Practically every online platform you interact with asks you to create a unique username and password. Sites store this information, and then use it to verify your identity later on. There are several different ways to store sensitive data like this, and the approach a given site takes has a big impact on how secure the data ultimately is.
One of the many techniques that sites employ to secure password data and prevent leaks is called, “password hashing.” But what is ‘password hashing’, anyway?
This comprehensive post aims to demystify the topic, explain some of the strategies WordPress uses to secure your password data, and offer guidance on how to build up more protective layers for your WordPress site.
So, let’s delve deeper into password hashing and WordPress password security. There’s lots to learn!
Password hashing and its place in website security
The best way to understand hashing is to first understand the different ways sites can store sensitive data like login credentials.
Plain text storage
This involves storing the username and password combinations exactly as they are, without any form of disguise or encoding.
However, this method is a massive Achilles’ heel in your database: If hackers get your password list, accounts on your platform become their playground.
Encrypted storage
A slightly improved form of security, this method sends passwords through a two-way, cryptographic key encryption algorithm and stores the transformed versions. These muddled versions of the passwords might seem like a meaningless string of characters, but a key decrypts the string and reveals the original password.
However, this approach still has its vulnerabilities, especially if both the encryption key and passwords reside in the same database system. Once hackers have both, it’s as good as giving them a plaintext version.
Password hashing
Created to address the problems with encryption, password hashing is a method of converting passwords into a unique string of characters. Think of it like blending together paints: The original colors lose their individual identities in the mix, and you can’t separate them back out again.
The beauty of password hashes is that they are stored, not the password. When a user logs in, the user-password combination goes through the same algorithm, generating a hash. This is then compared to the stored hash, allowing the server to verify passwords without storing them at all.
Password hashing offers a security level a notch higher than encryption because there is no key you can use to reverse-engineer the process. However, it is not without its pitfalls.
- One known issue with password hashing is called ‘collision.” This is when a hashing algorithm produces identical character strings for two different passwords. This can cause several issues, including unauthorized access. This is an especially big problem if your random, secure password generates the same hash as, say, “password123”.
- Although hackers can’t decrypt a leaked list of hashed passwords, they can use brute force methods to gradually decipher the list. Brute force bots run several potential passwords through the hashing algorithm to see what hash those passwords produce. If they find a match in your hash list, they now know the password for that user.
However, there are ways to counteract these password vulnerabilities. For example, WordPress mitigates this risk through the use of “salts,” which we’ll dive deeper into later on in this article. Lastly, good password practices, such as using random unique passwords for every site you access, keeps your data far more secure.

Which password hash algorithm does WordPress use?
WordPress uses the PHPass hashing framework to generate its password hashes. This supports several hashing algorithms, including MD5, SHA02, and bcrypt, which each provide a distinct layer of security.
However, this multipronged approach does not guarantee flawless security. For instance, let’s consider known vulnerabilities associated with the MD5 algorithm.
- Collision: One known issue with MD5 is it’s prone to collision. As discussed before, a collision happens when two distinct passwords go through the algorithm and come out with the same hash. This causes a serious cybersecurity risk, since someone could conceivably put the wrong password in and still gain access.
- Rainbow table attacks: Many common MD5 password hashes have already been decoded. This leaves them exposed to something known as ‘Rainbow Table attacks’ – a fast-acting way to crack passwords with the help of precomputed tables filled with plaintext passwords and their corresponding known hash values. These tables help bots quickly match hashed outputs to commonly used passwords.
One of the ways WordPress mitigates these issues is with the inclusion of ‘salts’. Let’s take a closer look at how these work:
Spicing your hash: The role of salt in password hashing
Salts are random data chunks, such as a brief string of numbers, that a website or application attaches to a password before the hashing process begins. They’re linked with your login information and run through the hashing algorithm alongside your password. They’re an elegant way to reduce some of the vulnerabilities associated with hashing.
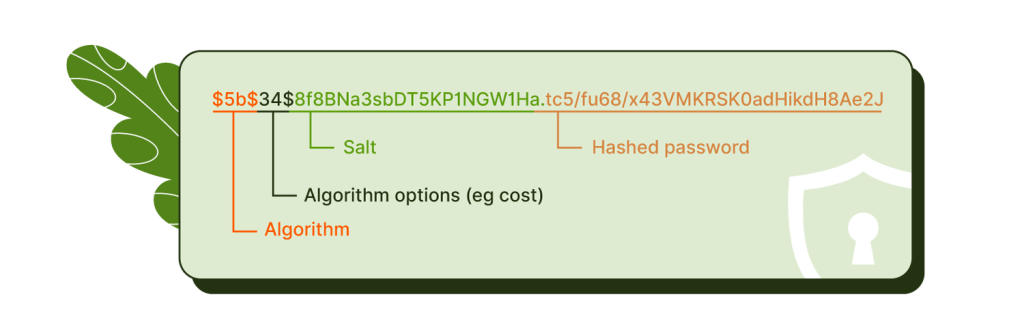
Without salts, identical passwords would generate identical hashes. If your database lands in hackers hands and they crack one common password, they can use the cracked hash to find everyone using the same one. Salts ensure that every single password hash is unique.
Counteracting rainbow table attacks
This guaranteed uniqueness helps to make rainbow table attacks far less effective.
Picture this: A hacker knows the hash for the password ‘password1’. However, they won’t be able to predict the hash for ‘password1 + 826463’, where ‘826463’ signifies the salt.
Once they manage to crack ‘password1 + 826463’, the hash they obtain still won’t match any other instance of ‘password1’ thanks to the mix-up from the salt. This simple step goes a long way to improve password security and protect everyone in the WordPress ecosystem from data leaks.
Although WordPress’s password hashing and salting has laid a great foundation for password security, you can go further to protect yourself and your users.
Enhancing WordPress security measures with Shield Security Pro
If you’re looking to boost your WordPress site security, consider using a plugin like Shield Security Pro. This plugin tackles site security from all sides to ensure that you and your users’ data are protected.

Shield Security PRO’s security measures have been thoughtfully designed to safeguard your site from login hacking attempts.
- The platform encourages users to set minimum password strengths, so your site is a less attractive target for hackers.
- Shield Security PRO reminds users to update their passwords periodically. This increases the chance that, should a user’s password be compromised, the information will soon be outdated.
- It also includes two-factor authentication, where users confirm their identity through a second step in addition to their login credentials. Legitimate users can access a code by email, authenticator apps, or hardware. Even if hackers access valid login information, the credentials are useless without the verification code.
Moreover, Shield Security PRO offers several other features designed to improve security all across your site:
- A bad bot detection system that automatically identifies hacking attempts, stopping them before they can cause harm.
- Regular malware scanning to detect suspicious code on your site early, giving you plenty of time to fix the issue.
- Traffic rate-limiting features to stave off DOS attacks, which can overwhelm your server.
- Custom security reports that keep you informed about your site’s activities, helping you to identify and solve potential issues.
- Solutions to block both bot-generated and human spam comments.
These are just some of the defense features you get with Shield Security PRO.
Shield Security PRO: The ultimate tool in WordPress security
WordPress uses password hashing and salts to protect your passwords and keep its users’ data safe from harm. It’s a strong start for cyber security, and you can improve things even more with a plugin like Shield Security PRO.
Shield Security PRO features a super-effective bad bot detection tool that identifies bots and blocks them from your site before they can cause trouble. In addition, it offers a malware scanning mechanism, which continuously checks your site for any suspicious code. It also features 2FA, vulnerability detection, and many other tools that make your site safer.
Shield Security PRO stands between you and potential security threats, mitigating risks and making it far harder for bad actors to make an impact on your site. The result is a more secure and reliable site for you and your users.Take a major step towards solid WordPress protection and download Shield Security PRO today!



