It’s easy to discover usernames on a WordPress website – it’s simply a matter of calling the website URL with the ?author=1 query.
Why is this a big deal? Because once a hacker knows the username of a registered user, especially an administrator, they have a far clearer target to attack.
It’s much easier to attempt a brute force attack against user when you know the username. Obviously.
How does the author URL query scan work exactly?
Try it on your site. In your browser window, type in the home page of your WordPress site, and then add this to the end of it: ?author=1
What will happen is, WordPress will see the “author” query and then try and find a username with that ID on the system. If it finds it, it will redirect your URL to the WordPress “homepage” for that author.
And in that URL will be the admin username.
Perhaps your admin username doesn’t have the ID of 1? That makes it harder to find the username, but by no means impossible. To fix this problem, I can write a script that does this:
https://www.icontrolwp.com/?author=1
https://www.icontrolwp.com/?author=2
https://www.icontrolwp.com/?author=3
https://www.icontrolwp.com/?author=4
…
https://www.icontrolwp.com/?author=100
…
And once it finds one that works, I’ve found a valid username. Easy.
What options do you have to prevent this fishing?
Currently, not a lot.
You’ll have heard people say that you should change your WordPress admin username (you can learn more on how to do that here). This is useful since it will also change your administrator user ID. But as you saw in the previous section, this only goes so far and finding your admin username is relatively easy.
Our Shield Security plugin goes 1 step further that other plugins – it will let you block the ?author=1 query altogether!
With the setting in-place, anyone who browses to your website with the ?author query will immediately receive a WordPress error message explaining to them that this action is forbidden.
How to block WordPress author scans today!
The screenshot shows the setting you need to turn on using the Shield Security plugin to prevent WordPress username fishing.
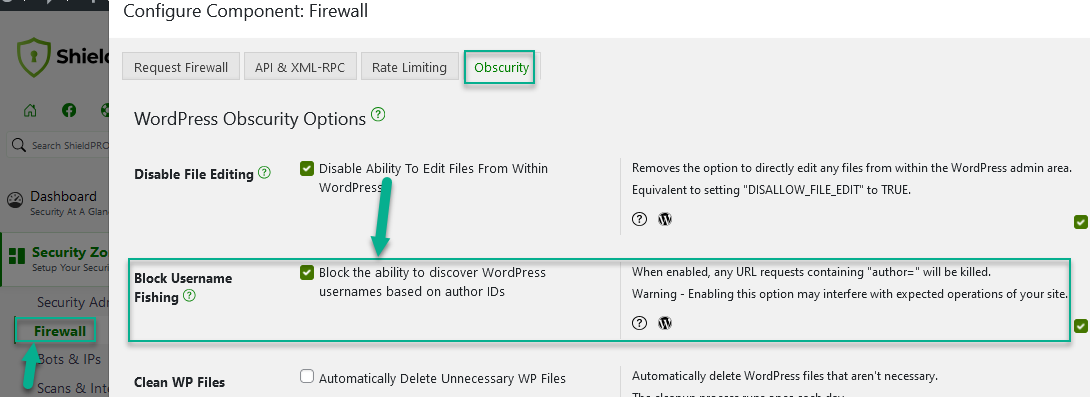
Once this is on under the Firewall Zone, it will affect requests to your site that include the ?author=X parameter.
Please note: this only blocks this URL for non-logged-in visitors. If you are logged in, the URL will work as normal.
The message that will appear to visitors when they’re blocked will be:
The “author” query parameter has been blocked by WordPress Shield Security to protect against user login name fishing.
Learn More.
In this way bots will receive a 503 error and legitimate users will receive an intelligent message outlining what when wrong. They can then contact you if they wish.
Is this a security risk?
It’s not really a security risk that someone knows your username. Far more important than this is that you have a strong password, your site uses SSL and you’re using some form of 2-factor authentication.
Question, Suggestions, or Feedback?
This sort of feature is what separates the Shield Security plugin from other plugins in this space. Rather than make cosmetic changes that are easily circumvented (e.g. change your admin username so your ID is different), we dig a bit deeper and find ways to prevent leakage of critical information that can be used against you.
In this way, it doesn’t matter what your administrator user ID is… no-one will be able to find it in this way.
Please let me know your thoughts and questions below!




Thanks for thinking ahead on this, guys!
great job you guys .. Love this plugin
Thanks for all the science, is very useful
Great post. Good to learn security details. Securing my website ProsnGurus with this tip.
Thank you.
Me gusta mucho esta paguina
[…] Strano come consiglio, eh ?! Eppure è sempre bene cambiare sia il collegamento al pannello di controllo – che in WordPress è di default /wp-admin/ sia nascondere gli utenti. Lo sapevi che aggiungendo ?author=1 al collegamento del tuo sito web, WordPress mostra molti dettagli riguardo gli utenti? […]