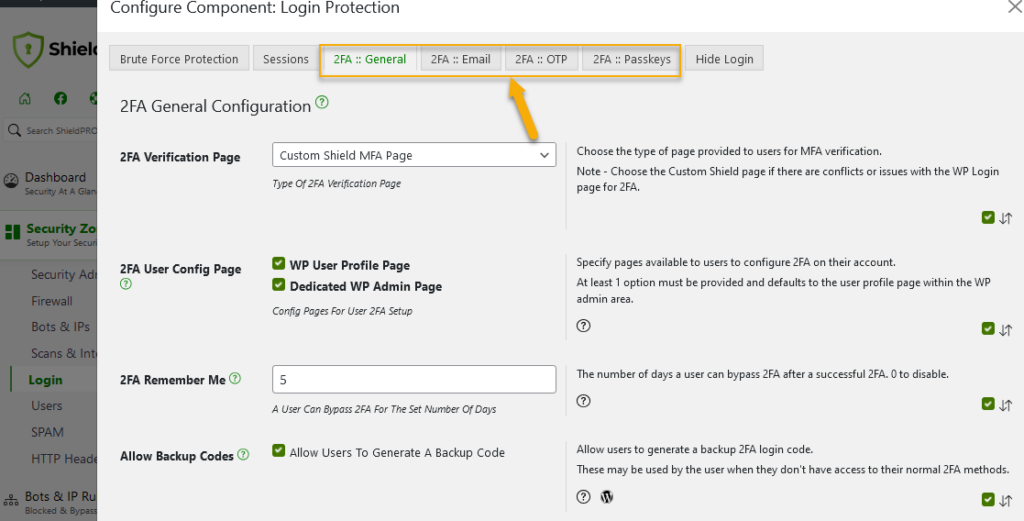
Implementing 2FA and passkeys significantly reduces the risk of unauthorised access to your site. Passkeys, in particular, offer a great security measure against various cyber attacks, including phishing where a user has inadvertently given away their login credentials. (More on this in the next section!)
Some other general preventative measures are:
- Firewalls: Use a firewall to block unauthorised access and malicious traffic (Shield Security PRO provides this).
- Regular updates: Keep your WordPress site, themes, and plugins updated to patch vulnerabilities.
- Activity logs: Regularly review activity logs for suspicious activity or unauthorised access attempts.
How to avoid falling victim to a phishing scam
Phishing scams are a persistent threat that can compromise your WordPress site by deceiving you or your team into granting unauthorised access. To make sure we stay safe online, we need to use 2FA and teach everyone in our organisation how to remain secure.
The Power of 2FA

Two-factor authentication is an important additional security layer for your WordPress site. Paul Goodchild, creator of Shield Security PRO, says, “If 2FA is taken seriously and used religiously by your entire organisation, it’s extremely difficult to fall victim to a phishing scam. If you use passkeys, it’s practically impossible.”
Passkeys require a physical item, often incorporating biometric tools like facial ID and fingerprint scanning, making unauthorised access virtually impossible.
However, certain types of 2FA can still be vulnerable to phishing if used incorrectly. It’s important to make sure everyone in your organisation knows that 2FA codes should never be shared. Train your team to be suspicious of any requests for these codes, in any form.
Proper training and education
Educating your team is essential to preventing phishing scams. Here are some points to cover in your training:
- Recognising legitimate requests: Teach employees to identify legitimate requests for access codes. If they must share these codes, they should verify the requester through additional means, such as a phone call or in-person confirmation. This reduces the risk of falling for phishing attempts where attackers pose as colleagues.
- Spotting fake messages: Phishing attempts often involve fake messages or cloned login pages. Train your team to notice small errors or variations in email addresses and URLs. Encourage them to always approach all requests for login credentials with a high degree of suspicion.
- Securing email passcodes: If your 2FA system uses email-based passcodes, ensure everyone has 2FA set up for their email accounts. This prevents attackers from bypassing your security by targeting less secure points in the communication chain.
Monitoring Activity Logs
Regularly reviewing your site’s activity log can identify suspicious behaviour early. Look for red flags, such as password changes or logins at unusual times compared to the user’s typical activity. Immediate attention can prevent a minor breach from escalating into a major security issue.
Principle of least privilege
Implementing the Principle of Least Privilege is another effective strategy. This means granting users only the access they absolutely need to perform their tasks. By doing this, you minimise the potential damage from successful phishing attempts, as low-level users won’t have access to critical areas of your site.
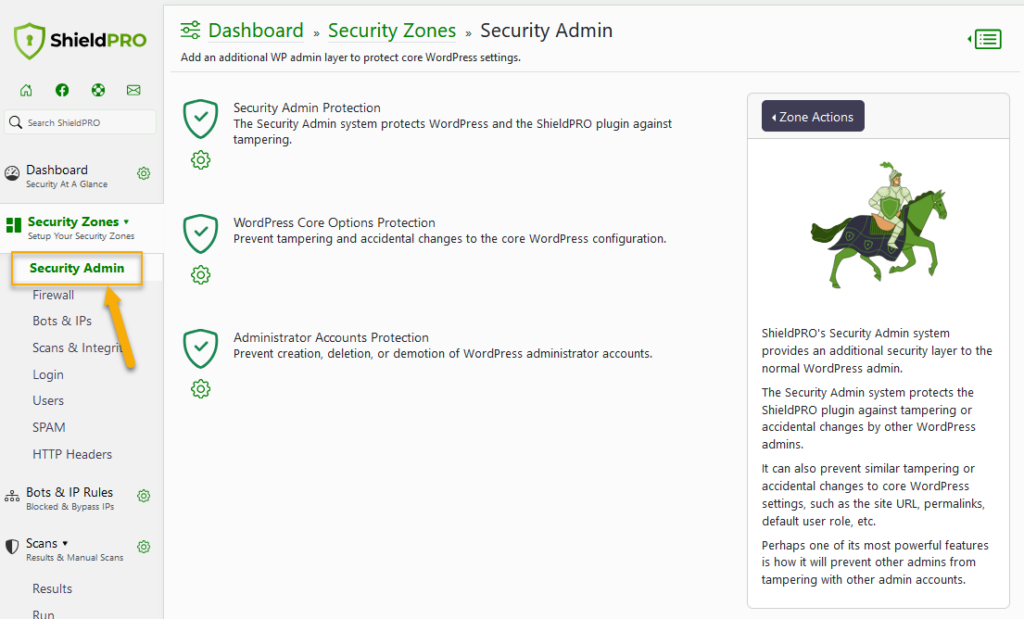
In Shield Security PRO, you can create a super-admin role, ensuring that only trusted and knowledgeable admins can access sensitive WordPress settings. This setting helps maintain tight control over your site’s security.
I think my site has been phished! What should I do?

If you suspect your WordPress site has been phished, or have received a report indicating it, take immediate action.
- Change all passwords immediately, ensuring the new passwords are strong and unique:
- WordPress admin password
- FTP/SFTP password
- Database password
- Associated email accounts
- Enable 2FA wherever possible – and have all staff members do so as well – to add an extra layer of security.
- Update everything:
- WordPress core: Make sure your WordPress installation is up-to-date.
- Plugins and themes: Update all plugins and themes to their latest versions to fix any known vulnerabilities.
- Use Shield Security PRO’s malware plugin to run a thorough scan of your site. Its MAL{ai} uses machine learning to identify and flag malicious files, even those it has never seen before.
- If you have a recent, known clean backup, restoring your site from this backup can ensure all malicious changes are removed.
- Inform your hosting provider about the attack. They can help identify any server-level vulnerabilities and secure your hosting environment.
- If relevant, notify your users of potential compromise. Encourage them to change their passwords and set up 2FA to secure their accounts.
- Apply the best practices discussed earlier, such as regular monitoring, using 2FA, and ensuring all software is updated. This will help prevent future attacks!
Protect your WordPress site from phishing attempts with Shield Security PRO
Phishing threats to WordPress sites come in two primary forms: scams hosted on your site and attempts to gain unauthorised access. Shield Security PRO offers excellent protection against both. Its features include advanced bad-bot blocking to prevent automated attacks, strong 2FA to secure logins, detailed activity logs to monitor suspicious behaviour, and the powerful MAL{ai} for detecting malware.
Shield Security PRO helps you identify and remove hidden phishing content while strengthening your site against future threats. Take proactive measures to secure your WordPress site and get started with Shield Security PRO today!

