DDoS attacks attempt to overwhelm a website with unwanted traffic for malicious reasons. As you can imagine, they can be a real headache for website owners. These attacks can disrupt your website or even shut it down completely.
With WordPress powering over 43.1% of all websites, it’s no surprise that it’s a prime target for these kinds of cyber threats. But don’t worry; creating a DDoS protection strategy can significantly minimize your site’s vulnerability.
In this article, you will learn all about DDoS attacks – their causes, their impact on your business, and effective strategies to prevent them.
Understanding DDoS attacks on WordPress sites
In web hosting, a server is a physical computer or software system that stores your website’s files and content. It ‘serves’ this content to your site visitors when they request it.
Whenever someone visits your website, their browser sends a request to your server. This request might be for a webpage, an image, a video, or any other piece of content that’s part of your website. Each click or interaction on the website could potentially send multiple requests to the server.
For your website to function smoothly and provide a good user experience, your server has to:
- Respond to these requests quickly.
- Handle multiple requests at the same time, especially if many users are accessing the website at the same time.
- Prioritize and process critical requests (like database queries) in a timely manner.
- Have mechanisms to deal with errors or high traffic volumes without crashing.
If the server is slow or fails to manage requests properly, users might experience delays, errors, or other issues when trying to navigate your website. This can frustrate users and deter them from revisiting.
On the other hand, a server that efficiently manages requests keeps the website accessible and responsive, providing a seamless experience for its users.
This is where the DDoS attacks pose a formidable threat to your website.
DDoS is a cyberattack aimed at overwhelming your website and its infrastructure. Attackers flood the server with excessive requests, causing your site to slow down significantly, crash, or become unresponsive, thereby denying service to genuine users.
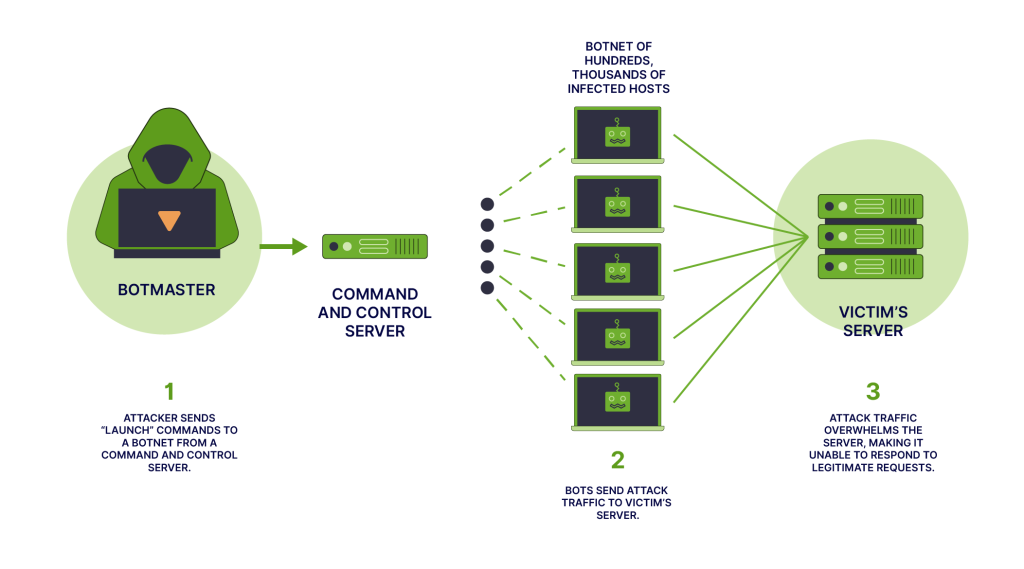
The attack is distributed, meaning it originates from multiple sources. This makes it difficult to stop the attack simply by blocking a single IP address, and it makes it hard to distinguish legitimate user traffic from attack traffic.
The motivations driving DDoS attackers can include:
- Reputational attack: The business world is competitive, with some companies resorting to hiring attackers to launch DDoS attacks on their competitors’ websites, tarnishing their online reputation.
- Ransom collection: Malicious hackers may hold your website hostage, demanding payment to stop the attack and restore your site’s functionality.
- Political motivation: Ideologically motivated attackers might target organizations or businesses that oppose their views, using DDoS attacks to protest.
- Random chaos: In some cases, DDoS attacks are launched simply for causing chaos or for bragging rights within hacker communities.
WordPress sites are prime targets for DDoS attacks due to the unfortunate tendency of some users to leave their website vulnerable by overlooking critical security measures – which is why it is so important to regularly check your site’s security posture.
A diverse range of DDoS attack methods exists, each exploiting different vulnerabilities. Here are some common approaches:
- Ping of death: Attackers send multiple malformed ping requests to the server. These altered pings are designed to consume excessive server resources and overwhelming capacity.
- UDP/HTML flood: This attack targets the User Datagram Protocol packets and HTML code. Attackers send a stream of blank app requests and HTML requests to the server, flooding random ports.
- Slowloris: This stealthy attack focuses on a specific site on a server without impacting other hosted resources. It sends several incomplete HTML requests to the server, leaving them open for as long as possible.
Recognizing a DDoS attack in progress is crucial for timely intervention. Some signs include:
- Sudden spikes in traffic: This is particularly suspicious if it’s on an unusual page or at an odd time.
- Slow-loading web pages: Visitors may encounter 504 (gateway timeout) errors.
- A sudden wave of requests: A sudden influx of requests targeted at a specific page or resource.
- An influx of form submissions: Abnormally high form submissions, often unrelated to genuine user activity.
- Slow or non-loading files: Website files, including images and scripts, load slowly or not at all.
- Complete website crash: In the most severe cases, a DDoS attack can bring your website to a standstill.
- Ransom notes: In some scenarios, attackers may leave ransom notes to extort money from site owners.
To effectively combat DDoS attacks, early intervention will help to limit the overall damage to the site.

The impact of DDoS attacks on your business
DDoS attacks can have immediate and long-term impacts on your business, extending beyond the temporary disruption they cause. Here’s a closer look at the consequences:
Immediate impacts:
- Lost revenue: You can lose potential sales, leads, and income that would have been generated during that period. Downtime is particularly detrimental for e-commerce businesses, as they miss out on valuable sales opportunities.
- Damage to your site’s reputation
- Increased security risk: When your systems are overwhelmed dealing with the attack, attackers might exploit vulnerabilities elsewhere. This can expose your website and sensitive data, putting your business at a higher security risk.
- Legal liability: Being unprepared for DDoS attacks can lead to legal and financial consequences. This can include compensation claims from customers who experienced losses due to your site’s unavailability during the attack.
- SEO issues: DDoS attacks can harm your site’s search engine optimization (SEO). Search engines like Google prioritize websites that offer a smooth and reliable user experience. When your site is under attack, its performance can suffer, leading to lower search engine rankings.
Long-term impacts:
- Loss of customer trust: Frequent disruptions and outages on your website may lead customers to seek more reliable alternatives and lose loyalty.
- Financial repercussions: DDoS attacks have financial repercussions beyond immediate revenue loss and can strain your security budget, along with legal and liability consequences.
- Business continuity challenges: Frequent DDoS attacks disrupt online operations, impacting productivity and customer satisfaction and leading to missed opportunities.
- Damage to brand image: Over time, DDoS attacks can significantly damage your brand’s image. Your business may be perceived as an attractive target for attackers, further undermining your reputation and attracting unwanted attention.
Given these consequences, investing in robust security solutions and an aggressive security strategy is essential to protect your business from the disruptive and damaging effects of DDoS attacks.
Key techniques to prevent DDoS attacks
Preventing DDoS attacks is critical to maintaining your WordPress site’s availability and security. Several key techniques can help you defend against these disruptive threats:
- Firewalls: Firewalls are crucial in preventing older forms of DDoS attacks. They act as a barrier between your site and incoming traffic, allowing you to filter out potentially malicious requests. However, a more thorough security approach is required for requests that arrive via HTML to combat DDoS attacks effectively.
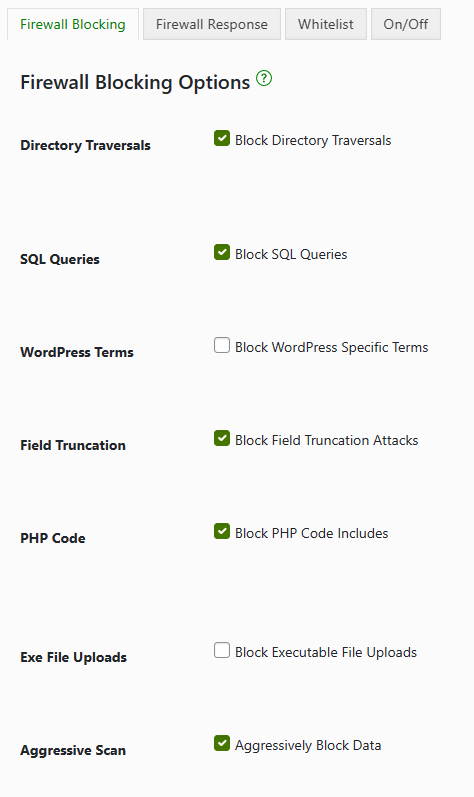
- Rate response limiters: Rate response limiters automatically block IP addresses that exhibit suspicious or abnormal behavior. These limiters can protect your site from DDoS attacks by identifying and isolating potentially harmful sources.
- Know your traffic patterns: Understanding your website’s typical traffic patterns is critical for recognizing and responding to abnormal activity that may indicate a DDoS attack. By identifying unusual spikes in traffic or requests, you can take swift action to mitigate potential threats.
Protecting your site with a reverse proxy
One of the best and most effective measures you can take to protect your site from a DDoS attack is by using a reverse proxy server. This is a server that sits behind your firewall and works as something of a bouncer, triaging requests and forwarding them to your site’s webservers.
There are several advantages to using a reverse proxy, one of which being that it’s a fantastic DDoS prevention tool. With the reverse proxy in place, there’s no way for users to access your site servers directly. Instead, the DDoS attack requests only go to the proxy server. Since most proxy servers are set up with caching enabled, they don’t have to send every request for the same URL back to the actual webservers.
This means that, although a DDoS attack may demand extra resources from the proxy server, it won’t increase load on your website servers themselves. Moreover, if you use a service like CloudFlare (which we wholeheartedly recommend) to act as your reverse proxy, you can trust that they’re well-equipped to handle this demand. Proxy servers should, by design, have extra security and plenty of resources to fend off DDoS attacks. Keep this in mind if you opt to set up your own reverse proxy rather than using an established service.
Shield Security: A multi-layered defense against cyber attacks
Shield Security PRO offers a complete WordPress security solution designed to protect your site from various security threats. Its primary defense mechanism is the AntiBot Detection Engine, or ADE. This detects malicious bots and blocks their IP addresses before they can start causing trouble. Although this is a great defense for non-distributed Denial of Service (DoS) attacks, it’s not enough to prevent DDoS attacks on its own.
DoS vs DDoS: Adapting your defenses for different attacks
Not sure about the difference between DoS attacks and DDoS attacks? Simply put, DoS attacks flood your site with requests from a single source, while DDoS attacks flood your site with requests from multiple sources.
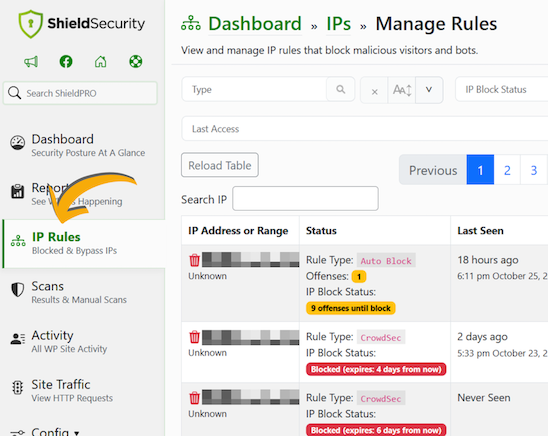
DoS attacks are bot-powered and come from a single IP address, so Shield’s bad bot blocking features can stop these attacks in their tracks. Since Shield blocks IP addresses on a one-by-one basis, it isn’t effective against DDoS attacks, which, by their nature, can come from 1000s of different IP addresses at once.
Still, Shield Security PRO includes several features that, alongside measures such as a reverse proxy server, can help you fortify your site against DDoS attacks:
- Firewall: Shield Security PRO includes a firewall that blocks malicious requests, helping prevent DDoS attacks from compromising your site’s availability.
- Traffic rate limiting: This feature enables you to stop DDoS attacks in their tracks by restricting the rate of incoming traffic. By controlling the flow of requests, you can thwart attackers’ efforts.
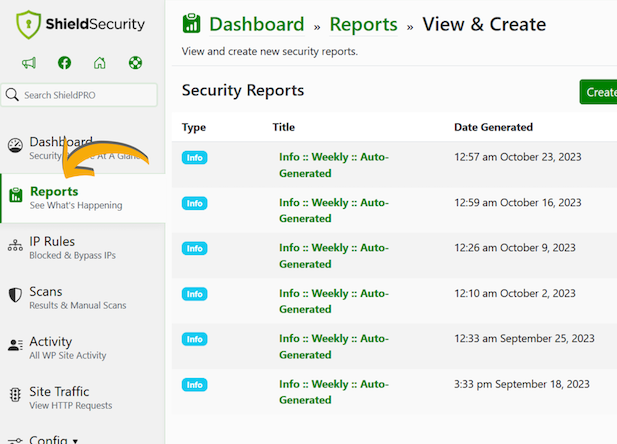
- Regular activity reports: Shield Security PRO provides daily activity reports so you can understand your site’s traffic patterns.
- Vulnerability scanner: The vulnerability scanner in Shield Security PRO helps you identify potential weaknesses attackers may exploit during a DDoS attack.
Shield Security PRO’s comprehensive and user-friendly features go far to protect your site from DDoS attacks and other cyber threats.
Best practices for WordPress security beyond DDoS protection
When it comes to cybersecurity, you need a strategy that will fortify your site from every angle. Here are some best practices:
- Strengthen your login security: Enhance login security with increased password strength, regular password resets, and two-factor authentication (2FA).
- Malware scanning: Regular malware scans help keep your website secure. Implement a robust scanning solution to maintain a clean site.
- Keep your software updated: Outdated software, whether it’s the core WordPress files or added plugins, poses a significant security risk. Regularly update your WordPress installation and all associated plugins to patch vulnerabilities and maintain site integrity.
- Remove unused plugins: Every plugin installed on your WordPress site can be a potential vulnerability. Periodically review your plugins and delete any that are no longer necessary.
- Site audit: Conducting a site audit is a proactive way to identify and address vulnerabilities. It involves reviewing your site’s code, configurations, and settings. You can strengthen your site’s defenses by finding and fixing security weaknesses.
- Using Shield Security PRO: Simplify your security efforts using a dedicated security plugin like Shield Security PRO. This all-in-one tool streamlines your WordPress site’s overall protection.
By following these best practices, you can minimize the risk of security breaches and ensure that your website remains resilient in the face of cybersecurity threats.

Creating a sturdy incident response and recovery plan with Shield Security PRO
You can become the target of a DDoS attack at any time, but you can be ready for it. With a plan and good preparation, you can rest assured that you can handle any security issues that arise. Here are the key steps for creating a DDoS response plan:
- Preparation
Prepare your site for possible DDoS attacks using Shield Security PRO and reverse proxy services such as CloudFlare, to provide rate limiting and set up firewalls. These proactive defenses will help mitigate the impact of an attack.
- Detection
Monitor web traffic and activity. Act quickly if you notice suspicious signs like sudden spikes in request volumes, performance degradation, or site outages. Early detection is essential to minimize damage.
- Containment and eradication
In the event of a DDoS attack, immediate action is imperative. For example, you may need to contact your Internet Service Provider (ISP) for help blocking the IP addresses involved in the attack. You can also use Shield’s Full Site Lockdown feature to help conserve resources.
- Recovery
Once you’ve come out the other side of an attack, run a site audit to ensure everything is as you expect. This step is critical to ensure your website hasn’t been compromised during the attack.
- Communication
Contact your customers or employees to let them know the situation has been resolved. Effective communication can help mitigate potential concerns or confusion.
- Post-mortem
Conduct a post-mortem analysis after the attack by reviewing and identifying vulnerabilities. This can help you learn to better detect and respond to future attacks.
Incorporating Shield Security PRO into your DDoS response and recovery plan means you have a powerful ally in mitigating attacks, identifying vulnerabilities, and improving your overall security. This proactive approach empowers you to defend your WordPress site effectively and respond swiftly to potential threats.
Choosing Shield Security PRO: The right DDoS protection solution for WordPress sites
DDoS attacks threaten your website’s stability, motivating you to take appropriate security measures. Following these best cybersecurity practices, you can reduce the likelihood of DDoS attacks and recover quickly should an attack occur.
Shield Security PRO’s features, proactive monitoring, and rapid response capabilities make it an indispensable tool for mitigating threats online.
Install Shield Security PRO on your WordPress website today, and enjoy the peace of mind that comes with knowing your site is in safe hands!

