Our need for stronger security grows as technology advances. On average, 30,000 websites are hacked daily – scary, right? Thankfully, thoughtful security practices can protect our sites.
Knowing what is happening on our sites is half the battle. Tracking user login history is an excellent way for WordPress site administrators to tighten security. This approach goes beyond observation; it enables administrators to stay in control, identify unusual activities, and protect their domains from threats.
Monitoring login history will reveal login patterns, helping administrators spot unusual activity and prevent security breaches from unauthorised access attempts. This is especially important in stopping brute-force attacks. Plugins like Shield Security PRO track all login attempts and block suspicious IP addresses automatically, reducing time wasted on manual intervention.
Tracking login history is also crucial for managing internal risks, such as uncovering insider threats, accidental breaches, or intentional misconduct. This is especially useful for websites with many users or membership-based access areas.
In the age of strict data protection laws like the General Data Protection Regulation (GDPR) and Health Insurance Portability and Accountability Act (HIPAA), keeping a detailed user activity record is a must. Shield Security PRO can help you adhere to regulations while improving the security of your whole site!
Illustrating the value of login tracking
Imagine you run a small marketing agency and take pride in your carefully curated team page. One morning, you find the page riddled with typos and unprofessional edits. Obviously, you’ll want to get to the bottom of this.
With login tracking, you can look through your site’s activity logs to pinpoint the timing and location of any unauthorised changes. The trail leads to the ex-staff member – mystery solved!
Although this is a contrived scenario, it demonstrates the importance of monitoring user logins. Without any tracking capabilities, breaches may go unresolved longer, causing further reputational damage. Login monitoring will help you identify and contain threats quickly, remove compromised accounts, and restore website integrity.
Tracking user login history with Shield Security PRO
Shield Security PRO’s Activity Log feature records user login details, including time, IP address, and username. This data helps identify suspicious activities like logins from unfamiliar locations or unusual times, that may point to a compromised account.
Administrators can detect and mitigate unauthorised access by analysing these logs.

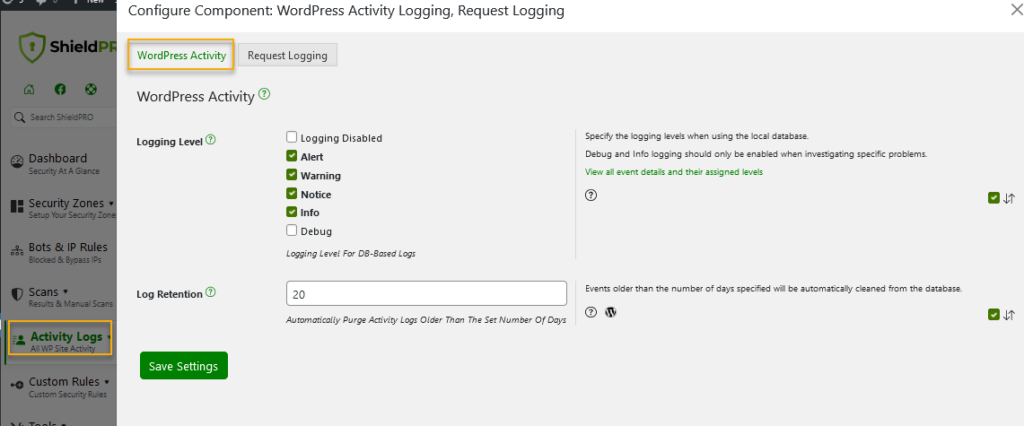
Shield Security PRO’s configuration settings allow site administrators to customise the login history retention duration. The WP Activity Log retains events for seven days by default, but this can be adjusted. To modify these settings:
- Go to the Activity Logs menu
- Press the Configuration.
- In the WordPress Activity tab, specify the logging levels and retention period to ensure login data availability.
Accessing the login history data in Shield Security PRO is easy. Go to the WordPress dashboard → Shield Security PRO → WP Activity Log for a full view of all events, including user logins.
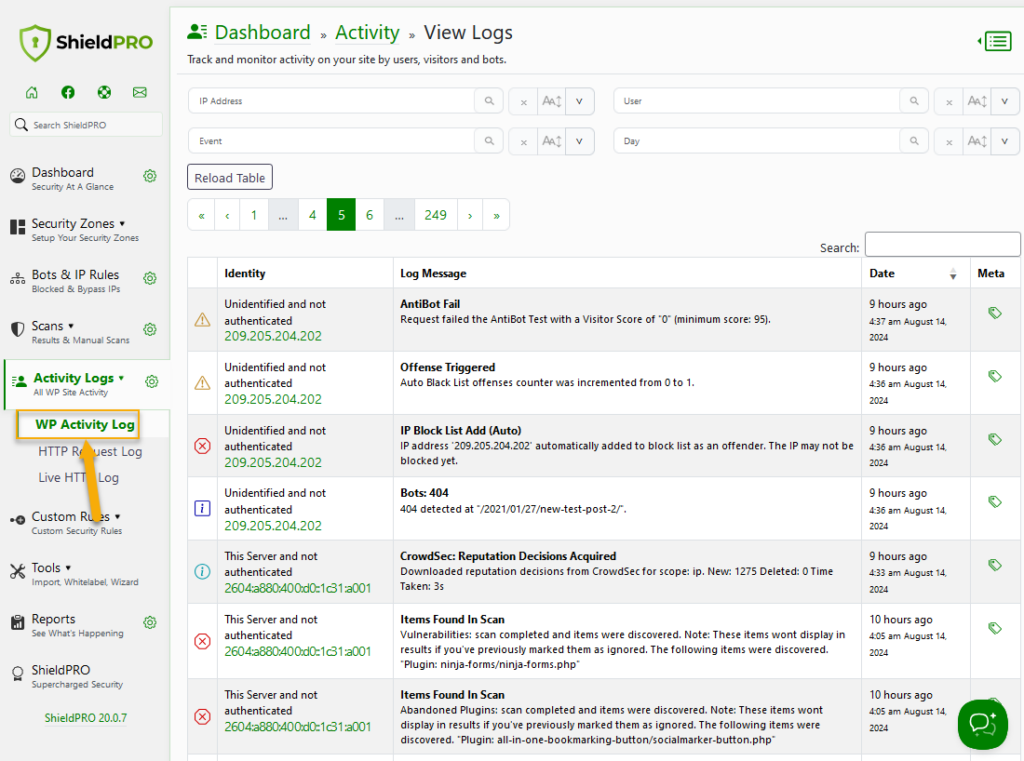
By using the “Event” filter at the top of the Activity Log table, you can easily filter the logs that are displayed to show only what you need. In the example of login history, you could simply search for “login” and it’ll filter for login-related events only.
More tools for in-depth user login tracking
Let’s take a look at additional plugins that provide tracking capabilities for monitoring user activity on WordPress sites.
User Login History
The User Login History plugin is a tool designed to track the login dates and times of users. This plugin captures essential login information, including the IP address, date/time, and user role, providing a view of user access patterns. Some of its features include:
- IP address control: This function monitors IP addresses to prevent unauthorised access attempts.
- Login time tracker: Records the exact time of user logins and logouts, offering precise activity tracking.
- Email alert: Sends real-time alert email notifications to administrators for specific events, such as unusual login activities.
- Track specific roles: This is especially beneficial for sites with multiple user roles, as it allows admins to focus on monitoring high-risk roles more closely.
The plugin is available in both free and pro versions. The pro version offers advanced reporting capabilities, such as detailed login reports and the ability to export data for further analysis. These features can be particularly useful for site owners who need to create timesheets or monitor user activity more closely.
Simple History
Simple History is a free plugin that offers a complete record of actions performed on a WordPress site, including user logins. Its easy-to-use interface presents a timeline of activities, allowing for effortless monitoring of user actions and timestamps. Features include:
- Activity logging: Tracks a wide range of activities, such as post/page edits, comment changes, and user logins/logouts.
- Integration: Supports integration with popular plugins like Jetpack, Advanced Custom Fields, and Beaver Builder, extending its tracking capabilities.
- Suspicious behaviour detection: Helps detect suspicious behaviour by monitoring changes in content, widgets, and user details.
- Retention policy: This feature allows administrators to configure the retention period of logs, ensuring that data is kept for as long as needed.
Simple History is useful for administrators who need to monitor user activity, changes to site settings, or potential security threats like repeated failed login attempts. The plugin’s ability to integrate with other tools and its detailed logging make it a valuable addition to any WordPress site.
Problem detected: What to do when you spot unusual login activity
When monitoring user login activity, spotting unusual patterns is a clear sign that your site’s security could be at risk. It’s important to take immediate and appropriate actions to address any concerns.
Upon noticing unusual login activity, the first steps you should take are:
- Change passwords: Immediately change the passwords for all administrator accounts and any other compromised accounts. Ensure that the new passwords are strong and unique.
- Check user roles: Review the roles and permissions of all users to ensure that no unauthorised changes have been made. Remove any suspicious accounts or downgrade their permissions if necessary.
- Review recent changes: Examine recent changes to your site, including new posts, pages, and installed plugins, to identify any unauthorised modifications.
Shield Security PRO offers a suite of features to help you respond to and investigate unusual login activity. These include:
- Instant alert notifications: Shield Security PRO can send real-time alerts via email or Short Message Service (SMS) when suspicious login activity is detected. This allows you to take immediate action.
- IP blocking: The plugin can automatically block IP addresses that exhibit suspicious behaviour, such as multiple failed login attempts or logins from unusual locations.
- Activity log: Use the activity log to track back to the source of the suspicious activity. This log includes details such as IP addresses, login times, and user roles.

All threats are different. To determine the severity of the threat, analyse the login patterns by:
- IP locations: Check if the logins come from unfamiliar or high-risk locations.
- Times of access: Look for logins at unusual times, which could indicate unauthorised access.
- Frequency of attempts: Multiple failed login attempts in a short period can be a sign of a brute force attack.
💀 Pro tip: If a serious threat is detected, use Shield Security PRO’s lockdown features to restrict access to your site temporarily. This can prevent further unauthorised access while you investigate and resolve the issue.
If legitimate user accounts have been compromised or security protocols affect their access, communicate with your users promptly. Inform them of the situation, advise them to change their passwords, and provide guidance on how to secure their accounts.
After the incident, conduct a thorough post-incident analysis to understand how the breach occurred and how to prevent similar incidents in the future. This should include:
- Reviewing security settings: Check and update Shield Security PRO’s security settings to ensure optimal protection.
- Examining logs: Analyse the activity logs to identify any patterns or vulnerabilities that were exploited.
Address any potential legal and compliance issues that may arise from a security breach. This includes reporting obligations under data protection regulations such as GDPR. Ensure that you document the incident and the steps taken to mitigate it.
To enhance security post-incident, consider:
- Enabling Two-Factor Authentication (2FA).
- Using Shield Security PRO’s AI-powered malware scanning to detect and remove any malicious code.
- Keeping your WordPress core, themes, and plugins up to date to protect against known vulnerabilities.
Optimise your WordPress security today with Shield Security PRO
Protecting your WordPress site against security threats is essential, and with Shield Security PRO, you’ll have peace of mind knowing that your site is protected against many WordPress threats.
By tracking user login history, Shield Security PRO enables quick detection and mitigation of illegitimate logins and suspicious activity, boosting your site’s defences from both external and internal threats. Shield Security PRO also offers a number of additional features, including bad bot detection and blocking, 2FA and password policy enforcement, and login attempt limits, further ensuring secure site access.
Optimise your WordPress security by getting started with Shield Security PRO today!



