You’ve just sat down to work on your online business, only to be greeted by a message warning that ‘this account has been suspended’. If you’ve ever faced this frustrating situation, you’re not alone. Website suspensions are more common than you might think, and getting back online is a must, given an average hour of downtime can cost a business over $300,000.
The best approach is not to panic. With a little knowledge and an overview of the suspension process, most cases can be resolved, allowing businesses to resume quickly. In this article, we’ll cover how to identify the cause of your suspension, effectively communicate with your hosting provider, and implement security measures to prevent future incidents.
You’ll also discover how tools like Shield Security PRO can harden your website’s defences and help you avoid suspensions in future. Let’s get to work!
Identifying the reasons behind website suspensions
‘Knowledge is power’, and when dealing with a website suspension, identification should be your first concern. Discover the reason behind the suspension, and you’ll then be able to work on a fix. The most common causes of website suspensions are as follows:
- Hosting prohibited content: Websites can be suspended for hosting prohibited content, such as pornography, hate speech, or illegal substances. Hosting providers enforce strict content policies to maintain a safe and legal environment, and if prohibited content is found, a suspension comes before a warning.
- Engaging in illegal activities: Fraud, hacking, or distributing malware can lead to immediate website suspension. By law, hosting providers have to protect their servers and other users from security threats.
- Administrative errors: Basic admin errors – such as incorrect domain registration or a failure to respond to verification emails – can result in website suspension. These issues are usually resolved by updating the necessary information.
- Missed payments: Missed payments for hosting services are a common reason for a suspension. Hosting providers typically send multiple reminders before suspending any account, and service is usually restored after payment.
- Malware and phishing attacks: Websites infected with malware or used for phishing attacks are often suspended to prevent further damage and protect other users. Site owners must clean the infection and secure their site to regain access.
Examples of real-life suspensions
Here are two examples of websites that were compromised, leading to suspension:
- Pornography violation: A Reddit user shared their experience where their WordPress account was suspended due to a pornography violation. The user had stored intimate videos with their partner in their site’s media library. Although the material could not be accessed by visitors to the site, the suspension occurred without warning.
- Accidental suspension: Another instance involved a blog that was accidentally suspended by WordPress. The platform’s overzealous spam filter shut down the site for 24 hours before the mistake was realised and the problem rectified.
Many hosting providers employ automated systems that detect policy violations or suspicious activity and suspend sites to protect their servers. This can be a major inconvenience for those running a business with an online presence.
Potential problems are best managed proactively, and Shield Security PRO is a comprehensive WordPress plugin designed to protect websites from various threats that can lead to suspensions.
It features malware scanning to detect and remove malicious code, a Web Application Firewall (WAF) to block malicious traffic, and login security to prevent unauthorised access attempts. The plugin also provides real-time alerts and detailed activity logs, allowing site owners to proactively monitor and manage security issues before they escalate.
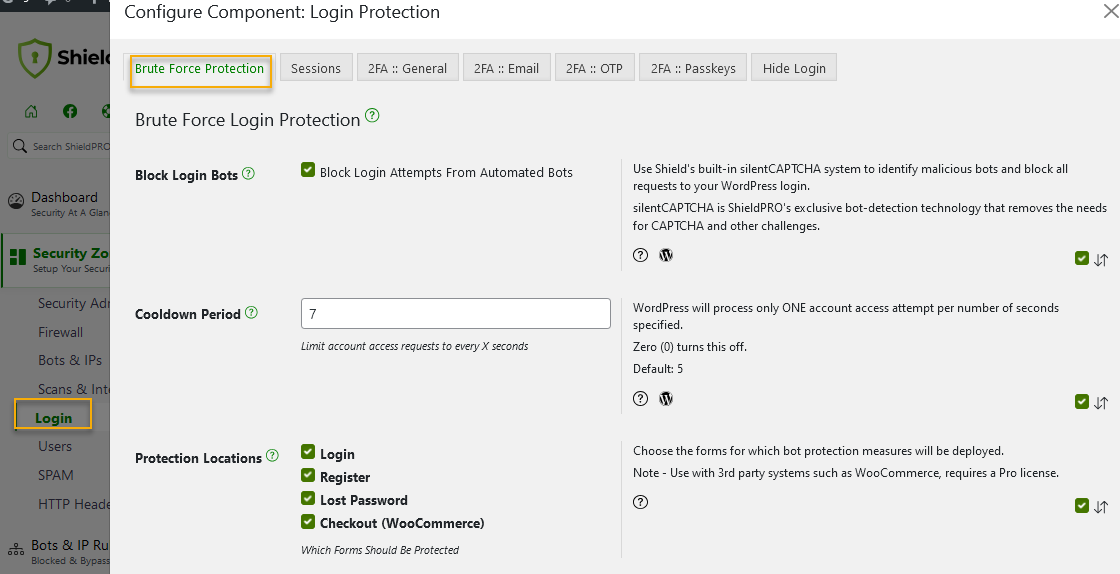
By implementing these measures, Shield Security PRO helps websites remain compliant with hosting policies and hardens sites against incidents that result in suspension.
How is access restricted with website suspension?
As we’ve seen, website suspension is carried out by hosting providers when they detect activity that violates their terms of service or acceptable use policy. When a site is suspended, the hosting provider restricts access to its content in various ways.
Commonly, all web traffic to the suspended site is redirected to a generic suspension notice page stating that the account has been suspended. This prevents the public from accessing any of the site’s pages or content. In some cases, access may be completely blocked and carry no warning, making the site inaccessible.
During a suspension, only the site owner or administrators can access the backend of the site to resolve the issues behind the suspension. Hosting providers achieve this by modifying server configurations to restrict access based on Internet Protocol (IP) or user permissions until the problems are fixed.
Steps to overcome account suspension
Overcoming an account suspension can be stressful and confusing for all site owners, especially those less technically inclined. But fear not! It’s actually a simple process if the following steps are taken:
- Understand the reason for suspension: This information can usually be found in the suspension notice sent by the hosting provider. It could be due to unpaid bills, security breaches, or violations of terms of service. Identifying the root cause will help you address the issue more effectively.
- Contact support: Contact your hosting provider’s support team with your findings so far. Have your account details ready, including the relevant dates of your suspension and the reasons you’ve identified behind your suspension.
- Resolve the issue: Depending on the reason for suspension, resolving the issue might involve removing malware, paying outstanding bills, or removing content that violates the terms of service. Prioritise resolution and ask a technical expert for help if needed.
- Submit an appeal: Some suspensions are due to a mistake. In such cases, a site owner may need to submit an appeal to their host. Include all relevant details in your email or letter, and apologise for any errors on your part. Detail the steps you’ve taken to correct the problem, any improved security measures, and a request for reinstatement of your site.
- Wait for a response: Finally, wait for a review from your hosting provider. A host will verify if you’ve followed the correct steps and either provide further advice or lift the suspension.
Remember, if a suspension is down to a security breach, Shield Security PRO works to prevent such occurrences in the first place. A major inconvenience can be avoided simply by shoring up your website security!
Understanding WP-CLI for site scans during suspension

The WordPress Command Line Interface (WP-CLI) allows users to manage WordPress installations through the command line instead of the traditional web-based admin interface. It provides a range of commands for managing WordPress core, plugins, themes, users, and database operations.
WP-CLI is particularly useful during site suspensions, which are often due to security breaches or malware infections. When a site is suspended, it usually won’t accept Hypertext Transfer Protocol (HTTP) requests, making it inaccessible via the web-based admin interface. However, with WP-CLI, you can still run security scans via the Secure Socket Shell (SSH) to identify issues that led to the suspension.
Many web hosting providers include WP-CLI pre-installed on their servers. If your host does not provide WP-CLI, you can install it manually by following the instructions in WP-CLI’s installation guide.
Once installed, you can use commands like wp core verify-checksums to verify the integrity of WordPress core files and detect any modifications or malware:
| $ wp core verify-checksums Success: WordPress installation verifies against checksums. |
In addition to core commands, certain security plugins like Shield Security PRO support WP-CLI integration. This allows you to control the plugin’s features via the command line, like initiating scans, updating firewall settings, and managing security rules.

With Shield Security PRO installed, you can run a malware scan using the following code:
| $ wp shield scans shield scans run –all |
Using WP-CLI to automate security tasks during a site suspension can significantly speed up the process of identifying and resolving issues. By scripting a sequence of commands to scan for malware, update firewall rules, and verify core files, you can efficiently restore a compromised site.
The role of security in preventing website suspensions
Having excellent security measures on your website reduces the likelihood of malware attacks, phishing, and Distributed Denial-of-Service (DDoS) attempts, all of which can result in website suspension.
Consider the following security considerations for hardening your site’s response:
- Regular updates and patches: Ensure all plugin and theme updates are timely and vulnerabilities patched as soon as possible. Shield Security PRO’s automated updates help to protect against vulnerabilities that can lead to security blips.
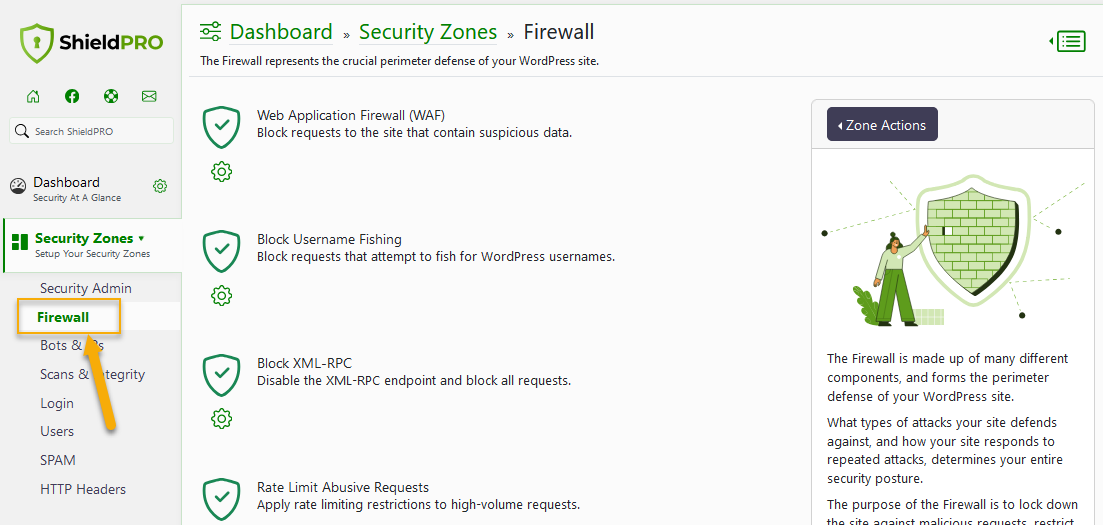
- Web Application Firewall (WAF): A powerful WAF protects websites from common exploits and DDoS attacks. These can overload your server, harming performance and the user experience. An account can be suspended if a site owner fails to deal with these problems. The Shield team recommends pairing Shield Security PRO with CloudFlare for the best WordPress site protection.
- Use a Content Delivery Network (CDN): A CDN improves global load times, absorbs traffic spikes, and manages potential attacks. CDNs help to stabilise your site’s performance, reducing any erratic traffic peaks and troughs that could violate your hosting provider’s policy.
- Conduct security audits: Regular audits and penetration testing can help discover security weaknesses before they can be exploited. Shield Security PRO includes automated file scanning, malware detection, and real-time monitoring to keep a continuous eye on potential security vulnerabilities.
- Regular data backups: Making regular backups and storing these on different servers guards against having your site’s server compromised. It will also make it easier to recover your data in the event of a suspension.
- Disaster recovery plan: Have a recovery plan to deal with and fix future security breaches. Ensure all staff members receive regular training and your plan is well-rehearsed.
Identifying the signs of malware and phishing attacks
Malware is malicious software designed to harm computers, steal data, or gain unauthorised access. It commonly slows performance and is identified by unauthorised changes to files or settings. Naturally, malware can lead to issues that result in suspended accounts, so if your site is experiencing any of these problems, troubleshoot immediately.
Shield Security PRO includes the following malware protection:
- Bad-bot blocking: The plugin includes a system that evaluates all visitor behaviour, watching for “bot signals” that indicate a malicious bot is on your site. Although there’s no single behaviour that proves an IP address is a bot, there are some unmistakable patterns, such as those that point toward brute force attacks or steps intended to probe for vulnerabilities. It then logs and blocks the visitors IP address so they’re unable to continue their malicious attempts.
- Malware scanning: Adaptive malware scanning includes AI-driven detection for PHP malware. This helps identify and remove malicious code that could compromise the site.
- File Locker: The plugin monitors changes to the most important WordPress files, alerting administrators to any unauthorised modifications that could indicate a malware infection.
- Traffic & Activity Monitoring: Full traffic logging and request monitoring help to detect unusual activity that might signify a malware attack. This includes tracking and blocking suspicious IP addresses.
- Automatic updates: Shield Security PRO ensures that security definitions and rules are continuously updated, providing protection against the latest threats.

In contrast, phishing is a scam that tricks people into revealing sensitive information or installing malware through fraudulent emails, websites, or messages. Some unexpected emails can be highly convincing, so look for warning signs such as poor grammar/spelling and mail coming from different links to the sender’s website.
Shield Security PRO can help to prevent such potential problems:
- Two-Factor Authentication (2FA): Shield Security PRO supports multiple 2FA methods, including email-based login codes, Google/Microsoft/LastPass Authenticator, Yubikey, and Universal 2nd Factor (U2F).
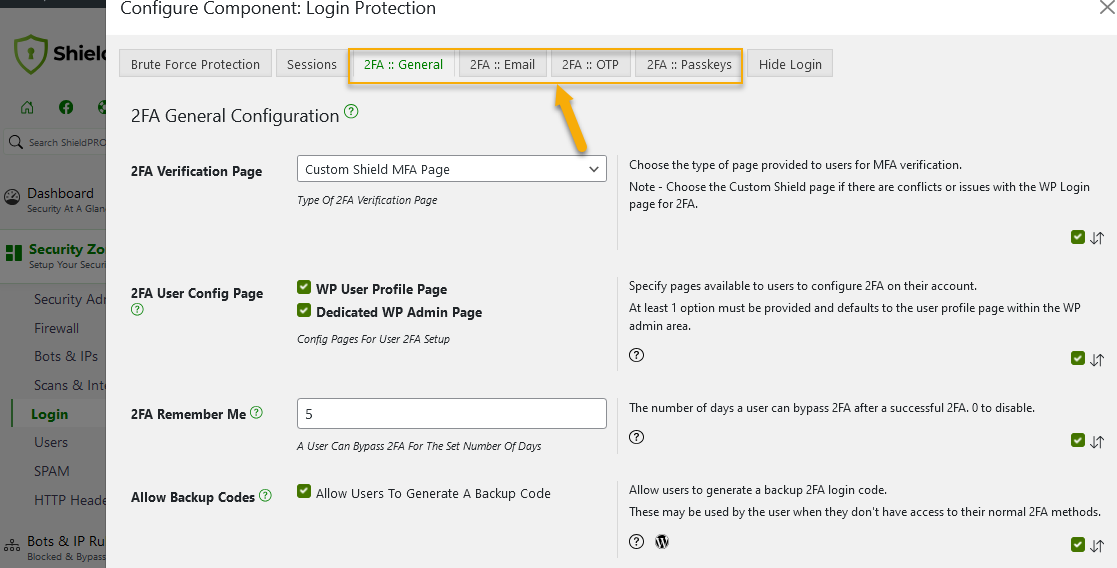
- User enumeration security: This is an attack technique that allows malicious actors to extract information about registered users on a website. Shield Security PRO’s bad-bot blocking and firewall block requests that attempt to enumerate users, and admins can also remove inactive users through manual suspension.
- Login protection: Shield Security PRO includes features to limit login attempts and enforce login cooldowns, reducing the risk of brute force attacks that often accompany phishing attempts.
How to prevent future suspensions with Shield Security PRO
Don’t let website suspensions catch you off guard. By understanding the common causes – from malware infections to terms of service violations – you’re already one step ahead when it comes to preventing future incidents.
Regular website scans are crucial, and Shield Security PRO is your ultimate ally. With its ability to scan WP-CLI even when your site is down, the inconvenience caused by any suspension can be much reduced.
The most secure websites embrace a proactive approach to security rather than reacting to issues as they arise. Having a reliable plugin manages all threats for you, allowing you to focus on strategy and growth, and minimising the chances of having your site suspended.
Take charge of your website’s future and get your security in order! Build a fortified wall around your site by trying Shield Security PRO today.

