Malware for WordPress is a hot topic today. And for good reason.
So with Shield Security Pro v8.0 we’re bringing you a brand new Malware scanner.
The scanner will examine PHP files on your WordPress sites, looking for code patterns that are commonly associated with Malware.
It’ll tell you about any malware files it finds, allow you to download the infected files to examine, and then you can repair it or delete it. You’ll have full and complete control over what happens.
There’s even an automatic repair feature so you can have Shield remove malware from your site without your intervention.
What Does Shield’s WordPress Malware Scanner Do?
First of all we need to understand what Malware is, exactly.
With respect to WordPress, Malware is a generic term used to describe malicious code on a WordPress site that has been put there by an intruder, specifically for the purposes of causing harm.
That definition may sound a little generalised, and that’s because it needs to be. The term ‘Malware’ is all-encompassing and used to describe all sorts of malicious code on your WordPress sites.
And “malicious” can mean practically anything that’s “bad”, from phishing, SEO spam, unauthorized redirects… anything goes.
And so, Malware is, by its very nature, changeable and always evolving.
But, thankfully, no matterwhat any particular piece of malware does, they have certain characteristics and perform actions that most “normal” code has no business executing.
So Shield’s malware scanner is designed to search for these common characteristics, or “patterns”, if you like.
And this is exactly what it will do. Shield Pro scans all your PHP files looking for these common malware patterns and when it finds a file containing one of them, it will alert you.
And half the battle is even being aware that you have malware on your site…
The Advantages and Disadvantages of using Malware Patterns
Patterns are just that – they represents the ways in which code might look, if it were Malware.
This means that the scanner can identify and alert you to as-yet undiscovered, or highly customised malware code.
But it may also alert you to files that are perfectly legitimate, but that contain code that “looks” like malware, but that isn’t. These are known as “false positives”.
A false positive is where a scanner falsely flags an item as being positive for malware, but it’s actually legitimate.
This happens all the time in the never-ending quest for security. Take email SPAM, as a perfect example. We’ve come to accept that the downside associated with the few false positives we get is greatly outweighed by the early detection of malware.
So patterns are powerful ways to identify malware code in whatever form, even those that nobody has seen before. But it comes with the disadvantage of potentially flagging false positives.
But don’t worry, we have made it simple to manage false-positives.
How To Handle False Positive Malware Detection in Shield Pro
All Shield Security scanners let you directly handle scan results in-situ, there and then.
Shield’s WordPress Malware scanner is absolutely no different.
For every file flagged as potential malware, you’ll be presented with 3 options:
- Ignore
- Repair / Delete
- Download
In order to determine whether a file actually contains malware, you’ll need to examine it first.
To do this, simple download the file using the Download link. This will immediately download the file to your computer. Don’t worry, if this is a PHP file, your computer is completely safe if you simply open it in a text editor, like Notepad++.
You’ll want to examine the file and ensure it’s safe. If you’re unsure, there are plenty of communities online that will assist in determining whether a file contains malware. If you’re really unsure, reach out to our support team for further guidance.
Assuming you’ve verified that the file is legitimate, you can simply click Ignore, and the file will not be presented to again (unless its content changes).
And that’s how easy it is to deal with any false positives that arise.
How Shield Reduces False Positives
False positives can be alarming, so the fewer we get, the better. In order to help reduce their occurrence we have a few tricks to help us.
As you’ll see below, there are a few special cases when files are discovered in certain areas of the site. In particular, these are WordPress core files, and WordPress.org plugins.
If a file is falsely flagged as matching a malware pattern and it’s a WordPress core file, or it’s a file in a plugin installed from WordPress, we verify the contents are legitimate.
We do this by simply automatically downloading the original files and comparing them with what is on your site. If the contents match, then we can be confident that this is a false positive and so this file wont make it into your scanner results.
Of course, this has 1 drawback. And it’s where a WordPress.org plugin has itself been compromised and there is malware present in the official release.
There is also 1 other restriction in this system. The WordPress.org plugin repository uses SVN, and they recommend that developers release their plugins using SVN Tags. Unfortunately, there are quite a few developers who don’t use this practice, which is a pity. For technical reasons, this makes it impossible to reliably determine the exact status and contents of files in a given release.
In this case, Shield flags the file as having potential malware (as it’s can’t verify it one way or another) and doesn’t offer a ‘Repair’ option. This is unavoidable.
How Shield Repairs Malware Files
How Shield can repair a malware file, and whether or not this is supported, depends on the file that is discovered.
Here are the potential scenarios:
Scenario 1: File is a WordPress Core file
If the file is a WordPress Core file that is shipped with your particular version of WordPress, Shield can repair the file by simply replacing it with the original file as taken from WordPress.org.
Scenario 2: File is a not a WordPress Core file but is in a core directory
This scenario is covered by the WordPress Core File scanner already in Shield Security. In this case, the simplest action here is to delete the file.
Scenario 3: File is a plugin file
If the file is shipped with your particular version of the installed plugin, Shield can repair the file by replacing it with the original.
This is only possible for plugins installed from WordPress.org.
Also, the following important conditions must be met before a plugin file can be repaired:
- As already mentioned, the plugin is from WordPress.org
- There are no updates for that plugin available
- The developer uses SVN Tags to publish releases. Unfortunately, it’s common for developers to not use SVN tags, but catering for this scenario is impossible and so automatic repair is not available. In these cases, you’ll not be able to “Repair” and you’ll only see “Delete” as the option.
Scenario 4: File is not a plugin file but is in a plugin directory
Here, the file found is in a plugin folder, but is not shipped with the version of the plugin that’s installed. Just like scenario #2 above, the simplest action here is to delete the file.
Again, this is only possible for plugins installed from WordPress.org.
Note: This also applies to the theme files.
Scenario 5: All other files
In this case, as mentioned above with false positives, you will need to manually examine the file and click the link to “Delete” the file if necessary.
How Automatic Malware Repair Works
Now that we’ve covered what the repair options are, let’s explore how the automatic repair feature work with Shield?
When you look at the Shield options, you’ll see there are currently 3 options to automatically repair files with malware:
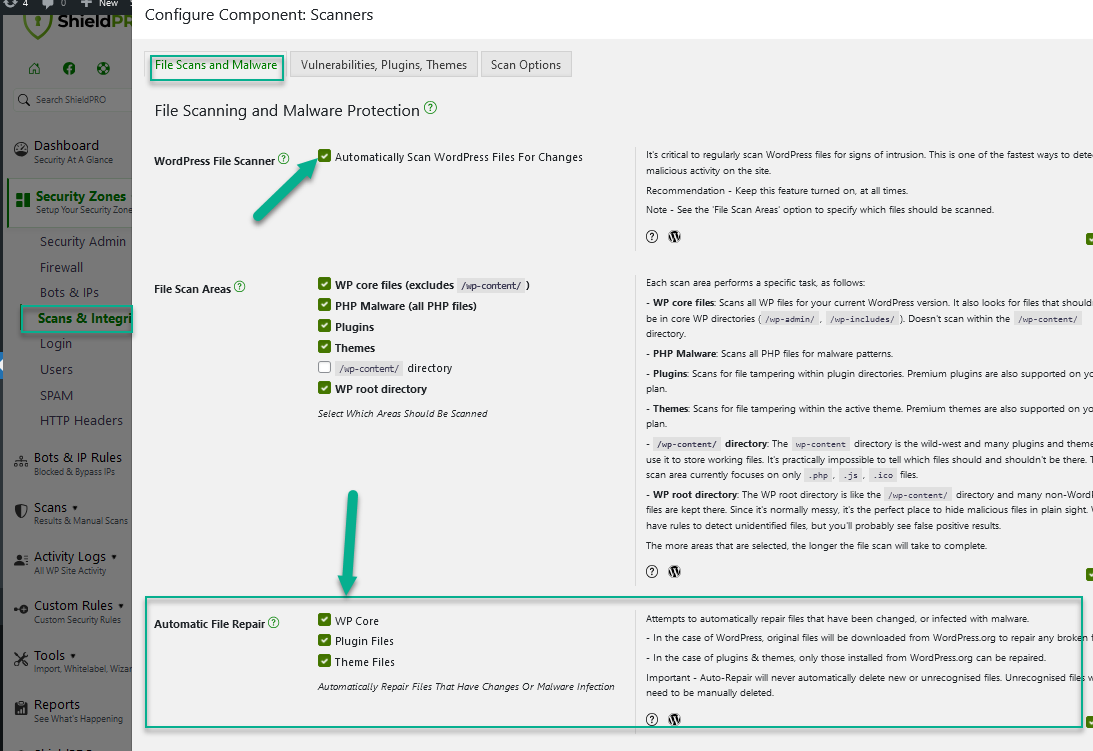
- Automatically Repair WP Core Files
- Automatically Repair WP Plugin Files
- Automatically Repair WP Theme Files
You’ll see how these 3 options reflect scenarios 1-4 above.
This is because in order to be able to repair or delete a file, Shield needs to know whether a file is legitimate and where to find the original source file.
So if you enable option #1, you’re letting Shield automatically handle Scenarios 1&2 above. Enabling option #2, lets Shield automatically handle Scenarios 3&4 etc.
The Future Of Shield’s Malware Scanner
The Malware scanner that ships with Shield 8.0 is just our first iteration of this solution. We have many more plans for this.
Currently the scanner is configured in the following ways:
- it scans every file with the extensions
php,php5,php7, andphtml. - scanning starts at the WordPress ABSPATH and recursively goes into every directory.
ABSPATHis the directory where yourwp-settings.phpfile is found.
Some of the ways we plan to build upon the malware scanner include:
- crowd-sources file whitelisting: this is where we will be able to report confidence levels to you of the percentage of admins that have reported files as either malware or false-positives. This will help you in deciding how to handle detected files.
- scanning for more than just PHP code
- scanning inside posts/pages
- detected malware reports so you can see details on why a file has been flagged for malware
How To Get Shield’s Malware Scanner
Shield’s new Malware scanner is Pro-only feature and you can get it on any site after it’s been upgraded to Shield Pro.
The feature is available from Shield Security Pro 8.0 and above.



