Re-using passwords is rarely a good idea, and re-using a password that has been part of a data breach spells trouble.
Luckily for all us WordPress admins, we now have a way to know if our passwords have ever been part of a known data breach. Last year Troy Hunt released a new password look-up service to his brilliant Have I Been Pwned.
The new serves provides an API where anyone can search for whether a password they’ve used in the past has ever been involved in a data security breach. He argues that if it has been, it shouldn’t be re-used.
You may or may not agree with that, that’s for you to decide. We definitely agree with that position and we think all WordPress admins should make a point of ensuring their passwords aren’t pwned.
As such, we’re making it an integral part of our upcoming User Password Policy system inside our Shield Security for WordPress.
What Are ‘Pwned’ Passwords?
If a password has been involved in a data breach and this data is accessible and relevant, it’s part of the ‘pwned passwords’ database.
Troy goes into much more detail here.
The aim of all this is: discourage the use of passwords that have been leaked as part of user account data breaches.
How do you know if a password is pwned? You can use the Pwned Passwords tool right now to look-up your password if you like.
How Does Shield Security Work With Pwned Passwords?
We’re bringing a new Password Policies feature to the Shield WordPress plugin.
As part of this, we’ve integrated automatic look-up in the new ‘pwned passwords’ API v2.
If the option is enabled, at the moment a user sets a password, Shield will look it up on the database for whether or not it’s been pwned.
If it’s there, it’ll return an error for the user and they’ll need to choose another password.
Waait… Does Shield Send The User’s Password To A 3rd Party?
No.
With v2 of this service, Troy has made it really easy to obfuscate the passwords that are being sent to the API.
At no point does Shield either send the password, or even the fully hashed password, to the API.
Sounds Sweet! How can I get access to this?
This integration is a part of the new Password Policy feature.
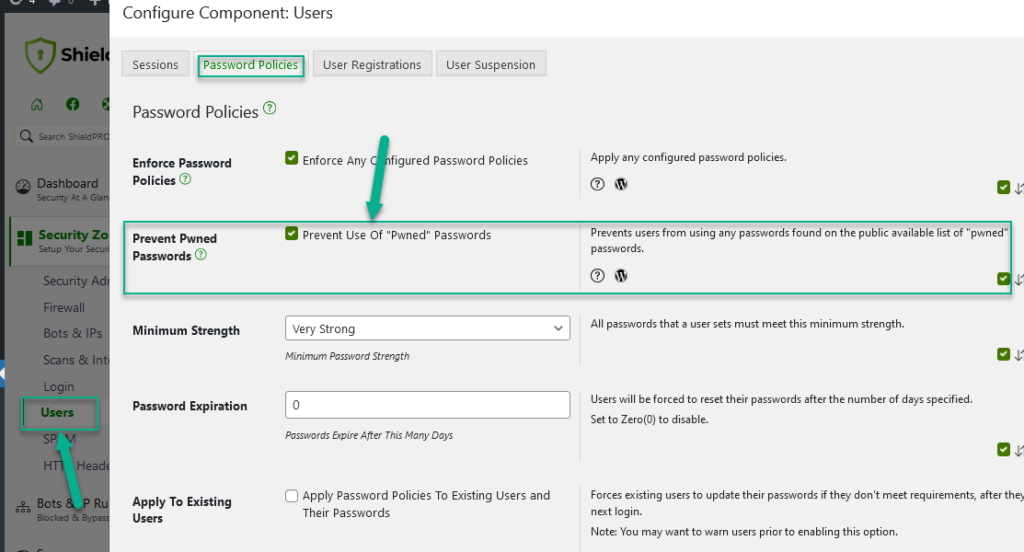
Shield provides you with the following functionality:
- prevent use of ‘pwned passwords’.
- enforce minimum password strength.
- enforce a password expiration.
- apply these policies retrospectively to existing passwords forcing users to update passwords when they login again.
- expire all passwords forcing all users to reset their passwords after they next login.
Feature Requests, Suggestions and Comments
We’re interested to take on any suggestions and feedback you may have.
As always, you can leave comments below and we’ll get back to you.
Note: The Pwned Password lookup feature is a free feature within Shield, reflecting the generously free nature of the API that Troy Hunt has provided. Other password policy settings are Pro-only.



When is this feature coming in? I have been using shield free since 2 years 🙂 I just upgraded to the paid version. It just says I love this plugin! Trust me it’s awesome.